Overview of Cisco Mobile and Remote Access (MRA)
What is Mobile & Remote Access (MRA)?
Mobile & Remote Access provides end-users video, voice, and chat capability anywhere, on any device, anywhere in the world. This feature went active in x8.1 and gives customers the ability to provide VPN-less access to Jabber and Physical Endpoints. The solution allows Jabber clients to securely traverse the enterprise firewall and access collaboration services deployed on the enterprise network.
Remote Jabber clients will have access to voice/video, instant messaging and presence, visual voicemail, and directory lookup services. Cisco Expressway is an important part of the Collaboration Edge Architecture offering a mobile and remote access alternative to VPN.
Why Transition From Anyconnect VPN To Expressway Firewall Traversal?
AnyConnect VPN
– Layer 3 VPN Solution
– Secures the entire device and its contents
– AnyConnect allows users access to any permitted applications & data
Expressway Firewall Traversal
– Session-based firewall traversal
– Allows access to collaboration applications ONLY
– Personal data is not routed through enterprise network
This is how the architecture looks like using cisco expressway firewall traversal for MRA?
What Features Do You Get From Cisco MRA?
Through the Mobile & Remote Access solution Jabber clients are offered a fully functional client with the following features:
– Instant Messaging and Presence
– Voice and Video Calling Capability
– Access to Visual Voicemail
– Directory Search w/ Photos (UDS)
– Content Sharing
– WebEx Conferencing
The MRA solution provides the following functions:
- Off-premises access: a consistent experience outside the network for Jabber and EX/MX/SX Series clients
- Security: secure business-to-business communications
- Cloud services: enterprise-grade flexibility and scalable solutions providing rich Cisco Webex integration and service provider offerings
- Gateway and interoperability services: media and signaling normalization, and support for non-standard endpoints
- 3rd Party device registrations on Cisco Expressway Core: The endpoints should support SIP/H323
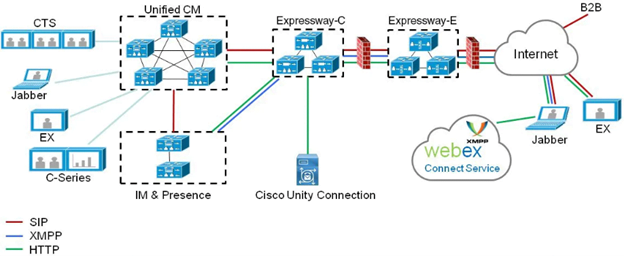
This is how the signaling looks like.
Deployment
Just to give you a high-level idea of deployment, you need to configure all the pointers below.
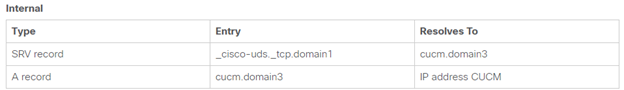
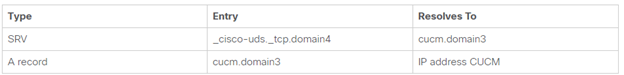
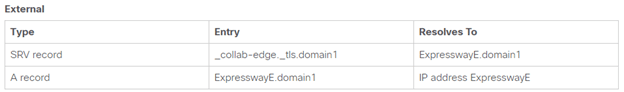
- Setup DNS – A/PTR records for CUCM and Expressway nodes with FQDN entries and service records as below.
Note
-> _cisco-uds and _cuplogin records (used for CUCM and IM PRESENCE) should not be publicly visible.
-> If the customer is doing High Availability the _collab-edge SRV will point to multiple hostnames
- Deploy Expressway Servers via OVA: Just a high-level idea of Virtualization of Expressway Servers.
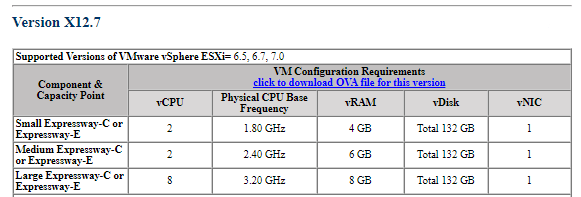
- License the Expressway Servers with option and release keys
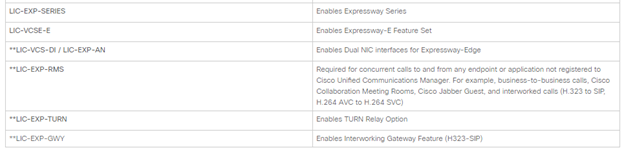
- On Expressway Core, you need the below release keys.
LIC-EXP-SERIES for Expressway Core - And below optional keys.
LIC-EXP-RMS - On Expressway Edge, you need below release keys
LIC-EXP-SERIES for Expressway – Edge - And below optional keys
- LIC-EXP-RMS
- LIC-EXP-AN (Recommended)
- LIC-EXP-TURN
- LIC-EXP-GWY
What Do These Keys Mean?
- Perform Base Configuration of Expressway Servers: NIC configuration, Domain, NTP.
- Gather Requirements for Expressway Certificates
- Expressway-E server certificates should be signed by a public 3rd party CA.
- Expressway-C server certificates can be signed by a public 3rd party CA or an Enterprise CA.
- Expressway server certificates must allow for both client & server authentication.
- Expressway server certificates should not be signed using the MD5 hash algorithm.
- Expressway servers do not support wildcard characters within their certificate although the RFC supports it.
- Expressway-E/C accepts a chained server certificate but uploading it this way, will result in softphone registration failures.
- Configure Mobile & Remote Access Related Features: UC Traversal Zones on both Core and Edge, UC communications mode, add IMP and CUCM nodes (Publisher) to Expressway Core.
- Test Jabber Login
This was just an overview of Cisco Mobile and remote access, although this is a very big topic, I tried to cover major pointers which are required to know for MRA. We hope this article gives you an understanding of the Cisco Mobile and remote access (MRA).
If you are looking for consulting, advisory and professional services to deploy a Collaboration Environment for your organization? Zindagi can help.
Zindagi Technologies Pvt. Ltd. is an IT consultancy and professional services organization based out of New Delhi, India. We have expertise in planning, designing, and deployment of collaboration environments, large-scale data centers, Private/Public/Hybrid cloud solutions. We believe in “Customer First” and provide quality services to our clients always. Call us on +919773973971.
Author
Rahul Bhukal
Senior Collaboration Consultant
