HA process in FortiGate firewall using FGSP – Explained in Detail.
Hi guys, in this series of blogs, we will talk about different FortiGate HA protocols. FortiGate has different HA protocols FGCP and FGSP.
In this blog, we will understand more about FGSP protocol i.e FortiGate Session Life Support Protocol. FGSP was introduced in Fortios 5.0 and above to overcome the HA restrictions over asymmetric traffic, TCP, UDP, ICMP sessions as well as NAT sessions. It also supports configuration synchronization between two Fortigate Firewalls. The use of traffic load-balancers to share the load across two FortiGates is possible with FGSP. FGSP is well suited for networks using equal-cost load balancing of links between routers. Also called equal-cost multi-path (ECMP) routing or multipath routing.
FGSP can be used for both sessions synchronization and configurations synchronization between two FortiGate firewalls.
Deployment Requirements
Two entities (either standalone Fortigate Firewall or FGCP clusters) can be integrated into the load balancing configuration using the FGSP protocol.
- There is no clustering between the devices
- FortiGate configuration sync must be configured to sync.
- The model and Fortios version should be the same for both devices.
- Only specific VDOMS can sync the sessions.
- You cannot configure FGSP HA when FGCP HA is enabled. However, FGSP HA is compatible with VRRP
- Fortios version should be above 5.0.
There can be a performance issue if one device goes down as all the traffic will be routed towards a single device.
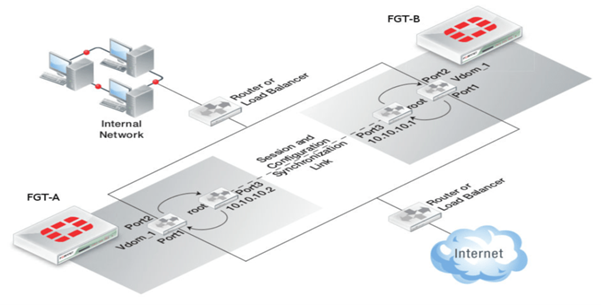
Configuration’s requirements
- FGSP parameters are configured through CLI only.
- The best practice is to reset both the FortiGate devices to factory mode.
- Both the FortiGate interface ips should be different. As shown in the above figure FGT- A has interface 3 with ip address – 10.10.10.2 and FGT-B has interface 3 with ip address- 10.10.10.1
Configuring Session Synchronization peers between two firewalls
First of all, we need to configure Ips to the interfaces of both the firewalls that you can do from both GUI and CLI. I will explain here the CLI method
For FGT-A
system config interface
- edit port3 // To edit port configurations
- set mode static //To set interface DHCP to static
- set ip 10.10.10.2/24 //To set IP address of interface
- end //To save the config
For FGT-B
- system config interface
- edit port3 // To edit port configurations
- set mode static //To set interface DHCP to static
- set ip 10.10.10.1/24 //To set IP address of interface
- end //To save the config
After configuring the ips to the interfaces now we need to configure the session peers to sync there VDOMS
FGT-A:
- config system session-sync
- edit 1
- set peerip 10.10.10.1 //IP of the interface on the peer unit that is used for the session synchronization link.
- set peervd “root” //VDOM that contains the session synchronization link interface on the peer unit.
- set syncvd “vdom_1” //Sessions from these VDOMs are synchronized using this session synchronization configuration.
- end // To save the config
FGT-B:
- config system session-sync
- edit 1
- set peerip 10.10.10.2 //IP of the interface on the peer unit that is used for the session synchronization link.
- set peervd “root” //VDOM that contains the session synchronization link interface on the peer unit.
- set syncvd “vdom_1” //Sessions from these VDOMs are synchronized using this session synchronization configuration.
- end // To save the config
The peervd of root tells the FortiGate that sessions will be synchronized using the root VDOM as the transport mechanism. The peerip IP address must be in the same VDOM as the peervd setting. In the above figure, the port3 is in the “root” VDOM.
