5 Types Of Penetration Testing That Will Help In Securing Your Data.
Let’s get straight to some facts related to Cybersecurity and why you should get VAPT:
- $4.24 billion was the average total cost of the data breach in the year 2021.
- This is the highest margin recorded in the past 7 years.
- A 9.8% increase in the average cost of a data breach is expected to multiply over the years.
- Since 2015 data breach costs have been increased by 11.6%.
And you think your data is secured and safe? VAPT assessment is testing IPs and letting you know about the vulnerabilities that are open and can be penetrated.
Data breaches are happening all over the world. It’s scary to think that the top 5 data breaches that happened in 2021 had names like Microsoft software, Facebook, Colonial Pipeline, and more. If you think that your data is safe and secure, then you are absolutely wrong.
You must have heard about a recent incident where a software engineer hacked the website of Indigo airlines when the airline failed to locate his missing luggage. He went ahead like, “let me take care of this myself”.
User trust is something that most company believes in, but data breaches turn out to be a nightmare. Any company that is dealing with services provided to customers then they have the right to be sure that all the information they have of all customers is safe but as soon as a loophole is found, all data is floating with the hacker. We give the best Comprehensive Cyber Security Solution in Delhi keeping in mind the needs of every organization.
It is not so easy to avoid a data breach but you can always keep your guard up by getting the Best Vulnerability Assessment in Delhi. Even with the most advanced software and firewalls, hackers slip through the cracks and proudly sit in the middle with your data in their hands. With the Best Penetration Testing in Delhi, you can be sure of two things
1. All the vulnerabilities that a possibility of a threat and where exactly they are present
2. All the penetrable doors through which the hacker might get in and steal your data.
What do we understand by Vulnerability in VAPT?
To find the weakness of any IP one needs to run a security check. When the security check is performed, all the vulnerabilities are exposed and we can clearly see what we need to fix and mitigate. Some of the many vulnerabilities that pop up can be SQL injection, XSS cross-site scripting, other types of code injection attacks, faulty authentication mechanisms, insecure settings like easily guessed admin passwords, and many more.
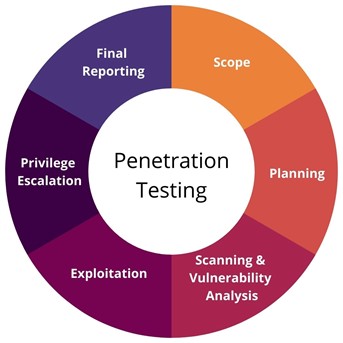
5 Types of Penetration Testing That Can Save Your Data – VAPT
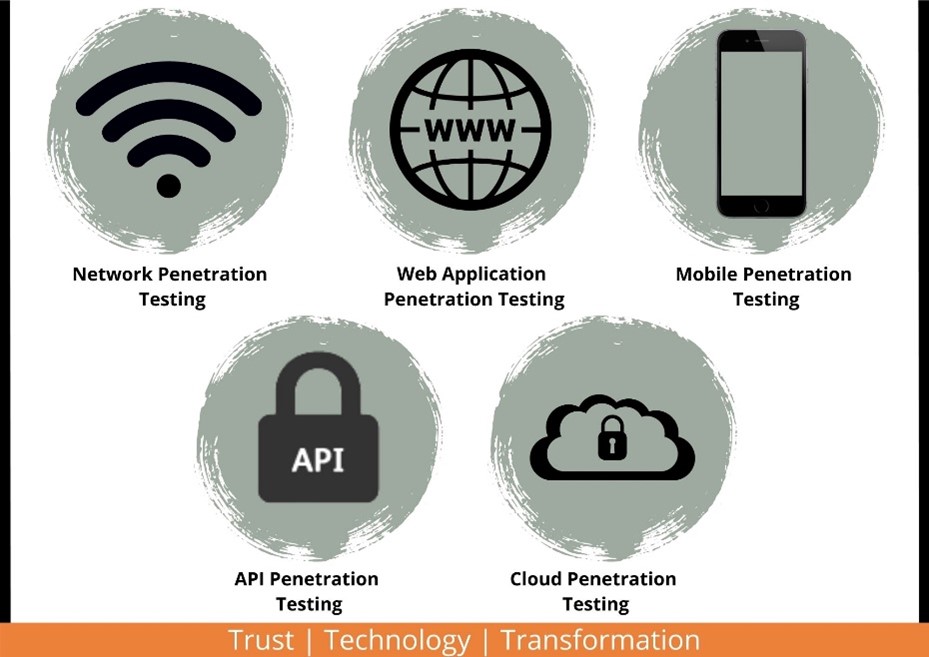
VAPT Network Penetration Testing
A type of security audit that enables you to check the security of the network. Almost all data is on the network and all the cyberattacks and threats are placed on the network only so it’s the best decision for every organization to get the network secured first. The system is stimulated, and the hacker tries to break in to launch a cyberattack. Network penetration testing is done to find the loophole through which the cyberattack was launched and the data was taken out.
Web Application Penetration Testing
You must have heard in the news so many times that XYZ’s website was hacked, and the information was stolen or misused. Web application penetration testing is done to know the security status of your website and know the vulnerabilities that are penetrable. The website loopholes are pointed out so that they can be mitigated, and the website can be made secure.
Mobile Penetration Testing
The application that you have on your mobile takes information about you like mobile number, email id, name, and other information as well. This information is asked by third-party apps which may or may not include face id, fingerprint, and other biometric authentication. Just imagine if the hacker is able to create a fingerprint and can get all your details including your extremely personal information? It’s a lot scary. Mobile penetration testing will allow the user to seal the cracks that are easily penetrable, once shut, the penetration will not happen. Android applications, iOS applications, hybrid applications, and PWA are some testing kinds.
API Penetration Testing
Application programming interface penetration testing is one of the most important security aspects connected to infrastructure. Apart from a single point failure issue, the company’s integrity is a major risk during an attack as the complete infrastructure is leaked. If the APIs used by employees and third-party apps fall into wrong hands then they can be used to spread malware, manipulate company data, and whatnot. API penetration will assess the security of your API as it is becoming the favorite target for cybersecurity.
Cloud Penetration Testing
Since the onset of the pandemic, most companies have transferred their data to the cloud which makes it easy for the person who is anywhere can easily access the information and the related data. The only issue with the cloud is that while you are accessing the information, at the same time a hacker is looking for a loophole through which they can easily get into the cloud and can casually lie in the pool of data.
This penetration test should be performed before the applications and data are moved to the cloud as it is a part of the pre-security process.
Vulnerability assessment is an essential part of the security process that will help the organization in getting all the details of your vulnerabilities that will make it easy for you in getting all possible threat openings. Zindagi Technologies has the best team that will keep your business afloat by removing all the vulnerabilities. Get in touch with our team via message or call on number +91-9773973971. We are experts in giving the right VAPT report and will also mitigate the risks for you. All you have to do is to provide us with the IPs and we can start with the testing and bring out the issues.
Author
Shweta
Senior Executive, S&M

8 Types Of IT Risks & Consequences | Zindagi Technologies
June 13, 2022[…] the corporations. With a clear knowledge of all the challenges, the companies would perform better. Comprehensive Cyber Security Solution in Delhi will help you in risk […]