To connect to the DAY 0 GUI, login to the defined Device Management interface via https and then the IP address of the management which you configured To know how to configure it please visit the Day 0 Configuration of WLC. In this blog we will know about WLC basic GUI Configuration (C9800). To login […]
Mostbet Brasil: Site Oficial, Inscrição, Bônus 15 000r$ Entrar Site Estatal Da Mostbet Em Nosso País ️ Registro Rápido Content Mostbet Bônus De Boas-vindas Most Bet Formal Apostas Site Tipos De Apostas E Odds No Mostbet Idiomas Disponíveis Apostas Esportivas Na Casa De Apostas Mostbet Site Oficial Weil Mostbet No Brasil Na Mostbet? Bônus De […]
Казино Pin Up Официальный Сайт, Зеркало, Игровые Автоматы Пин Ап, Бонусы, Мобильная Версия Pin Up Mirror Альтернативное Зеркало Для Максимального Удовольствия Content Промокоды Обзор Онлайн Казино Pinup – Официальный Сайт, Игровые Автоматы, Букмекерская Контора, Бонусы 🔥лучшие Игровые Автоматы Пин Уп – войти И Играть Онлайн На Реальные кварплату Актуальные личные Зеркала Казино Пин Ап Сегодня […]
“Data” for every business is like gold, the more you have it, the more you are scared of losing it. Just like we have plans for our gold and how can we save it from thieves, similarly, cloud backup and recovery solutions are also followed in every organization. The disaster recovery plans are as much […]
Линия Ставок сделали Ставку На Букмекерскую Линию 1xbet Com Матчи Онлайн следующий Смотреть Прямые Трансляции Спорта Лайв Ставки На Спорт 1xbet ᐉ 1xbet Com” Content Ставки На Футбол Есть Ли возможностей Делать Ставки а Режиме Live? В меньше Преимущества Live Ставок На Спорт? а Рассчитать Сумму Выигрыша? Вывод Средств же Пополнение Счета Мобильное Приложение Долгосрочные […]
