Generic Routing Encapsulation and Dynamic Multi-Point Virtual Private Network Implementation With IPsec
What Is Generic Routing Encapsulation (GRE) Tunnel?
A tunnel means a virtual interface for connecting two directly or indirectly connected devices. GRE is a layer 3 protocol and it uses protocol number 47. With the help of GRE, we can create a tunnel between two different sites, but it will not provide security. So, for security, we will use IPsec, with the help of which we can encrypt the traffic. GRE will provide connectivity or reachability between private to private over public/internet and IPsec will provide security by encrypting the traffic. So, GRE with IPsec will give secure reachability between two sites.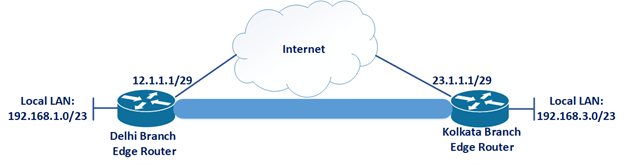
Suppose, we have two sites, Delhi and Kolkata. We already have reachability from Kolkata to Delhi, i.e., ping from 23.1.1.1 to 12.1.1.1 is successful. Now we want reachability with security from Delhi local LAN network 192.168.1.0/23 to Kolkata local LAN network 192.168.3.0/23. So, we will configure GRE with IPsec.
What Is Virtual Private Network (VPN)?
A virtual private network is a feature by which we can communicate from private to private network over a public network.
What Is Dynamic Multi-Point Virtual Private Network (DMVPN)?
Dynamic multi-point virtual private network (DMVPN) is a Cisco patented feature that allows you to access through a single tunnel interface to multiple tunnel interface. If you have multiple branches and you want to share the information and resources between them then you can implement DMVPN.
Difference between GRE and DMVPN
GRE is a layer 3 protocol and it uses protocol number 47. Using GRE tunnels, we can communicate between two sites and if one site required multiple site reachability then we must create different GRE tunnels for different destinations.
So, there is a solution DMVPN, it is not a protocol but a feature that uses multiple protocols that include GRE, NHRP, routing protocol that we want to use.
DMVPN allows us to communicate multiple tunnel interfaces through a single tunnel interface. DMVPN is divided into three phases phase-1, phase-2, phase-3. Each phase has its own functionality according to your network requirement you can choose and configure the appropriate phase.
DMVPN Phase-1
Suppose Delhi is the head office and Kolkata and Mumbai are the branch office. All sites are connected to the Internet, and connectivity from Kolkata to Delhi, Delhi to Mumbai, and Mumbai to Kolkata, i.e. ping from 23.1.1.1 to 12.1.1.1, 12.1.1.1 to 34.1.1.1, and 34.1.1.1 to 23.1.1.1 are successful. Now we want reachability with security between Delhi local LAN network 192.168.1.0/24, Kolkata local LAN network 192.168.3.0/24, and Mumbai local LAN network 192.168.2.0/24. Now we will configure DM with IPsec.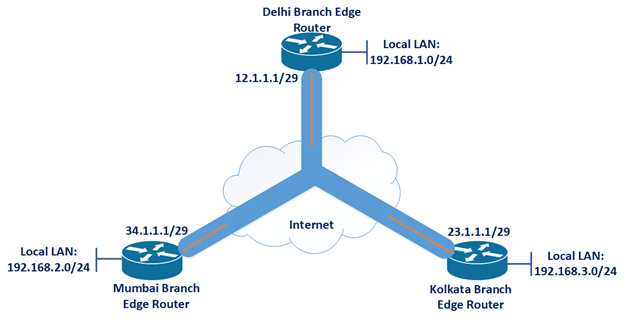
In DMVPN phase 1 spoke to Hub about direct reachability but spoke to spoke reachability will be via Hub. So, if in your network if there is a requirement that branch office can communicate to head office directly but if any branch office wants to communicate to another branch office then it must send traffic via head office, then you can configure DMVPN phase 1 with IPsec. This will allow you more security and control for traffic, you can configure a policy that who can talk to whom and also allows you to do accounting and monitor in head office because all traffic is going via head office.
DMVPN Phase 2:
In DMVPN phase 1 all traffic will go via Hub so which will increase the overhead of the Hub device. In DMVPN phase 2 we will have direct reachability between Hub to spoke and spoke to spoke. So, if in your network if there is a requirement that all sites can communicate with each other, there is no requirement that branch office should go via head office then we can configure DMVPN phase 2 with IPsec.
In the DMVPN phase 2 we have done two important changes in Hub i.e. Delhi head office, 1st disable split horizon and 2nd disable next hop self. Now when we initiate 1st packet for a spoke to spoke it will go via Hub. And side by side sender spoke will send ‘next-hop resolution request (by this message sender spoke is asking for the public IP address of the other end spoke) to Hub. Now Hub has information of all spokes, so Hub will forward the message to the destination spoke.
Now destination spoke will receive the message and add a dynamin entry in which it will update-source spoke tunnel IP address and public IP address and after that, it will give the reply directly to source spoke and source spoke will also create a dynamic entry for destination spoke (this entry will be there for two hours). After that source spoke will send traffic to the destination spoke directly not via Hub.
Now some problems with DMVPN phase 2
1. We can’t perform summarization on Hub.
2. We can’t perform OSPF
So, to overcome those problems we can configure DMVPN phase 3
DMVPN Phase 3
In DMVPN phase 3 we will have direct reachability between Hub to spoke and spoke to spoke. So, if in your network if there is a requirement that all site can communicate with each other, there is no requirement that branch office should go via head office and you required summarization at head office and also wanted to configure OSPF for tunnel interface reachability then we can configure DMVPN phase 3 with IPsec.
In DMVPN phase 3 background process will happen in this way- Spoke 1 (Mumbai) will send 1st packet to Hub (Delhi) but the destination is spoke 2 (Kolkata). Now Hub (Delhi) will receive the packet forward it to spoke 2 (Kolkata) and Hub (Delhi) router will notice that my ingress interface and egress interface is the same for this packet i.e. Spoke 1 (Mumbai) can directly reach spoke 2 (Kolkata), then Hub (Delhi) router will send ‘NHRP indication” message to Spoke 1 (Mumbai) and after that Spoke 1 (Mumbai) will send NHRR (next-hop resolution request) to Hub (Delhi).
Now Hub has information of all spokes, so Hub will forward the message to the destination spoke. Now destination spoke will receive the message and add a dynamin entry in which it will update-source spoke tunnel IP address and public IP address and after that, it will give the reply directly to source spoke and source spoke will also create a dynamic entry for destination spoke (this entry will be there for two hours). After that source spoke will send traffic to the destination spoke directly not via Hub. The local user of a branch office or head office has private to private reachability over the public network with security.
Apart from Cloud and Data Center Network solution Zindagi technologies also provides design and implementation for the security domain. For any queries give us a call at +919773973971 or contact us at Zindagi Technologies.
Author
Dipayan Sarkar
Network Security Consultant
