What is SD-WAN and Its Controllers?
The term “software-defined wide area network” (SD-WAN) refers to a wide area network that makes use of software-defined network technology, such as overlay tunnels for Internet communication that are encrypted while going to locations inside an organization.
By separating the networking hardware from its control mechanism, SD-WAN makes it easier to manage and operate a WAN if standard tunnel setup and configuration messages are supported by all the network hardware vendors. In practice, proprietary protocols are utilized to set up and administer an SD-WAN, therefore there is no decoupling of the hardware and its control mechanism. This is comparable to how software-defined networking utilizes virtualization technologies to improve data center management and operation.
Controllers in SD-WAN
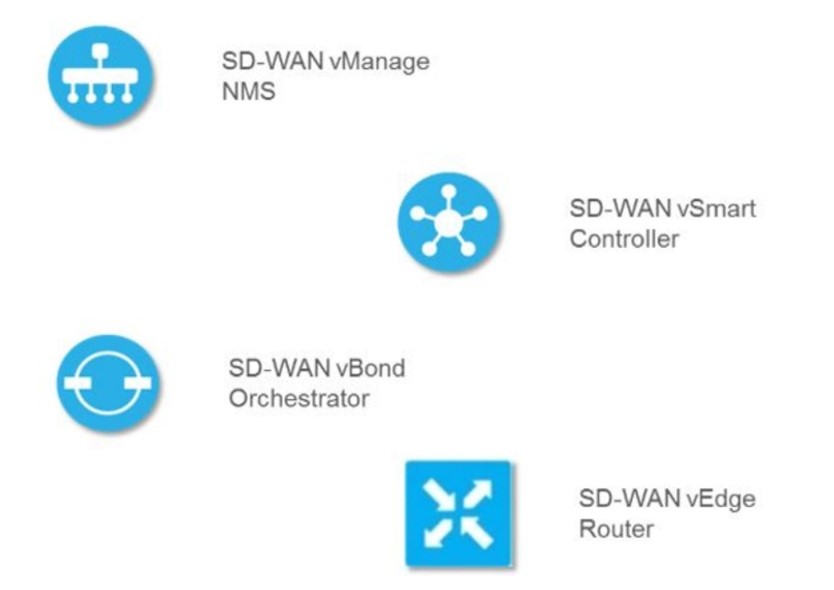
Vmanage
Since vManage is the network management system (NMS), it serves as your system window. You will use the dashboard daily. You can very much compare vManage to the Meraki dashboard if you are familiar with it. It is in charge of gathering network telemetry from our vEdge devices and sending alerts about occasions and outages in the SD-WAN setting. You can create your device settings (Device Templates) and overlay traffic engineering policies there as well. This is also the REST API-compatible system’s programmable interface.
Vbond
For good reason, vBond is regarded as the system’s orchestrator. Its responsibility is to coordinate connectivity amongst all of the other system components. In other words, it directs our vEdges to the vManage and vSmart controllers within our businesses and advises our vSmart controllers as new vEdges join the SD-WAN network. It assists with IPsec NAT traversal and enables the use of Authentication Header security for our data plane tunnels by alerting our vEdges if they are behind a NAT device (more on that in upcoming posts). All SD-WAN components connect to vBond as soon as they boot up and join the SD-WAN fabric, serving as our first point of authentication.
Vsmart
As its name suggests, vSmart serves as the system’s brain. This item is what the architecture’s control plane component is made up of. The data plane policies, security, and routing are all promoted by vSmart controllers. All the vEdges peer with a vSmart, as vEdges never form control plane peerings with one another. They are set up as hub devices in the control plane topology.
Vedge
The hardware or software element that is located at your sites is called vEdge. The only part of the architecture that needs to be deployed if you opt for a cloud-hosted control/management plane deployment is this one. As they set up IPsec or GRE tunnels between your sites, vEdges manage the data plane of the SD-WAN fabric. As previously indicated, rather than between themselves, vEdges build control plane links with vSmart controllers. There are numerous form factors for vEdge hardware. As the model number rises, the key differences are more available interfaces, better-supported throughput, and data plane tunnels.
Zindagi technology is a leading IT consulting company. We have successfully completed lots of IT projects. Our motive is to provide network solutions, cybersecurity solutions, managed IT solutions and other solutions as well that will help your organization to have a better IT infrastructure. We provide IT solutions like cyber security, cloud computing, VAPT, VoIP, etc. We can assist you in your network programs. You can ping us at +91-9773973971 or you can also drop us an email and we will get back to you soon. To follow our updates, you can follow us on LinkedIn and stay in touch with technology.
Author
Lokesh Kumar
Associate Consultant
