5 Things To Consider Before Installing CISCO FTD Firewall
Cisco Firepower Threat Defense (FTD) is Cisco’s Next-Generation Firewall provided with the best of the industry features. It is easy to deploy, configure, manage, and troubleshoot. The Graphical User Interface (GUI) provides a smooth experience to a user for configuration, analysis, troubleshooting. Below mentioned are the components that make a complete Cisco Firepower Threat Defense Solution.
Firepower Management Center
It is a Centralized Manager which is used to manage, configure, troubleshoot, generating reports, and visibility of devices. FMC can be deployed as dedicated hardware and as a Virtual Machine if you already have some spare compute/server for it. FTD firewalls get registered to FMC and then FMC is the master, which can push any configuration or fetch any details to/from FTD Firewalls.
Firepower Threat Defense
It is a firewall image that can be installed on Firepower Chassis or as a Virtual Machine on Server. Firepower chassis is preinstalled with Firepower Extensible Operating System (FXOS). On top of FXOS, the Cisco FTD image can be installed as a container which is your actual firewall software. You can compare FXOS with a Hypervisor and FTD as a VM running on top of Hypervisor. Once the FTD image is deployed, FTD is required to be registered with FMC for further configuration.
Key Considerations for Cisco FTD Solution
Plan The Right Hardware/Software For Your Environment
The very first step is to understand what model of FTD and FMC appliance is the right fit for your environment. Let’s start with FTD first. We know that FTD is our main firewall software code. Cisco offers both variants whether you can install FTD on Firepower Chassis or you can install it as a Virtual machine on top of any *86 server. Cisco offers FTDv supported for Vmware Esxi and KVM hypervisor.
Depending upon your requirement like if you are planning for a perimeter security device, an ideal choice would be for Physical Firewall whereas if you already have a Perimeter firewall and you want to have a dedicated Firewall for your cloud customers or if you have workloads running on AWS or any public cloud, you may have a requirement of a firewall to manage security restrictions between your application groups, you can better go for a virtual firewall.
Also, Virtual Firewalls have limited support of throughput. As per the day when we are writing this blog, the maximum supported throughput on FTDv is 10Gbps whereas FTD on physical Firepower 9300 chassis supports up to more than 100 Gbps.
Another factor could be that if you already have perimeter firewalls and existing infrastructure running, but you want a VPN concentrator could be for IPsec tunnels or SSL VPNs and your existing firewall may not support or be feasible for this requirement so in that case, you a better choice could be a virtual FTD. The last but not the least factor is urgency, if you have an immediate kind of requirement, you can buy FTDv and use it whereas buying hardware and getting it to deliver takes more time.
If you decide to go with hardware Firepower Chassis for FTDs, the most important thing you need to take care of is the throughput supported on the hardware. Let’s suppose you are planning to buy a Firepower FTD firewalls for your Data Center and you expecting both east-west and north-south traffic to be passing via FTD Firewalls, and expected throughput could be 40 Gbps but if you bought the Firepower chassis which supports less throughput then 40 Gbps, then you are in trouble. So please be very careful when deciding the right Firepower chassis for your environment.
Another component is FMC, the managers of the Firewall. Similar to FTD, Cisco offers FMC in 2 variants hardware FMC and Virtual FMC which is supported on VMware ESXi and KVM-based hypervisors, also supported on most of the leading public cloud vendors like AWS, Azure, GCP, etc. There is a saying “You can’t protect what you can’t see” so that’s where FMC plays its role. It is not just for centralized device and configuration management, but also it collects, collates, and displays contextual information about everything running in your network.
If you have on-prem devices, we will always prefer to go with hardware FMC because you will not have to worry about performance parts, hardware considerations like IOPS, Hard drives, Clock rate in CPUs, etc. If you are planning to set up a lab then FMCv would be an ideal choice. Moreover, physical FMC supports more sensors (FTDs), logs, Concurrent connections, etc.
