5 Steps To Conduct The Cloud Security Assessment
Benefits are offered like cost cutting and improvement in end-user productivity are a part of cloud based applications and services. But still cloud platforms may pose security risks that are quite similar to the software and services. If the proper steps are not taken then a cloud disaster could happen and you might end up losing the data. Comprehensive Cyber Security Solution in Delhi are provided by us and you can save the data in your cloud by taking up the benefits.
What Do We Understand By Cloud Security Assessment?
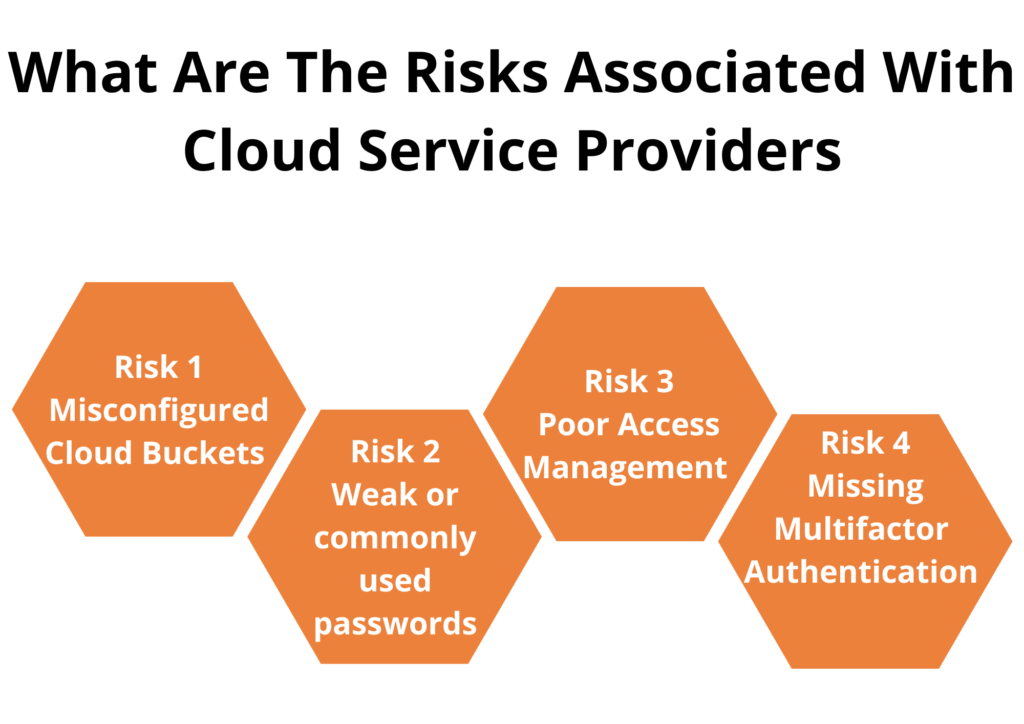
The security professionals estimate the security risks of the cloud infrastructure, and this is known as cloud security assessment. It examines the security aspects and determines that if they are in place or not and it will also determine that if the controls are appropriate for the designated use case for which they are designed for the application.
The organization should conduct the security assessment of the present and future cloud deployments as this is a critical part of the process.
5 Steps Of Cloud Security Assessment
Cloud security is not easy and its assessment is difficult too as it takes time and resources and good experience to accomplish and in the following 5 steps, we will explain how successfully we can conduct the cloud security assessment.
The Scope
Understanding the present condition of your cloud application is the first step in the process. This will enable you to decide on the assessment’s scope. What are you attempting to achieve? What are you attempting to evaluate?
Investigation Or Discovery
The auditors conduct recon on the agreed-upon scope in the second step following the scoping process. Reconnaissance may be defined as the process of learning about an organization’s strengths, vulnerabilities, and potential points of attack. In other words, information on a target is gathered broadly as part of reconnaissance.
Testing Of Vulnerabilities
The method of vulnerability testing is used to find potential defects in assets that have previously been found. Testing for vulnerabilities seeks to evaluate the dangers that can be seen in the discovered assets. To test the cloud and look for vulnerabilities in the cloud infrastructure, testers employ a variety of tools. Using a hacker mentality, they search for flaws and attempt to develop ways to exploit such weaknesses.
Reporting Of The Seen
The reporting team receives the results of the vulnerability assessment so they can create an in-depth report. The purpose of the report is to clarify how secure the infrastructure and applications are.
Repeating The Test
Retesting is the last phase of the cloud assessment, and it is done only once the issues are fixed, and the customer wants to get it tested again. A retest is essential to verify the issues have been fixed. Retesting is an important step in the cloud assessment process, thus it is advised to include it in the project and not skip this stage.
Cloud security assessment is essential as it helps in identifying the weak areas and the risks involved in your organization, it follows with the process of risk mitigation. This in turn will help the organization in becoming an organization with a good security posture and that too aligned with the business goals and objectives.
Zindagi Technologies is a leading company of Cloud Testing in Delhi and will also help in vulnerability assessment and penetration testing. We have experience in all types of security assessments that will be aligned with your organization goals and objectives. To know more about the security options, get in touch with us or you can give us a call on +91 97739 73971.
Author
Shweta
Senior Executive, S&M

Cybersecurity audit and assessment | Zindagi Technologies
August 25, 2022[…] be mitigated. Many might be having a notion that compliance assessment, maturity assessment, and cyber security risk assessment are all same but with a different […]