Securing Network Connectivity with IPsec
Our goal as a Network Security Engineer is to be able to provide secure channels of communication over unsecured networks. E.g., the Internet. We have 2 remote offices we are trying to connect or remote users and a central office that we are trying to connect, and we want to make sure that we have privacy in the data that we are forwarding over the public network. Many people confuse keywords like VPN with privacy. VPNs do not necessarily imply encryption, so it does not imply security, just a virtual connection. E.g. an MPLS Layer 3 VPN does not offer encryption.
Why Do We Need Secure Network Connectivity?
There are 2 Offices/Sites between which network connectivity is required so that the network nodes/Clients/Servers in both the sites should be able to communicate with each other. Both Sites are connected over the Internet which is an unsecured network. End Host cannot prevent their traffic from being captured in the cloud. Anything sent in the clear can be reproduced from a packet capture. E.g., VoIP Phone Call. In order to achieve confidentiality of data, Secure Network Connectivity is required.
What Protocols Can Be Used To Provide Secure Channels?
SSL/TLS
– Typically used for Host-to-Host VPNs. E.g. Web Client to Web Servers
– Can be used for Remote Access VPNs. E.g. User accessing Office servers from home via the Internet
IPsec (Our Focus in this blog)
– Typically used for Site-to-Site VPNs. E.g. Remote Office to Data Center
– Can be used for Remote Access VPNs also. E.g. User accessing Office servers from home via the Internet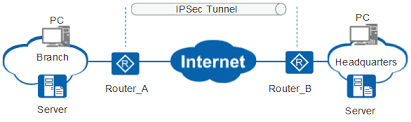
What Is Ipsec and Why Would We Want To Use Ipsec?
Internet Protocol Security (IPsec) is a suite of open standards-based security protocols that allows us to provide secure VPNs by authenticating and encrypting IP Packets between two peers reachable over IP transport.
IPsec is considered to have four main security services, which are as follows.
- Confidentiality – To ensure no one can read the communication in transit.
- Origin Authentication– To ensure the data come from a legitimate source.
- Data Integrity – To ensure the data is not modified in transit.
- Anti-replay– To ensure the data is not already received.
How IPsec works?
IPsec uses symmetric encryption which means the same key is used to encrypt and decrypt the traffic. But the challenge is how do we exchange a secure key over an unsecured network?
This is accomplished using 2 phases of IPSec.
1. Phase 1 IKE/ISAKMP – Create a secure that we can exchange keys over
2. Phase 2 IPsec– Encrypt/Decrypt the packets with the shared key
Read more about how to configure IPsec VPN between Cisco IOS routers.
Are You Planning To Deploy Ipsec VPN Solution Between Your 2 Or More Sites?
If you are planning for a Green-field Deployment, Tech Refresh, Migration from your legacy MPLS or plane GRE VPN to IPSec Solution or for implementing advanced features in your already deployed IPSec Solution then you can always reach out to us, the team at Zindagi Technologies consists of experts in the field of Network Security, Data Centre technologies, Enterprise & Service Provider Networks, Virtualization, Private Cloud, Public Cloud, Data Center Networks (LAN and SAN), Collaboration, Wireless, Surveillance, Openstack, ACI, storage and security technologies with over a 20 years of combined industry experience in planning, designing, implementing and optimizing complex Network Security and VPN deployments. You can also give us a call at +919773973971.
Author
Harpreet Singh Batra
Consulting Engineer-Data Center and Network Security
