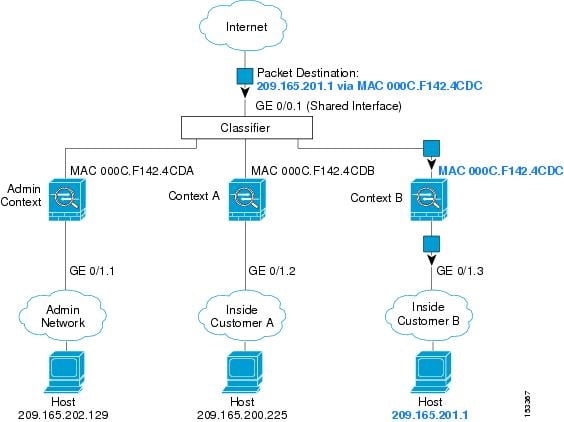
Network Security Engineer should provide security of communication and should be able to restrict access from insecure networks like the Internet. A Firewall is used for the restriction of any unwanted communication between any private and public networks.
Now when we are moving towards Cloud, there is a requirement of multi-tenancy where you want to provide a separate tenant and resources dedicated to individual customers. In order to achieve multi-tenancy in Firewall, ASA provides a feature called Context. Previously we explained the To and Through the Cisco ASA Firewall and today, we will be discussing what is Context and how it works in Cisco Firewall i.e. ASA for traffic belongs to the different customers.
What is Context in Cisco ASA?
Before understanding the concept of Context in ASA firewall, first, we need to understand Virtualization. Virtualization is the process of running a virtual instance of a computer system in a layer abstracted from the actual hardware like we create Virtual Machines on Hypervisor.
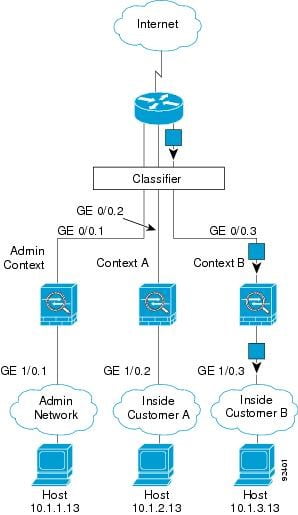
Similarly, Context is the way of Virtualizing the ASA Hardware resources to create multiple instances on ASA FW with dedicated interfaces, Connection entries, NAT entries, Routing Tables for each instance. Traditionally, we used to create VRFs on Routers, similarly, we create Contexts on ASA FW. Every Context in ASA Firewall has a separate RIB, FIB, Interfaces, VPN Table, Connection Table, Xlate (NAT) Table, etc.
Prerequisites for Creating Context in Cisco ASA Firewall?
- For Context Creation on ASA, ASA has a physical firewall box. Like We know ASA comes in Physical hardware form as well as Virtualized form for Hypervisors known as ASAv. So, we cannot create contexts in ASAv, it has to be a hardware ASA Firewall box.
- By default, you cannot create context on the ASA firewall because ASA has 2 modes i.e., Single Mode and Multiple Mode. By default, ASA comes in a single mode, in order to create contexts, you need to change the mode of the firewall i.e., Multiple Mode.
Note: When you change the mode of ASA, it requires a reboot.
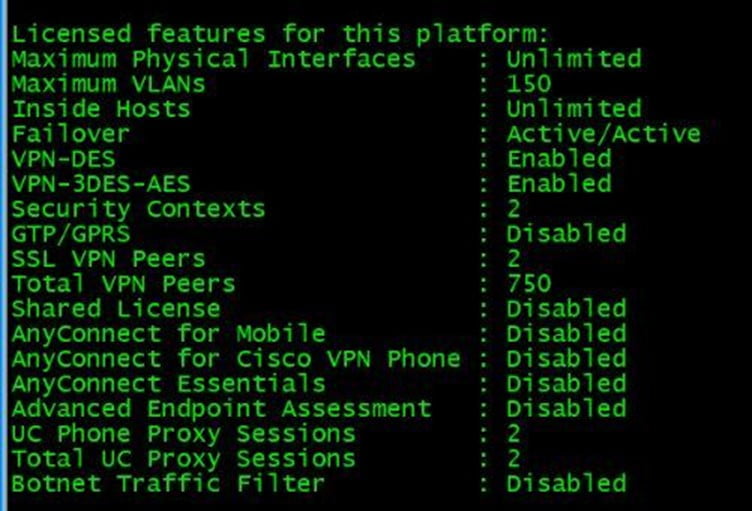
- Licenses- I order to create Contexts, you should have a license for contexts. It is an add-on license required to create contexts. A number of licenses can be created depends on the licenses and hardware capability of the Firewall.

To check the number of Context licenses in ASA, use the “show version” command. The below-mentioned output shows that the ASA has 2 licenses for contexts.
Types of Contexts in ASA Firewall?
There are 3 types of Contexts in the ASA Firewall. Following are the types.
1. SES Context (System Execution Space)
2. Admin Context
3. User Context
System Execution Space (SES) Context
– It is created by default. It cannot be modified or deleted.
– There can only be 1 SES context, not more than that.
– It does not participate in Control and Data plane.
– Whenever we take the console of the Multi-Context ASA, we always login to SES Context by default.
– From SES Context, we create another context and allocate physical resources to other contexts.
– Creation/deletion/suspension of all contexts are done on SES Context.
– Any Configuration done in the SES context gets saved in NVRAM.
Admin Context
– It is also created by default when switching to multi-mode in ASA.
– Admin Context can be deleted, suspended, created from SES context.
– Admin Context is a prerequisite for User Contexts, without Admin Context, User Contexts cannot be created.
– Any Configuration done in Admin Context gets saved in Flash.
– The purpose of this context is generally for management like Remote Access- SSH, telnet, NTP, DNS, etc.
– Only one Admin Context can be there in the ASA firewall.
User Context
– It does not thereby default, we can create user contexts as per our requirement, licenses.
– It can be created and deleted from the SES context only.
– We allocate interfaces or/and sub-interfaces to the User context as per our requirement and the User context takes an active part in Control and Data Plane.
– Every User context has its separate RIB, FIB, Connection Table, NAT Table, configuration, etc.
– Any configuration done in User Context gets saved in Flash
That’s all about the Contexts in ASA Firewall in this blog. In the next blog, will see the High Availability Options in ASA Firewall.
Are you Planning to Deploy Cisco ASA Firewall for your Environment?
If you are planning for Deployment, Tech Refresh, Data Migration from your legacy Firewall or any Firewall to Cisco ASA, or for implementing advanced features in your already deployed ASA Firewall. You can always get in touch with the team at Zindagi Technologies.
Our team consists of experts in the field of Data Centre technologies, Network Security, Enterprise & Service Provider Networks, Virtualization, Private Cloud, Public Cloud, Data Center Networks (LAN and SAN), Surveillance, Wireless, Collaboration, Openstack, storage, ACI, and security technologies with over a 20 years of industry experience in planning, designing, implementing and optimizing complex Network Security and VPN deployments. We can help your organization grow by planning, deployment, and implementation of our services, give us a call at +91 9773973971 or you can also mail us.
Author
Harpreet Singh Batra
Consulting Engineer- Data Center and Network Security