What is IEEE 802.1ae (MACSec) & How does it work?
In this article, we are going to discuss MACSec & its role in our network environment.
The following topics will be covered in this article:
- What is MACSec?
- Why MACSec as a solution?
- How MACSec works?
- Configuration of MACSec
What is MACSec?
MACSec stands for Media Access Control Security. It was introduced in 2006 by IEEE 802.1ae. It operates at the Data-link layer (Layer-2) and secure point-to-point link. It has become an important encryption technology. It provides secure communication for Ethernet Networks.
MACsec is based on the standard Ethernet Frame format and its encoding is as follows:
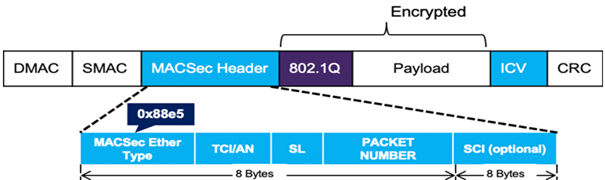
Why use MACsec as a Solution?
Whenever MACsec is configured, each packet on the wire is encrypted.
We have several advantages of using MACsec in our network environment:
- Confidentiality
- Integrity
- Flexibility
- Network Intelligence
Confidentiality
MACsec protects our data from unauthorized access. An unauthorized user should not be able to reach the content of data. So, MACsec provides confidentiality by using strong encryption.
Integrity
When we say integrity that means protecting our data from unauthorized alteration. We should have a mechanism to detect modification of data. So, MACsec performs an integrity check to prevent data tampering and make sure that data is not modified in transit.
Flexibility
MACsec is flexible as we can enable/disable it on any selective interface on a MACsec capable device.
Network Intelligence
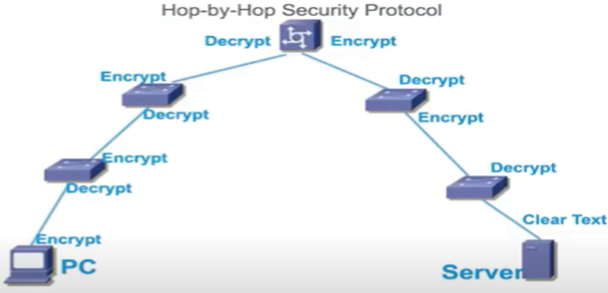
MACsec does not hide the content of data from network devices as MACsec is a hop by hop encryption. When we say hop by hop encryption means that the data will be decrypted on the ingress port & encrypted on the egress port. The data will be in clear text form on a network device.
How MACsec works?
There are mainly two steps involved for data security:
- MACsec uses MKA (MACsec Key Agreement) to discover and establish the session with peers.
- MACsec uses SAK (Security Association Key) to encrypt and decrypt the data traffic.
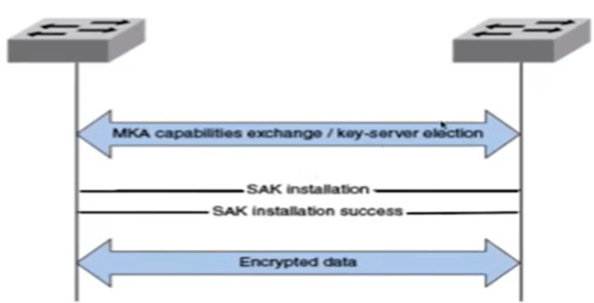
- When MACsec enabled interface comes up they start exchanging MKA PDU’s. If parameters are valid then the peer will be discovered and accepted.
- Now we will see the concept of Key-Server. It is responsible to generate and distribute Security Association Key (SAK). The key server is elected on the basis of priority (default = 16).
- Once SAK is formed, MACsec uses SAK to encrypt the data traffic on a protected link or secure link.
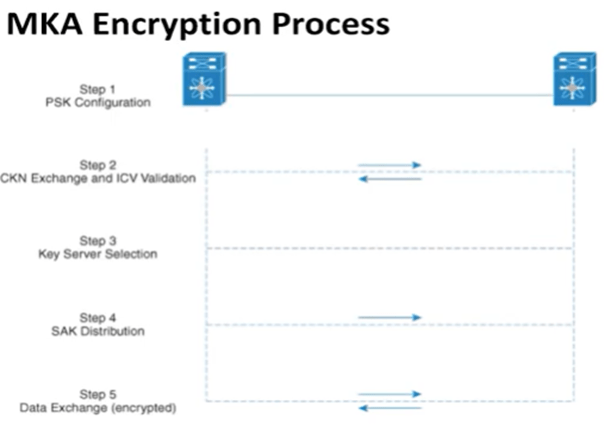
Here we will see about the Pre-Shared Key (PSK) mechanism which is used for “Authentication” and MKA (MACsec Key Agreement) protocol which is used for “Key Management”.
Step1: We configure PSK on both devices. It is also known as CAK (Connectivity Association Key). It is used for mutual authentication. Once peer authentication gets successful, Connectivity Association (CA) will be formed between the peers.
Step2: Then they will exchange CKN (Connectivity Association Key Name) and validate ICV (Integrity Check Value) with PSK. CKN is used for configuring the key value.
Step3: Then key server selection will happen. It is responsible to generate and distribute SAK.
Step4: Once SAK is formed, MACsec uses SAK to encrypt the data on a protected link.
Configuration of MACsec
Configuring MACsec involves the following steps:
- Creating a MACsec keychain
- Creating a user-defined MACsec policy
- Applying MACsec configuration on an Interface
Creating a MACsec keychain:
Switch (config) # key chain <NAME> macsec
Switch (config-keychain-macsec) # key 01
Switch (config-keychain-macsec-key) # key-string <128 bit or 256 bit>
Switch (config-keychain-macsec-key) # life-time
Creating a user-defined MACsec policy:
Switch(config) #mka policy <MKA Policy Name>
Switch(config-mka-policy) # macsec-cipher-suite ?
gcm-aes-128 GCM-AES-128 Cipher Suite
gcm-aes 256 GCM-AES-256 Cipher Suite (choose any)
Switch(config-mka-policy) # confidentiality-offset ?
0 MACsec Confidentiality Offset value of 0 octets (bytes) (choose any)
30 MACsec Confidentiality Offset value of 30 octets (bytes)
50 MACsec Confidentiality Offset value of 50 octets (bytes)
Switch(config-mka-policy) # key-server priority ?
<0-255> Key Server Priority (255= never act as Key Server)
Applying MACsec configuration on Interface
Switch(config)# interface gi0/0/1
Switch(config-if) # macsec
Switch(config-if) # mka policy MKA_POLICY
Switch(config-if) #mka pre-shared-key key-chain <NAME>
In this blog, we learned the basic concept and the requirement of MACsec. We also learned the workflow of MACsec in our network environment and covered the implementation part as well on a device. Zindagi Technologies has been helping LE and MSE in securing organizations with giving services like cyber security, data protection, data center implementation, Managed IT, and many more. Being an IT consulting service provider, we give the best when it comes to service. For more information, you can get in touch with us on WhatsApp, +91 97739 73971, you can also mail us or visit us on our website.
Author
Sani Singh
Consultant – Enterprise Networking

coloby
December 5, 2022hello
thank’s for the article
As it is for peer to peer, it is not working for multicast Layer 2 message ? broadcasrt L2 ?
if not working, what can be the solution for multicast/broadcast Layer 2?
Thank you
Regards
Manish K
October 15, 2023Very neat clear explanation