Ethical Hacking involves attacking and trying to gain access to a computer, server, database, or application. Ethical hackers are also known as white hats, ethical hackers are security experts that perform these assessments. It helps to improve the security posture of an organization.

There Are Mainly Five Steps In Hacking
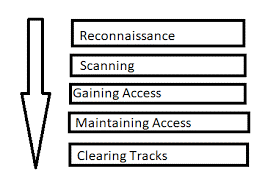
Reconnaissance
The first step of hacking is reconnaissance. It is also known as information gathering or footprinting. In this phase, we collect as much information we can collect about the target. We usually collect information about three groups network, host and people involved.
There are two types of footprinting:
- Active: Direct interaction with the target using tools like Nmap for gathering information.
- Passive: Passivefootprintingis attempting to gather information about the target without directly gaining access to the target. It is also known as social engineering such as social platforms, websites, etc.
Scanning
There are three types of scanning:

- Vulnerability Scanning: Checking the target for vulnerabilities that can be exploited with the help of automated tools.
- Port Scanning: This phase involves a scan of the target for the information such as whether the server is running on the host, which ports are open and live systems.
- Network Mapping: In this phase, we can find the topology of the network, routers, firewalls, servers if any, and the host information and draw the network diagram with available information. This map helps as a valuable piece of gathering information through the hacking process.
Gaining Access
In this phase, attackers break into the system or network using various automated tools or manually. The attacker has to increase his privilege to administrator level so that he can install backdoor or modify data or hide data, after entering the system.
Maintaining Access
When the hacker hacks the system to show it was vulnerable and he wants to maintain a connection with the system without the knowledge of the user by creating backdoor. These backdoors can be created by using trojans, rootkits, or other malicious files. The main aim of the hacker is to maintain the access of the target until he finishes the tasks that he planned to accomplish in that target.
Clearing Tracks
A hacker always is the smartest in the room. He always remembers to clear the tracks so that there will be no evidence later that will lead the trace to him. This involves modifying, corrupting, deleting the value of logs, modifying registry values and uninstalling all the applications he used, and deleting all folders he created.
Types of Hackers
There are mainly three types of hackers:
- White Hat Hacker – White Hat hackers are also called an ethical hackers. White hat hacking is legal basically it uses the same process as the hacker to detect the vulnerability and protect the system against hackers as they have full knowledge about the network.
- Black Hat Hacker – Black Hat Hacker is also called an unethical hacker. It is illegal as they don’t have permission and authority to enter the network and they enter forcefully.
- Grey Hat Hacker – Grey Hat Hacker is the hybrid between white and black hats. They don’t have permission but they don’t cause harm to your network or system. But sometimes it is acted as legally and sometimes not.
We at Zindagi Technologies are providing a defensive approach for your network against these hackers. We offer planning, deployment, implementation, and documentation. You can contact us at +919773973971.
Author
Shivam Rana
Associate Consultant
Comment (1)
Leave a comment
You must be logged in to post a comment.







Cross-site scripting & its prevention | Zindagi Technologies
May 18, 2023[…] will be able to take full control of the app’s functionality and data. It is also done by an ethical hacker to check for vulnerabilities in your […]