What is Cross-site Scripting and How Can We Prevent It?
What is cross-site scripting (XXS)?
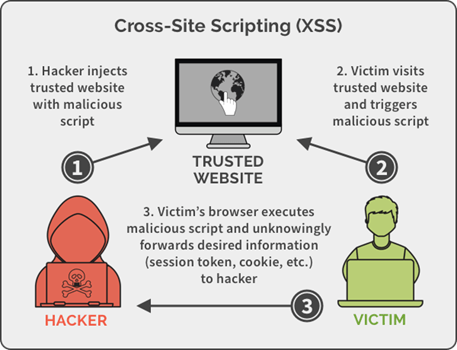
Cross-site scripting (XSS) is a web security vulnerability that allows an attacker to compromise user interactions with a vulnerable application. It allows an attacker to get around the same-origin policy, which is intended to keep websites separate from one another. Cross-site scripting vulnerabilities allow the attacker to imitate a victim user and perform any actions or access any of the victim’s data. If the victim user has privileged access to the device, the attacker will be able to take full control of the app’s functionality and data. It is also done by an ethical hacker to check for vulnerabilities in your website.
How does cross-site scripting works?
Cross-site scripting works by redirecting users to a vulnerable website that contains malicious JavaScript. When malicious code executes in a victim’s browser, the hacker has full control over how users interact with the app.
What are the types of XSS attacks?
XSS attacks can be classified into three categories. These are the following:
- Reflected XSS is a kind of XSS in which the malicious script derives from the current HTTP request.
- The dangerous script is Stored XSS, and it comes from the website’s database.
- The vulnerability is found in client-side code rather than server-side code in DOM-based XSS.
What can XSS be used for?
An attacker that takes advantage of a cross-site scripting vulnerability can usually:
- Assume the identity of the victim user and impersonate them.
- Execute any action available to the user.
- Read any data the user gets access to.
- The login credentials of the user should be captured.
- Deface the website using a virtual defacer.
- Add trojan functionality to the website.
How to prevent XSS attacks?
Preventing cross-site scripting can be simple in some circumstances, but it can be much more difficult in others, depending on the application’s complexity and how it handles user-controllable data.
In general, preventing XSS vulnerabilities will almost certainly require a combination of the following steps:
- Check all your software is up to date – For a variety of reasons, including bug fixes, improved performance, the addition of new features, and the patching of security vulnerabilities, software should always be kept up to date. Updating software on a regular basis would greatly reduce the number of vulnerabilities that leave a site or application vulnerable to XSS attacks.
- Input Fields Should Be Sanitized and Validated -The most common entrance point for XSS attack scripts is input fields. As a result, all data entered data fields should always be screened and validated. To protect against reflected XSS attacks, this is especially crucial if the data will be included as HTML output.
- Firewall for Web Applications – For preventing XSS assaults, a web application firewall (WAF) can be a useful solution. Bots and other harmful activities that may suggest an attack can be filtered by WAFs. Attacks can then be presented before the execution of any script.
- Policy on Content Security – The functionalities that a website is allowed to perform can be defined by a content security policy (CSP). They can be used to prevent in-line scripts from being accepted by a website. This may be the most powerful approach available, as it can totally prevent or considerably minimize the likelihood of XSS assaults.
Now we know how cross-site scripting works and what consequences it can have. The loss of login credentials can lead to a variety of issues, including the exposure of other sensitive information. Some steps to secure your Network Infrastructure are offered above to help you overcome this. You can reach us at or +919773973971 if you wish to secure your network infrastructure, cloud solutions, or data center services.
Author
Shivam Rana
Associate Consultant

5 VAPT testing to secure your data | Zindagi Technologies
April 11, 2023[…] we need to fix and mitigate. Some of the many vulnerabilities that pop up can be SQL injection, XSS cross-site scripting, other types of code injection attacks, faulty authentication mechanisms, insecure settings like […]