Deep Dive into WSA Policies
Hi guys, we are here to dive into WSA (Web Security Appliance) Policies. You may be good or new to WSA but if you want to be a hero in WSA then we recommend this Blog. Please check it out.
In this blog, we will talk about only the policies of WSA and from this, you will know what is suitable for your network and how can you achieve it.
Policy – A Simple Word but Important Role
What do you understand by the policy? The policy gives direction, accountability, and clarity on how a device manipulates the traffic. Using policies, an administrator can define the allowed or blocked websites as per the organization’s requirements.
When we are saying about allowed or blocked websites then it means that an administrator can create rules/policies in WSA (Web Security Appliance) to allow/block the websites. The result will affect endpoints/subnet which we defined in WSA. We will see how many policies and types of policies to implement the same.
There are 3 types of policies in Web Security Appliance: –
1. Identification Policy
2. Access Policy
3. Decryption Policy
Identification Policy
Identity policy is used to identify the traffic by groups, so other policies can be applied based on the identification policy.
When a user tries to browse the internet then the request comes to WSA, which checks the identity of the request by IP address, Active Directory Group, and user.
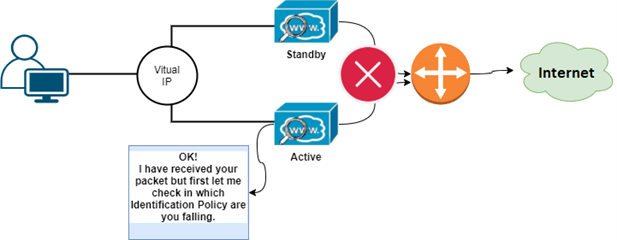
WSA checks the Identification policy from top to bottom.
With the help of the Identification Policy, we can also set authentication and browser (User-agent) as well to access the internet.
If you are creating 2 identification policies. One for without authentication and second for authentication then you should place a non-authentication policy on top.
If the request does not match in any created Identification policy, then it will match to Global Identification Policy.
Access Policy
Here comes on that Policy, in which most of the administrators are interested because this is the place where we allow and block the websites/URL.
With the help of Access Policy, a security engineer allows or blocks the websites as per the organization’s requirements like: –
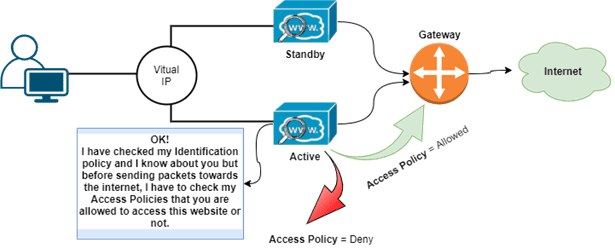
- Block Social sites for the technical team but at the same time, it allows for the HR or Social media handling team.
- Block Media sites for all the employees but allows for party organizers team or maybe for visitors of the company.
- Block Illegal sites for the whole network.
- Allow Corporate related sites for all the employees etc.
We can also create different access policies as per department or requirement with the help of the Identification Policy.
Any HTTP or HTTPs traffic matches only one access policy, it also checks from top to bottom.
In Access Policy, if traffic does not match in any created policy, then it will be matched to Global Policy.
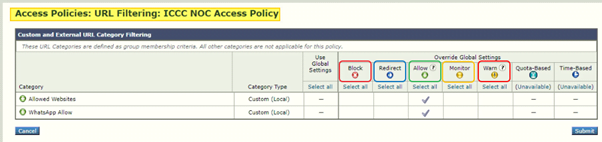
Access Policy has many actions, which will be implemented as per requirements. The actions are as follow:
- Block – Drops all the traffic.
- Redirect – Redirect the traffic to different URLs.
- Allow – Allow all the traffic.
- Monitor – Allow the traffic but checks everything.
- Warn – Show warning page to end-user, user need to click on the continue button to access the Website/URL.
