What is VLAN Hopping and How it is Performed?
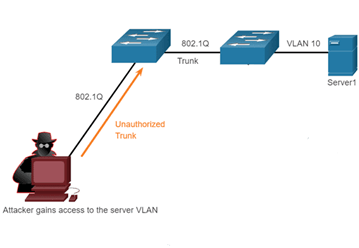
VLAN hopping is a type of attack where the attacker sends traffic from one VLAN to another VLAN. An attacker can then steal passwords or other protected information and install viruses or corrupt, modify, or delete critical data.
How VLAN Hopping Attack is Performed?
VLAN hopping attack can be performed in two different ways: –
- Switched Spoofing
- Double tagging
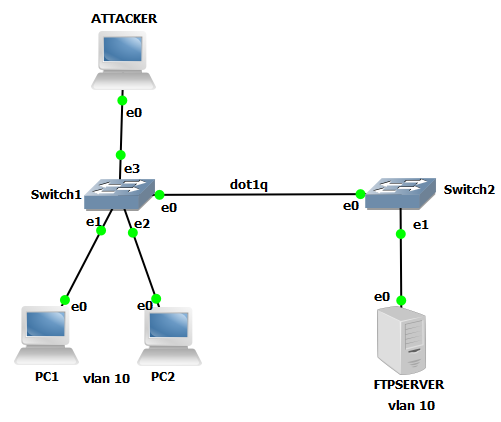
In the above diagram, we have two switches directly connected and the link is trunk mode with Dot1q encapsulation. There are two users on SW1 who are in VLAN 10. FTP Server is connected to SW2 which is in the same VLAN 10.
Attacker connects its pc to switch 1 on port 0/3. An attacker with an intention to corrupt the FTP Server wants to gain access to it. But attackers cannot communicate with the FTP as they are in different VLANs. By default, an attacker is connected on VLAN 1, when it sends data with malware, switch 1 forwards it to the VLAN 1 interface and on the trunk link. Data will reach switch 2 but gets discarded as no VLAN 1 user is active.
As the attacker gets to know FTP Server is on which VLAN, it adds tag 10 with the help of the application. When the traffic reaches switch 1, it checks traffic is received at which VLAN and forwards to VLAN 10 port and on trunk link through native VLAN. On reaching switch 2, tag 10 gets removed and gets forward to the FTP Server and it gets down.
How To Protect The Network From VLAN Hopping?
- Use of ISL encapsulation on the trunk link
When we use ISL as the trunk encapsulation protocol, even if traffic is forwarded through
native VLAN it adds tag of VLAN 1
- Make an unused port member of bogus VLAN
Random VLAN but not a member of VLAN 1
- Add tag at native VLAN even when Dot1q encapsulation is running
By default, no tag is performed at native VLAN for dot1q
Command to add a tag at native VLAN: –
SW(Config)# vlan dot1q tag native
When a tag is performed at native VLAN in dot1q in SW1
EX: –
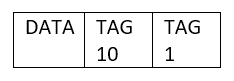
SW2 removes tag 1 and forwards the tagged frame to the users at VLAN 1.
Users will discard the tag frame as they do not understand.
In the next blog, we will see how VLAN hopping is performed with the help of switched spoofing.
Zindagi Technologies is an IT consulting company having engineers with decades of experience in planning, designing, and implementing Data Centers along with Managed IT Services, cybersecurity, cloud services. If you want to secure your network, we are just a call away. Please call or message us on +91-9773973971 or drop a mail at [email protected].
Author
Jainul Khan
Associate Consultant
