What Is SQL Injection Attack And How Can We Detect It?
SQL injection attacks are a type of injection attack in which SQL commands are injected into input fields for execution. SQL Injection is listed as the most vulnerable threat for website applications as it can interfere with the queries that an application makes to its database.
What Is The Impact Of A Successful SQL Injection Attack?
A successful SQL Injection attack is really dangerous for an organization as it results in authorization access to sensitive data such as credentials, credit card details, bank account details. Many high-profile data in recent years have been the result of SQL Injection attacks.
How To Detect SQL Injection Vulnerabilities
The majority of SQL injection vulnerabilities can be found quickly and reliably using a web vulnerability scanner
SQL injection can be detected manually by using a systematic set of tests against every entry point in the application. This typically involves:
- Submitting the single quote character ‘ and looking for errors or other anomalies.
- Submitting some SQL-specific syntax that evaluates to the base (original) value of the entry point, and to a different value, and looking for systematic differences in the resulting application responses.
Submitting Boolean conditions such as OR 1=1 and OR 1=2 and looking for differences in the application’s responses.
- Submitting payloads designed to trigger time delays when executed within an SQL query and looking for differences in the time taken to respond.
- Submitting OAST payloads designed to trigger an out-of-band network interaction when executed within an SQL query and monitoring for any resulting interactions.
How To Prevent SQL Injection
Most instances of SQL injection can be prevented by using parameterized queries (also known as prepared statements) instead of string concatenation within the query.
The following code is vulnerable to SQL injection because the user input is concatenated directly into the query:

This code can be easily rewritten in a way that prevents the user input from interfering with the query structure:
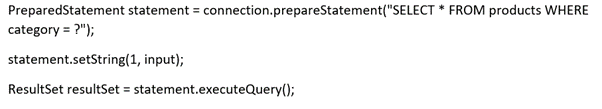
Parameterized queries can be used for any situation where untrusted input appears as data within the query, including the WHERE clause and values in an INSERT or UPDATE statement. They can’t be used to handle untrusted input in other parts of the query, such as table or column names, or the ORDER BY clause. Application functionality that places untrusted data into those parts of the query will need to take a different approach, such as whitelisting permitted input values or using different logic to deliver the required behaviour.
We recommend you check for the OWASP top 10 vulnerabilities using a web vulnerability scanner such as Nessus and monitoring your network from such vulnerabilities which are so critical and can affect your organization awfully bad.
We at Zindagi Technologies are here to help to protect your network from such critical vulnerabilities. We offer Planning, Deployment, Implementation, and Documentation. You can contact us at +919773973971.
Author
Shivam Rana
Associate Consultant

5 VAPT testing to secure your data | Zindagi Technologies
April 11, 2023[…] clearly see what we need to fix and mitigate. Some of the many vulnerabilities that pop up can be SQL injection, XSS cross-site scripting, other types of code injection attacks, faulty authentication mechanisms, […]