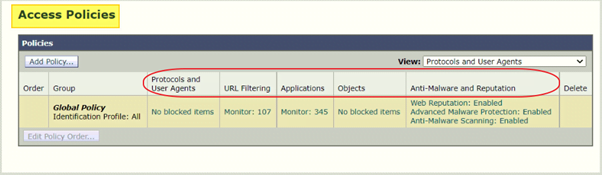
You will see 5 columns in every access policy, which is basically control over policy and the 5 sets are: –
- Protocols and User Agents – Which protocols, Ports, and User-Agents you will be allowed.
- URL Filtering – You can filter Custom URL categories as well as predefined categories.
- Applications – It works just like the name. You can filter base upon applications.
- Objects – You can define Object size and MIME types.
- Anti-Malware and Reputation – It checks the Cisco cloud for malware checks and scanning.
Decryption Policy
This is the last but not the least policy of the WSA. The major role of this policy is to treat HTTPS traffic. As like earlier, we can create this policy as per requirement for different groups and subnets for different actions.
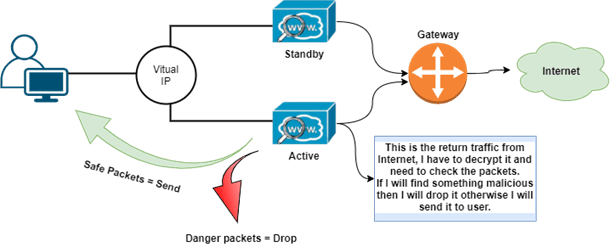
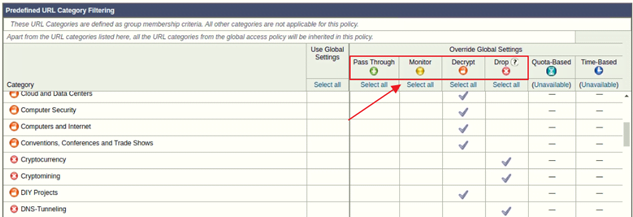
We can monitor HTTPS ports as well and when we configure Proxy for HTTPs traffic then WSA will act as an SSL proxy and maintains a connection with both the ends (Client to Proxy and Proxy to Web Server). Decryption Policy has multiple actions where we can choose 1 action for 1 category. All the actions are:
- Pass Through – If you don’t want any decryption then select this action, for e.g. Banking Sites
- Monitor – It Decrypts the traffic and monitors other things also.
- Decrypt – Allow the connection but decrypts the traffic.
- Drop – Drop the connection.
When WSA decrypts the traffic then it sends the traffic towards the user.
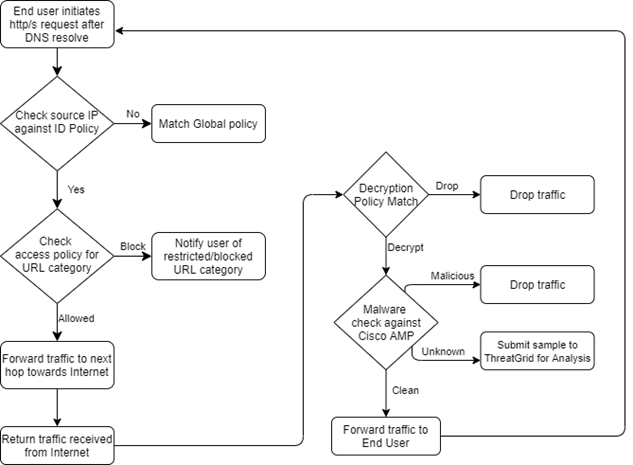
With the help of the below-mentioned diagram, you can understand the packet flow of Web Security Appliance. We have not included DNS resolve packet flow in this diagram because DNS query will go direct and, in this blog, we are focusing only on WSA. Follow this diagram after DNS resolve.
We recommend you deploy WSA in your network to secure or restrict the network. We hope that we clear your doubts and make it simple to understand the WSA policies and now you know very well that how to play with WSA.
Zindagi Technologies has expertise in deploying Network and Security devices. We offer planning, designing, and implementation with proper KT and Documentation. You can contact us at Zindagi Technologies and call us at +919773973971.
Author
Jagjeet Singh
Senior Network Security Consultant
