Top 5 Ways To Prevent Unauthorized Access
The data breach is one such thing that is seen a lot of times and can be avoided if proper footsteps and practices are followed.
Data is authorized to people who are the part of a company or an organization, but data breach is still happening from outside premises. This can be stopped, and we will give you a few pointers on how you can work on network security.
Always Have A Strong Password
A strong password is your savior as the mix n match of letters and numbers will prove the best. One should follow this practice of a strong password every time. The hackers are intelligent enough that they can gain access to your personal data and can steal valuable information.
Use long passwords with a combination of numbers and case-sensitive letters and this will help in creating a strong password. Always remember the unique your password is the more protected you are from the data breach. Avoid using your name, surname, middle name, date of birth, school name, pet name, or anything that is easily guessed.

Out of laziness and ease of remembering, most people keep their name and date of birth in their password and also the same name as their identification. This gives a window to the attacker as they will seep in from this gap.
Using tools like Identity and Access Management and Enterprise Password Management to be sure that your password is secure and non-breachable.
Two-Factor Authentication
You must know about security questions that are used when you set your password. Generally, they are two questions that will ask you about your first pet name, your school’s name, your maiden’s name, or your birthplace. This is the information that most people know about you and even while you are talking to someone online, they might ask you questions related to these which will make you open to vulnerabilities.
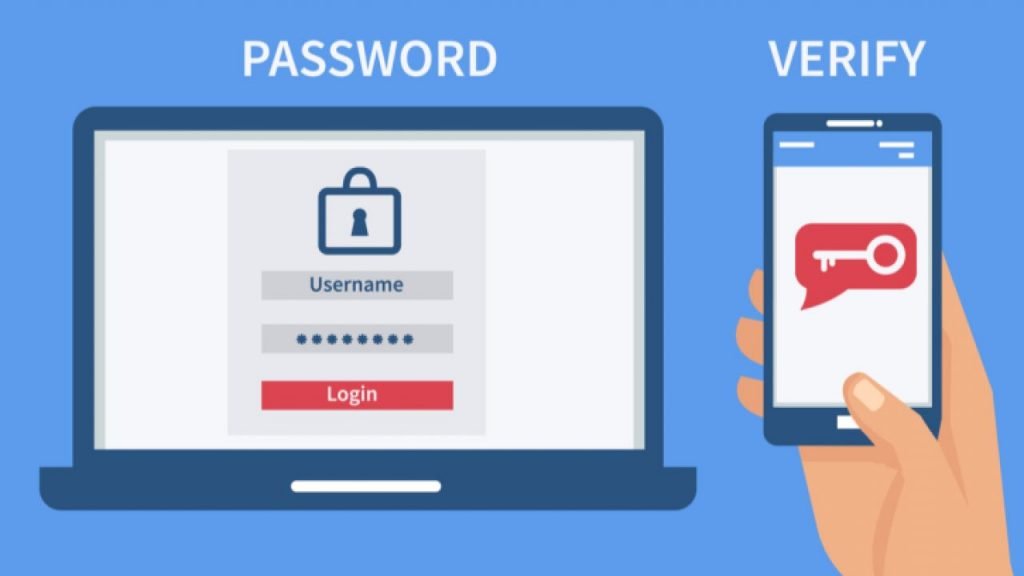
Two-factor authentication is the step that everyone should take if they want to make their data secure.
Possession Factor – The authentication by possessed objects by the user. (Physical Card, Mobile Phone)
Inheritance Factor – The authentication by retinal scan or fingerprint or voice recognition.
Physical Security Procedure
Cybersecurity is more important, but this does not mean that you will forget about physical security. Most people have the habit of writing down passwords and login credentials. This can be a good habit if only the user has the access to the written passwords.
Leaving crucial documents open and unattended or writing down passwords that everyone can see is not the practice that should be followed. This is basic understanding unless it’s uncommon for you.
Monitoring The User Activity
The user would know about their own activities and would have a track of it too but what if you are not checking on a continuous basis. The user should have a close watch on the activities and should know about who and what data has been accessed by others.

A security analyst can access your logs and can gain sensitive information. You should have an alert system so as when another person accesses the data then an alert is generated.
Endpoint Security
Most of the data is breached because of loopholes in the network perimeters. The threat can also be possible when you migrate cloud data from one place to other. The network perimeters give desired drawbacks to the stealer as they target points like workstations, clouds, servers, and other things.

Security endpoint is essential, and a powerful antivirus should be installed at each point as this is the most basic security measure.
However, if you still feel that you are not satisfied with just the antivirus and want more to protect your data then Zindagi Technologies can help you with their disintegrated security services.
Author
Shweta
Senior Content Writer
