3 Options To Choose Your Best Antimalware Solution
Earlier, we told you about the ultimate Antiware Solution named Symantec Endpoint Security. Whereas in this blog, our focus will be on the types of Symantec Endpoint Security Solutions, their features, and the differences between them.
Symantec Endpoint Security Solution
Symantec Endpoint Security is leading the market as the best Antimalware solution as it offers the industry’s most effective and advanced threat protection with single-agent, multiple deployment options.
Symantec Endpoint Security is designed, developed, manufactured by an American-based company Broadcom Inc.
Broadcom sells three types of Endpoint Security solutions Symantec Endpoint Protection, Symantec Endpoint Security Enterprise, and Symantec Endpoint Security Complete.
Symantec Endpoint Protection is an on-premises-based industry-leading security solution. It is running as no 1 protection all over the world. Now also as per the AV-Test, it is rated as best Performer.
Symantec Endpoint Security Enterprise has all the capabilities of SEP with some additional features such as the extended capability to protect all operating systems including Mobile, Cloud management, etc.
Symantec Endpoint Security Complete offers complete protection to the Endpoints with some added capabilities and advancements than SEP and SES Enterprise. For example, Endpoint detection and response technology, threat hunting, breach assessment, etc.
Similarities and Differences between all three Symantec Products
Following are the features, protection technologies, and capabilities of Symantec Products.
Features
Deployment and Management Options
It defines the deployment and management capability of the SES solution. There can be three deployment methods on-premises, cloud, and hybrid. The Symantec product that has the capability to support which deployment option is mentioned in the following table:
Requirement of Protection Agent
Agent on the endpoints is required which installs on endpoints and communicates with the manager to exchange content updates, reports, security policies, logs, roles and access, security, and administrative functions.
Supported Operating System
The operating systems which can be protected by the products are mentioned in the table below.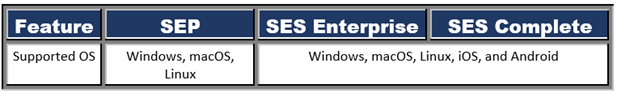
Supported Devices
The types of devices which can be protected by the products are shown in the below-mentioned table.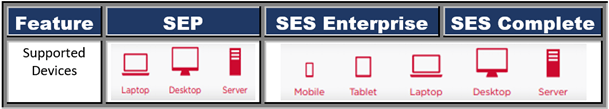
Protection Technologies
Attack Surface Reduction
Symantec Endpoint Security Solution offers proactive endpoint security with preattack surface reduction abilities. It constantly scans for misconfigurations and other vulnerabilities across the devices, AD, applications, etc., according to the advanced policy control and technologies.
Breach Assessment
Constantly simulates attacks and breaches to discover vulnerabilities, misconfigurations, and backdoors that can be used by an attacker to compromise the system completely.
Application Control
Evaluates the vulnerabilities and the risks of applications and allows only authorize an application to run on the system.
Behavioral Isolation
It assesses the trusted or authorized application and prevents it to run malicious code.
Device Control
It specifies allow and block policies based on the removable devices that connect to the endpoint like USB drive, dongle, etc.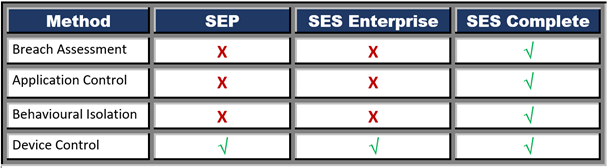
Breach Prevention Technologies
Symantec Endpoint Security uses multiple proven methods and utilizes AI also to prevent a breach like a firewall, intrusion prevention, etc. Methods supported on different Symantec products are explained below. Firewall: It handles the network access based on the configured default and custom policies.
Firewall: It handles the network access based on the configured default and custom policies.  Intrusion Prevention: It inspects the packets deeply, detects and blocks the web attacks, malicious inbound and outbound traffic.