Physical Connectivity
The next thing you need to consider is Physical connectivity. It depends upon the throughput of the Firewalls and Network Modules/Interfaces available on the Firewalls and FMC appliances. Accordingly, you may need to factor in the transceivers as well. As we know that there are multiple series/models of hardware Firepower chassis are available. Each hardware model has a fixed number of interfaces and/or slot available for additional network modules which can be procured optionally. The physical connectivity depends upon the environment, like if you are planning to deploy FTD Firewalls for perimeter security of your campus network, then probably you will connect the firewalls between your WAN Edge Switches and Core switches but if you are planning to setup Firewalls for your Data Center environment with close architecture and your requirement is of segmentation for both east-west and north-south traffic then ideally you will connect with your Border Leaf Switches only depending on your Data Center Network Architecture.
Another factor is to keep in mind that once you decide what devices you will connect your firewalls with, you need to ensure the connected device interface bandwidth/speed, type (fiber/copper) must be in line with the Firewall interfaces. For example, you decided to connect your Firewalls with Borer Leafs in your Data Center but if the Firewall has 1/10G copper as well as fiber interfaces and the Border Leafs has 40G fiber interfaces only, then again you are in trouble. So, it is important to keep in mind the connected devices’ interface bandwidth and type.
Another important consideration is to factor in the right transceivers between the Firewalls and connected devices to ensure the link works after you did the connectivity. For example, the Firewalls have 1/10G fiber interfaces which you are planning to connect with the Border Leaf switches in your DC which is also having 1/10G fiber interfaces. Now if you have an SFP-10G-SR transceiver on your Firewall and SFP-10G-LR is available on your Leaf switches, then it won’t work.
You need the same SFPs/transceivers on both sides. Another example could be you have a Firepower 4100 series chassis which has only 1/10G fiber interfaces but the other end device is a WAN edge switch which has only 1G copper interfaces, then in that case of course you cannot connect with fiber cable but you can factor GLC-TE transceiver which provides 1G copper connectivity on 1/10G fiber interface, so you can use GLC-TE on Firepower chassis 1/10G fiber interface and can connect with the WAN edge switch with copper cable.
Cisco has an online tool to check the supported transceivers with the network modules and the specifications of each transceiver. You can check as per your device/module. Below mentioned is the link.
Tip- Always check the installation guide of the hardware Firepower chassis and FMC Appliance to know the available and optional interfaces/modules supported on the device.
Software Version
One of the most important considerations is the Software version when you are deploying any device whether it is a firewall, routers, switches. Have you ever faced any situations where you have configured everything correctly but still the things are not working as expected? Probably, there could be a software bug. To avoid any such situations, always have your software upgraded to the most recommended version/patch.
The rule applies to Firepower FTD software code as well. The simplest way is that you go Cisco Software download portal, find and select your hardware/software, and look for a star-marked version/patch. Below mentioned is the link to the Cisco software download portal and also the screenshot to see the recommended version. Cisco Software Download Portal
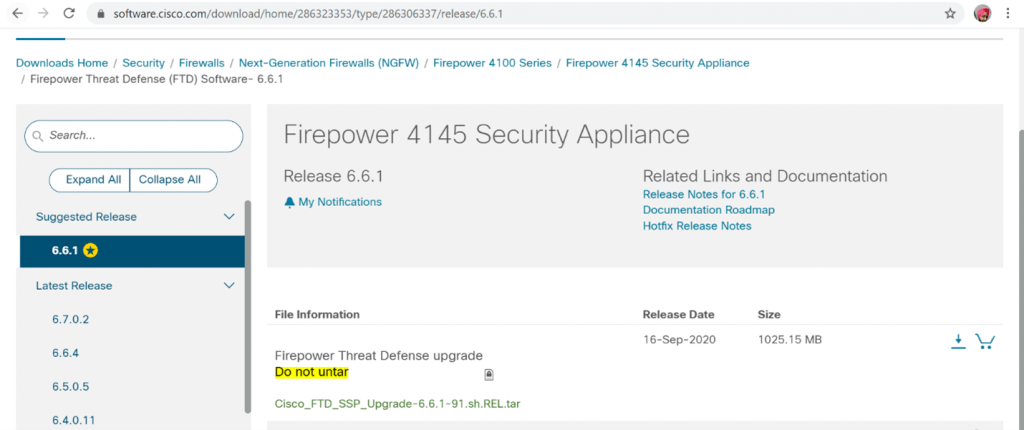
In the above image, we checked for the FTD version on Firepower 4145 chassis and we found 6.6.1 is the suggested release/version by cisco for FTD. Similarly, you can look for FXOS recommended version as well and use the same. Trust me, your life would be much easy.