When VDOMs are not enabled the peervd setting defaults to “root” and is only visible using “show full-configuration”. If VDOMs are not enabled the peervd setting defaults to root.
FGT-A:
- config system session-sync
- edit 1
- set peerip 10.10.10.1 //IP of the interface on the peer unit that is used for the session synchronization link.
- set syncvd “root” //Sessions from these VDOMs are synchronized using this session synchronization configuration.
FGT-B:
- config system session-sync
- edit 1
- set peerip 10.10.10.2 //IP of the interface on the peer unit that is used for the session synchronization link.
- set syncvd “root //Sessions from these VDOMs are synchronized using this session synchronization configuration.
Enabling configuration Synchronization between the peers. Configuration Synchronization in FGSP synchronizes firewall policies, UTM policies, etc, and all other features. By default, the configuration synchronization is disabled, and interface IP addresses and BGP neighbour settings, are not synchronized so each FortiGate unit maintains its identity in the network. To enable the configuration synchronization in CLI, you need to run the below commands on both FortiGate firewalls.
FGT-A:
- config system ha
- set standalone-config-sync enable
- end
FGT-B:
- config system ha
- set standalone-config-sync enable
- end
A Reboot will be required after the command on both FortiGate’s to enable the command.
Configuring Session Synchronization
Now we need to define in FGSP which sessions they need to share between the FortiGate firewalls.
FGSP synchronizes IPv4 and IPv6 TCP connections by default.
For UDP, ICMP, expectation (asymmetric sessions), and NAT sessions we need to enable them on the device, All the configuration is done in HA system settings.
Session pickup must first be enabled. Different session synchronization commands need to be run to be defined as per the requirements.
To configure synchronization of NAT sessions: –
- config system ha
- set session-pickup enable
- set session-pickup-nat enable
- end
To configure synchronization of UDP and ICMP sessions: –
- config system ha
- set session-pickup enable
- set session-pickup-connectionless enable
- end
To configure synchronization of asymmetric sessions (if you have asymmetric routing configurations you can synchronize asymmetric sessions by disabling anti-reply): –
- config system ha
- set session-pickup enable
- set session-pickup-expectation enable
We can also configure a session filter that will help us synchronize specific traffic.
For example, only sessions for specific IP addresses can be synchronized. In the below configuration, the traffic sessions only from sourced ip 192.168.1.50 to 172.16.1.50 would be synchronized. The rest traffic will not be synchronized.
- config system cluster-sync
- edit 1
- config system session-sync-filter
- set srcintf ‘interface name string’
- set dstintf ’interface name string’
- set srcaddr 192.168.1.50 255.255.255.255
- set dstaddr 172.16.1.50 255.255.255.255
- end
You need to configure the commands on one FortiGate and it will be synchronized to both firewalls.
So, in the above blog, we learned about how to configure FortiGate HA using FGSP. We also learned about how can we configure FortiGate HA using FGSP. If you want to read more blogs on Security components (Cisco ISE, Cisco WSA, and FortiGate Firewall) blogs and Beginner and Advance Home Security then please follow the links. If you are planning to deploy a FortiGate firewall for your network, you can always reach out to us, the team at Zindagi Technologies consists of experts in the field of Network Security, Data Centre technologies, Enterprise & Service Provider Networks, Virtualization, Private Cloud, Public Cloud, Data Centre Networks (LAN and SAN), Collaboration, Wireless, Surveillance, Open stack, ACI, storage and security technologies with over 20 years of combined industry experience in planning, designing, implementing and optimizing complex Network Security and VPN deployments. To get in touch with us, you can give us a call at +91 9773973971.
Author
Anshul Sapra
Network Enterprise Consultant

Does not matter
January 3, 2023Anshul you have so many wrong information on this article dated Nov 4 – 2021 !
Please refer to https://docs.fortinet.com/document/fortigate/7.2.3/administration-guide/668583/fgsp and make sure you post correct info.
Zindagi Technologies
January 16, 2023Hello Does not matter, The blog has been updated as suggested.