Intrusion Prevention: It inspects the packets deeply, detects and blocks the web attacks, malicious inbound and outbound traffic. Deception: It utilizes multiple receptors (lures and baits) like fake credentials, web requests, shared folders, files, cache entries, etc., to expose hidden opponents and reveal the attacker’s intention, strategies and delay them through early visibility.
Deception: It utilizes multiple receptors (lures and baits) like fake credentials, web requests, shared folders, files, cache entries, etc., to expose hidden opponents and reveal the attacker’s intention, strategies and delay them through early visibility. AD Security: It identifies the exploitation of AD credentials and prevents breaches and lateral changes at the Endpoint.
AD Security: It identifies the exploitation of AD credentials and prevents breaches and lateral changes at the Endpoint.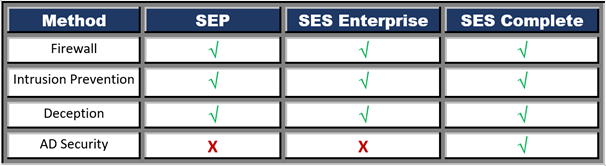
Attack Protection
Symantec Endpoint Security Solution acts against different methods and vectors of files and file-based attacks instantly and efficiently.
Industry-leading Anti-Malware
It utilizes the following capabilities and provides the best antimalware solution. It protects the system from all kinds of threats.
– Antimalware
– Behaviour Based Prevention
– Intensive Protection
– Memory Exploit Mitigation
– Advanced Artificial Intelligence and Machine Learning
Mobile Threat Protection
It calculates, identifies, and protects physical, malware, network, and vulnerability abuses to protect enterprises from mobile cyberattacks.
Network Connection Security
It detects the rogue wi-fi networks and protects the devices when operators work in public areas and are on non-company networks.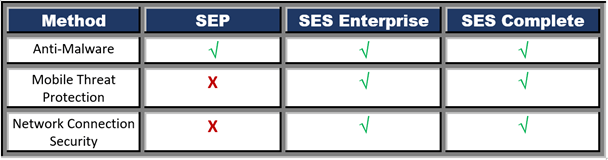
Remediation and Response
Symantec Endpoint Security solution gives you the tools required to rapidly close out endpoint events and minimize attack impacts by uniting EDR technologies and unique SOC specialist skills.
Threat Hunter
It utilizes a combination of Machine Learning technologies & Symantec’s Expert Threat Hunter’s power to help detect high-fidelity incidents.
Behavioral Analysis
It has the capability to analyze and record activities from all the running processes from the client machine to detect advanced attack techniques. It can be searched and retrieved remotely to assist investigation and remediation.
EDR (Endpoint Detection and Response)
It helps the SOC team to detect and prevent threats with different actionable behavioral analysis, intelligence, and enhanced investigation and response tools.
Rapid Response
It acts immediately and minimizes the time to rectify threats and respond to invaders in real-time.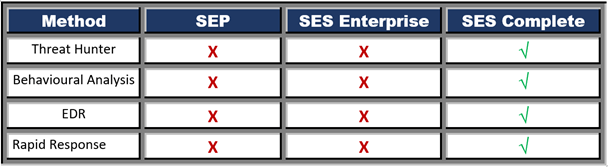
Now as we have explained and covered most part of the Symantec Endpoint Security solution which include the types and the similarities as well as differences between the products. This blog will help you in the right selection of the product according to your organizations requirements.
Furthermore, one would always need a specialist to plan, design and deploy Endpoint Security solutions and we are the best in doing so. Being a leading organization, which is a leading IT consulting company has successfully planned, designed, and deployed multiple Endpoint Security Solutions in Public, Private, and Defence sectors.
Our plan is to give the right service to the customer and take utmost care of their satisfaction and this is why our techs deliver the best results. If you want to deploy security solutions for your organization then let’s talk about it on +919773973971.
Author
Ankesh Singh
Network Consultant Engineer