High Availability
Fault Tolerance is one of the important aspects of any good design. Cisco FTD supports 2 kinds of fault tolerance methods i.e. High Availability and Clustering. In a Layman term, the High Availability option is Active-standby where one out of 2 Firewalls is Active and inspecting the traffic whereas the second firewall is on standby, no user traffic gets passed to the standby firewall. The moment Active Firewall goes down, the Standby firewall gets active and takes over the responsibility of passing/inspecting the traffic. HA is only supported for 2 firewalls. All FTD types whether virtual or physical supports HA.
Another option is Clustering which makes 2 or more firewalls into 1 single cluster and all firewalls in the cluster perform user traffic forwarding and inspecting. Cisco Firepower supports up to 6 units in 1 single cluster. Of course, there are pros and cons for both the options i.e. HA and Clustering. Clustering provides you more aggregated throughput and features like spanned ether-channel which utilizes the maximum number of interfaces across the chassis in a cluster for better bandwidth but at the same time, there are few protocols/features which are unsupported on clustering like Remote Access VPN (SSL and IPsec VPN), DHCP server, Integrated Routing & Bridging and few more.
So, make sure if you are planning to deploy FTDs in a cluster, ensure that you are not going to use any of these features which are unsupported on clustering. On the other hand, HA supports all the features.
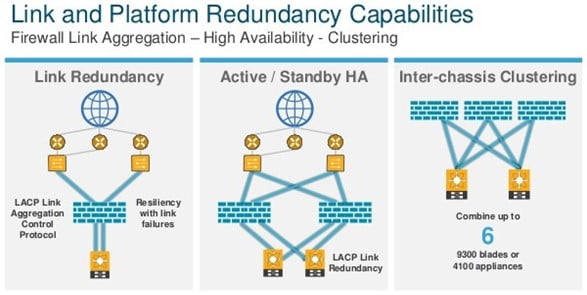
Important point is that as of now clustering is supported only on Firepower 4100 and 9300 series chassis. Chassis less than 4100 series will only support HA.
We will always recommend choosing HA if you have 2 firewalls and enough throughput is factored on each FTD unit to handle the traffic in your environment by a single FTD unit. Otherwise, you can go for clustering.
You can Configuring HA on FTD and click here if you want to Deploying a Cluster for FTD.
Licensing
Last but not the least, as you know that Cisco FTD is a Next-Generation Firewall so it supports advanced features like URL filtering, Advanced Malware Protection, Intrusion Prevention, VPN, etc. Also keeping in mind that FTD supports smart licensing, so you would need a Smart Account to register for licenses. Cisco’s Presales Engineer can help you in setting up a Smart Account.

Below mentioned are the major subscription/license types as a part of Cisco’s offering for FTD and FMC Solution.
- FMCv– Hardware FMCs do not require licenses but virtual FMC does require a license for each FMCv appliance.
- Threat– Threat subscription for Intrusion Prevention. Without this subscription, you cannot use intrusion prevention policies on FTD nodes.
- URL Filtering– This subscription is required to create access rules based on URLs.
- AMP– This subscription provides a Malware license which is used for Advanced Malware Protection.
- TC– This subscription is a combination of Threat + URL Filtering features.
- TM– This subscription is a combination of Threat + Malware features.
- TMC– This subscription is a combination of Threat + Malware + URL Filtering features.
As per your requirement and your environment, you can decide what Firepower licenses you need.
Need help in Planning, Designing, and Implementation of Cisco FTD?
If you are planning for a Tech Refresh, Migration from your legacy Firewall to Cisco NGFW (FTD), or for implementing advanced features in your already deployed Cisco FTD. You can always reach out to us, the team at Zindagi Technologies consists of experts in the field of Cyber Security, Campus/Data Centre technologies, Service Provider Networks, Collaboration, Wireless, Surveillance, private cloud, public cloud, Openstack, ACI, storage and security technologies with over a 20 years of combined industry experience in planning, designing, implementing and optimizing complex Data Centre and cloud deployments. We will be glad to help you; you can also call us on +919773973971.
Author
Harpreet Singh Batra
Consulting Engineer- Data Center and Network Security
