Cryptography is the study of secure communication that allows the sender and recipient of a message to have highly secure and confidential to view its contents. The data is encrypted using a secret key, and then both the encoded message and secret key are sent to the recipient for decryption.
What are the Objectives Of Cryptography?
The main principle of cryptography is C.I.A (confidentiality, Integrity, authenticity)
- Confidentiality: Confidentiality ensures that only the recipient can decrypt the message and read its content.
- Integrity: Integrity focuses on the ability to ensure the information contained in the message cannot be modified.
- Authenticity: Authenticity ensures the sender and recipient can verify each other’s identities and the destination of the message.
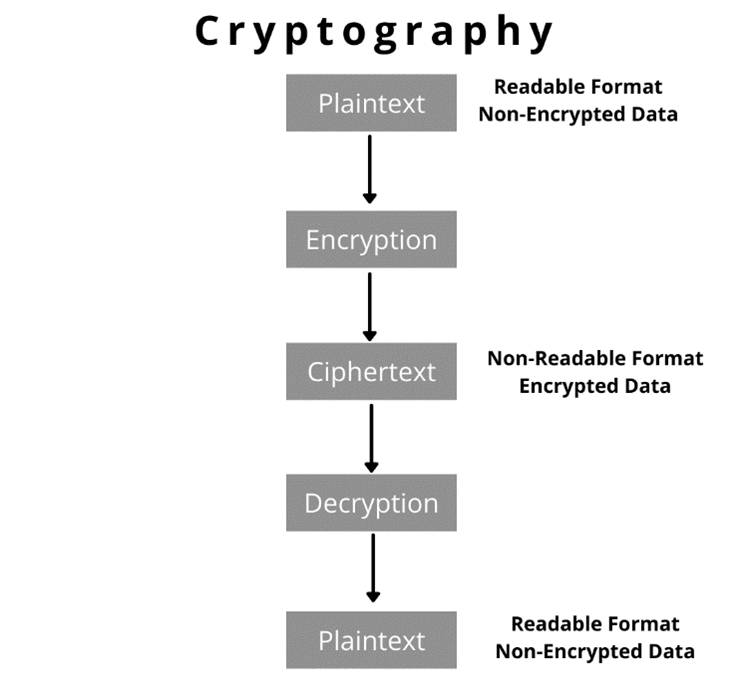
Listed below are the Types Of Cryptography.
In general, there are three types of cryptography:
- Symmetric Key Cryptography: It is an encryption system where the sender and receiver of a message use a single common key to decrypt messages. Symmetric key systems are faster and simpler but the problem is that the sender and the receiver have to exchange in a secure way so that the key does not get exposed. The most popular symmetric-key cryptography system is Data Encryption System (DES).
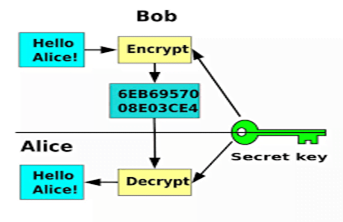
- Asymmetric Key Cryptography: In this system, a pair of keys is used to encrypt and decrypt information. A public key is used for encryption and a private key is used for decryption. The main advantage of Asymmetric key cryptography is that it uses 2 keys so if the public key is known by everyone but they cannot decode the message as the private key only decode that message which is the recipient.
- Hashing Cryptography: Hashing is a method of cryptography that converts any form of data into a unique string of text. Any piece of data can be hashed, no matter its size or type. Hashing is a mathematical operation that is easy to perform, but extremely difficult to reverse. The difference between hashing and encryption is that encryption can be reversed, or decrypted, using a specific key. The most widely used hashing functions are MD5, SHA1, SHA-256.
When an organization discovers that a platform’s password has been compromised it usually means that hackers have acquired the hashes that represent the passwords. Hackers then run hashes of common words and numbers to decipher some of the passwords that are unsaved.
What Could Be The Disadvantage Of Cryptography
With some major advantages, there are always drawbacks such as strong encrypted, authentic, and digitally signed information can be difficult to access even for a legitimate user at a crucial time of decision making. Cryptography comes at a cost like the addition of cryptography techniques in the information processing leads to delay and the use of public-key cryptography requires setting up and maintenance of public key infrastructure requiring a high budget. High availability cannot be ensured through the use of cryptography.
We At Zindagi Technologies Are Here To Help To Protect Your Network. We Offer Planning, Deployment, Implementation, And Documentation. You can contact us on our email or can drop us a WhatsApp too on +919773973971
Author
Shivam Rana
Associate Consultant
Comment (1)
Leave a Reply to rescator Cancel reply
You must be logged in to post a comment.







rescator
November 26, 2022In your posts and blogs, you share how-to information with such good humor that is greatly appreciated.