What is Zero Trust Network Access? What are the advantages of Zero Trust Security?
According to Gartner, by the year 2022, around 80% of new business applications will be accessed through Zero Trust Network Access and by 2023, around 60% of enterprises will be phasing out their remote access VPN in the favor of ZTNA.
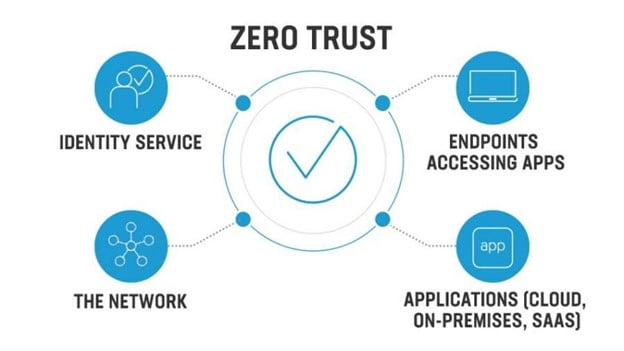
What is ZTNA? It is a software defines perimeter service that provides secure and seamless connectivity to private users without even placing any user on the network frame or by exposure to the internet. It is a model that delivers security that is based on users and applications and not the IP addresses no matter what the location is and the device of the user.
The organization wants to adopt zero trust security and as the name suggests this model is built for the mobility and cloud-first models. As far as the IP addresses are concerned, they were built for the connection and not for securing the connection and this is why they are identified as weak security. The IP address’s security can be abused because of their default allow feature which will lead to “trust issues”. Since exposing IP is risky and being connected with everyone in the organizations so everyone had to come to one island; the island was adopting firewalls, which is been seen in the past 30 years.
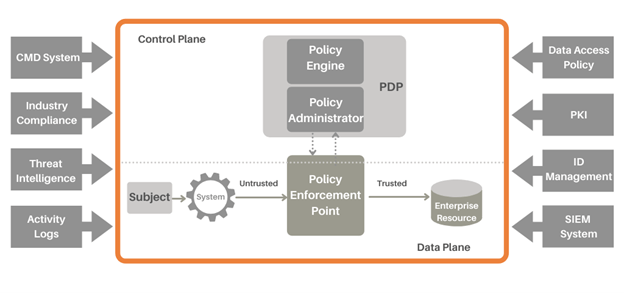
How does Zero Trust Network work?
After ZTNA authentication, the access is established with ZTNA. On the user’s behalf, access is provided to the application through an encrypted tunnel. An extra layer of protection is added to the corporate applications by covering the visible IP that is otherwise public. The support of dark cloud is also given by ZTNA so that the users cannot see the applications that they do not have the access to. If someone is attacking at a later moment then the protection will be intact as the endpoint point which is compromised will be scanned swiveling to other services.
What Are The Benefits Of Zero Trust Network Access?
Reduction In Business Risks As Well As Organization Risk
It is an assumption of Zero Trust that until and unless the services and the applications are identified by the attributes such as authentication and authorization requirements. The risk is reduced as Zero trust Network uncovers all that is on the network and makes the communication of the assets are communicating. The risk of continuous credential checking of every communicating asset is also reduced.
Providing Access Controls Over Container And Cloud Environments
The greatest fear of those who practice security is about moving to and fro from the cloud of visibility and access management. Even though the cloud has evolved but the workload of security remains a combined responsibility between the organization and the CSP. There is only a little that can be affected in an organization’s cloud.
All the security policies are applied on the basis of the identity of communicating workloads and this is done with zero trust security architecture. Security is closely held to the assets that when the protection is required then it is not affected by IP addresses, ports, and protocols. Thus the protection is not changed even when the environment changes as it travels along with the workload.
Reduced Risk Of The Data Breach
The principle of zero trust is that every user or device or workload is assumed hostile. This results in the inspection of every request and the authentication of users and devices. Not only this but the “trust” is also granted before the permissions are accessed. The “trust” is reevaluated the moment context is changed, like the location of the user.
Compliance Initiative Supportive
One of the best things about Zero trust is that all users and connections are protected from the internet in a way so that they are not exploited or exposed in any way. Because of the cloak of invisibility, the demonstration is simpler and is compliant with all privacy standards; giving few findings in audits. When a data breach is encountered then the visibility is complete and so is the control over network architectures.
What Advantages Do We Get From Zero Trust Security?
This is one of the rare security modules that is sure to stop cyberattacks. So obviously the advantages are going to be there for Zero Trust Security.
Working In A Remote Environment Is Easy
Almost every user is granted secure and safe remote access through zero trust. It is much more superior to the VPN system and can provide for a single location. Without impacting the security, the network of your organization becomes clear and vibrant with zero trust. Great control over cloud computing is also offered by zero trust; the main point considered for remote working.
Integration Is Easy
If the organization is not using any cloud-based system then they might have different private servers and networks. So going through a lot of different procedures for integrating the security module. Things are different in a zero-trust system as the integration and implementation are easy as it has a flexible base.
Unmatched Security
In this blog, we have only talked about the unmatched security that is provided by Zero Trust access in remote working. The dividing of network systems by the organization is a pro as, without authentication, anyone cannot enter the server; both risks about internal and external security are eliminated. Technology transformation is important and re-establishing the security system will save the organization from all types of cyberattacks ZTNA is a bit more sophisticated and adequate in the terms of security and will strengthen your network environment. Having Zindagi Technologies on your side will give more power and best security measures to your organization. We have brilliant engineers with great experience and commendable working and problem solving abilities. The CEO of Zindagi Technologies, Abhijit Singh Anand conducted a webinar on Deploying Wifi6 on a large-scale campus and our next webinar would be Zero Trust Network Access. You can register here and can have all the knowledge about Zero Trust Network access and whether it is a good option or not for your organization. Meanwhile, you can contact us on +91 97739 73971 or can get in touch with us by mail too.
Author
Shweta
Senior Content Writer
