WHAT DO YOU UNDERSTAND BY DATA LOSS PREVENTION (DLP)?
Data loss prevention, sometimes referred to as data leak prevention is the practice to ensure that there are no data breaches and sensitive data is not lost or misused. DLP is defined as technologies to perform both content inspection and contextual analysis of data sent via messaging applications, in use on a managed endpoint device, in motion over the network, and at rest in on-premises file servers or in cloud applications and cloud storage.
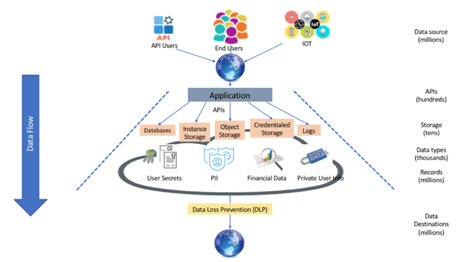
DLP software stops information such as intellectual property, financial data, and employee or customer details from being sent, either accidentally or intentionally, outside the corporate network. Once those violations are identified, DLP generates alerts and encrypts the data to prevent end-users from accidentally or maliciously sharing data that could put the organization at risk.
Gartner estimates that by the end of 2021, 90% of organizations will have implemented at least one form of integrated DLP.
Types Of DLP Products
DLP products are of two types, dedicated and integrated. Dedicated are standalone products, which are in-depth and complex.
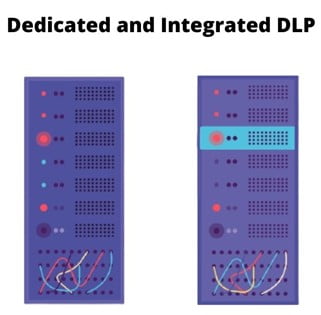
Integrated products are more basic and work with other security tools. They focus on policy enforcement and are less expensive than dedicated DLP tools.
Types Of Data Loss Prevention
Data Identification
Organizations should use automated data discovery and classification tools to ensure accurate identification and categorization of data instead of depending on humans. All data is not equally critical. Organizations have their own definition of critical data. DLP should start with the most valuable or sensitive data that is likely to be targeted by attackers.
Protecting Data In Motion
It is very important to understand how data is used and to identify behavior that puts data at risk. Organizations need to monitor data in motion to gain visibility into what is happening to their sensitive data and to determine the scope of the issues that their DLP strategy should address. Data is moving internally and externally both. DLP software ensures that data is not routed someplace it should not go.
Protecting Data At Rest
This technique secures data when it is not moving, such as residing in databases, computers, mobile devices, and other storage.
Endpoint Data Loss Prevention
This type of DLP functionality protects data at the endpoint device level. It can block data from being copied or encrypt all data as it is transferred. monitor devices such as laptops and smartphones for all data transferring actions such as downloading, printing, copying, or transferring to USB, CD-DVD, MTP devices, Bluetooth devices, and printers. DLP may be configured to actively block specific activities or configured only for passive monitoring.
Data Leak Detection This technique involves setting a baseline of normal activity, then actively looking for unusual behavior.
Personal Information Protection By DLP
Does your organization collect and store Personal Information, Protected Health Information, or payment card information? If so, you are more than likely subject to compliance regulations that require you to protect your customers’ sensitive data. DLP can identify, classify, and tag sensitive data and monitor activities and events. DLP also provides reporting capabilities that can be used for compliance audits.
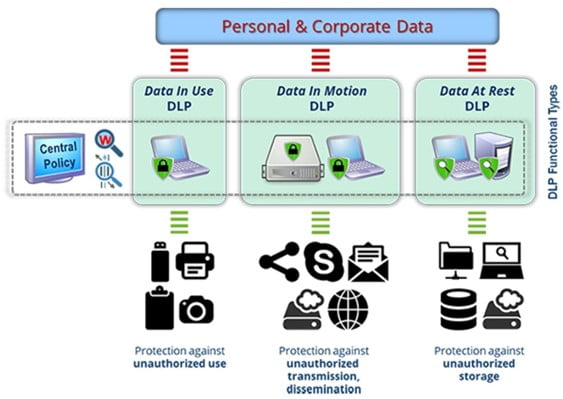
DLP provides a scalable approach by associating data with the source application, the data store, or the user who created the data. Content inspection by DLP is also useful. DLP examines data to identify regular expressions, such as Social Security and credit card numbers or keywords (example: “confidential”). The content inspection often comes with pre-configured rules for PCI, PII, and other standards.
DLP, typically informed by regulatory compliance such as the Health Insurance Portability and Accountability Act (HIPAA), the General Data Protection Regulations (GDPR), or the Payment Card Industry Data Security Standard (PCI-DSS), classifies data as regulated or confidential and then defines violation policies.
Understanding the scarcity of good techs and security talent, our techs at Zindagi technologies will help you. Our technology team at Zindagi Technologies will extend the capabilities to fulfill the security gap that is halting your business. We have round-the-clock security analyst support and we will help you in making sure that you don’t encounter any data leak and will manage your data from start to finish and build a proper protection infrastructure and help you get deployed for the fastest time-to-value. Let’s meet at our office or you can give us a call at +919773973971.
Author
Chakransh Awasthi
Senior Network Security Consultant