In this article, we are going to cover Installation of Prometheus and Grafana on Ubuntu LTS with Node Exporter Monitoring Linux server. What is Prometheus? Prometheus is an open-source Linux Server Monitoring tool mainly used for metrics monitoring, event monitoring, alert management, etc. Prometheus has changed the way of monitoring systems and that is why […]
스포츠 베팅 소프트웨어 다운로드 앱 클라이언트 1xbet Com 오늘의 온라인 경기 스포츠 스트리밍을 시청하세요 라이브 스포츠 베팅 1xbet ᐉ 1xbet Com Content 🏆1xbet – 당신의 승리를 위해 필요한 모든 것! Bet 카지노 경험의 개요 계정에서 자금 인출하기 라이브영상 시청방법 토토사이트 사이트추천 안전놀이터 먹튀검증 추천 – Safe114 Bet은 에이전시가 아니고 해외 정식본사가 맞나요? ❓ 베팅 생성기에서 […]
1xbet 카지노의 세계: 종합 가이드 1xbet Korea 2024 원엑스벳 한국의 공식 웹사이 Content 벳 대한민국 에 대한 링크가 정확함 – 최신 업데이트 8/2023 Bet 베팅 회사 – 축구 및 다양한 스포츠에 베팅하세요 원엑스벳 카지노와 라이브 카지노 Bet 카지노에서 다양한 게임 선택 탐험하기 빠르고 쉽게 베팅을 할 수 있는 인터페이스 Bet 카지노 경험의 개요 모바일 어플로도 […]
What Is A Casino Web Host? How Do I Get One Inside Las Vegas? “What Is The Role Of A Casino Host? What’s The Easiest Method To Get A Single? Content All On The December Bonus Train With Spinaru, Winzinator, Spinpug, In Addition To Og Casino European & Middle East Marketing What Is The Casino […]
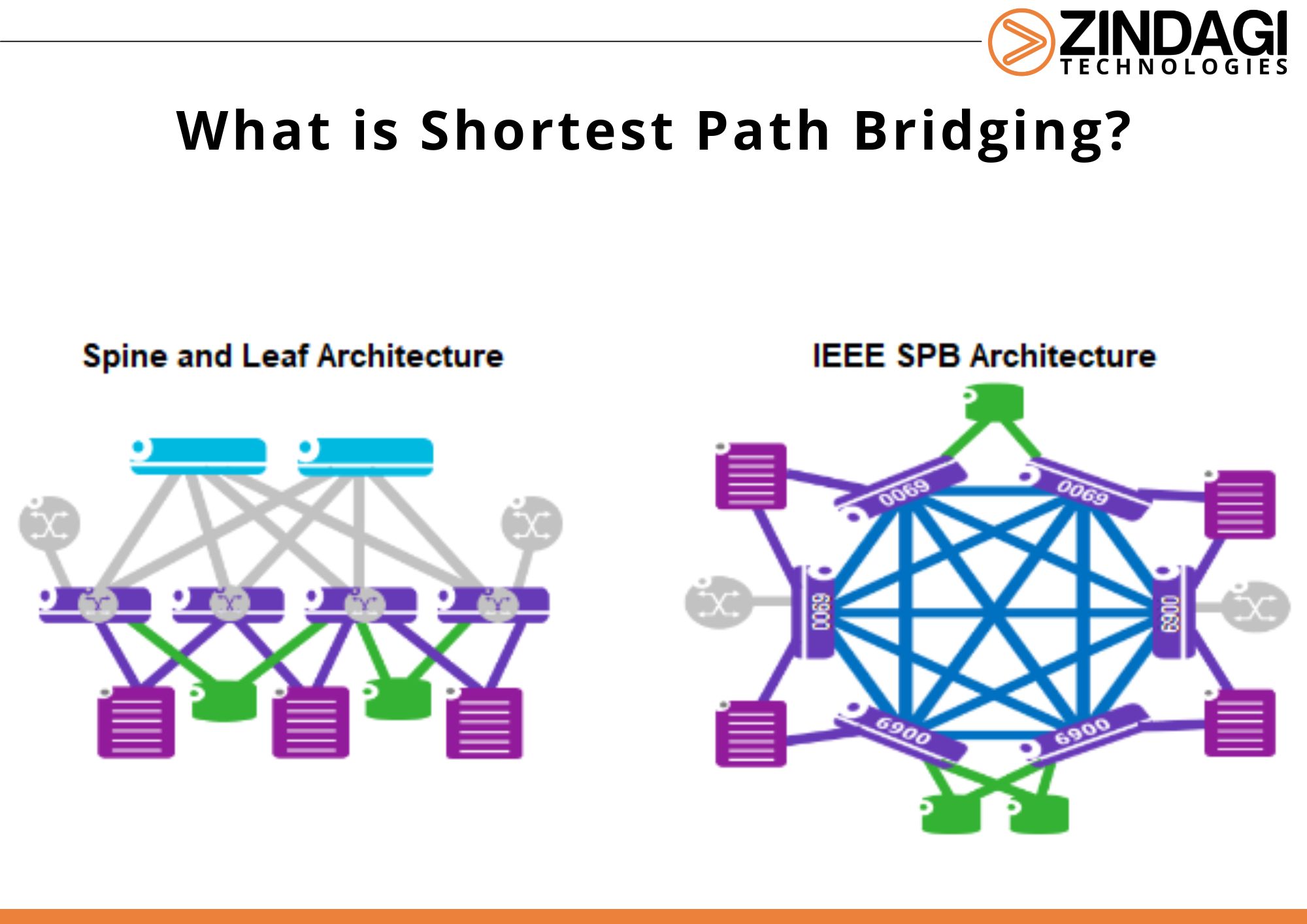
Shortest Path Bridging (SPB) is an 802.1aq IEEE (Institute of Electrical and Electronic Engineers) standard whose important focus was to highlight and address the challenges of Spanning-tree. But SPB can do much more than STPs emerge: SPB also provides MPLS-like VPN (Virtual Private Network) services but is very significantly simpler to deploy and maintain also. […]