How To Prevent The Top Password Attacks?
We will be continuing with our security point of view and this time we bring you a new blog on how you can prevent password attacks. In our previous blog, we discussed the issues of cybersecurity and how they can create havoc on the security of an organization.
Let’s know something about passwords
There is nothing new about passwords as it is a safe combination of letters, numbers, and symbols in upper case or lower case which help you to get into your personal digital space. They are the more vulnerable, most secure, and very valuable set of letters, numbers, and symbols.
In recent times, the passwords of many people have been leaked and a lot of data has been stolen. Password is something that is not easy to guess yet for many hackers, it’s a piece of cake. What are the ways by which the hackers can guess and bring out your password? Here we bring 6 password attacks for you.
Social Engineering
Once in a while, a message circulates on social media saying that a very expensive item is available on Amazon at a very reasonable rate. You click on the link and a similar-looking web page pops up. The webpage is so strikingly similar that you fail to recognize the fake website and end up entering your bank card details. This is the moment that the hacker has been waiting for. In the disguise of Amazon’s actual website, it is a fake website that s waiting for your credentials so the hacker can generate an OTP and can take away your hard-earned money. Also, the hacker will have all your details which can be misused in any way. Another way to steal data is phishing like voice phishing, spear phishing, pharming, and many other elaborated options that have different techniques.
Brute Force Attack

Hackers are very talented, and they find out elaborated ways by which they can steal your passwords. Another type of attack is a brute force attack. This means that the hacker will try to break the authentication by finding out the secret password or by getting an application that will accept a stolen password. How does this work? The hacker will try out all the possible ways to crack your password by cracking or by applying guessing schemes. This is why people are asked not to keep their passwords like date of birth, dog names, parent names, middle name, sibling names, first school, or any specific word or phrase that you speak often (Saw Ajnabee? How cleverly Bobby Deol logs in the bank account of Akshay Kumar?). Keeping very common passwords or similar to your email ids is like the holy grail for the hackers.
Credential Stores

Do you have a habit of saving your passwords when any website prompts you to save yourself from entering the password again and again? You should probably rethink your habit. Many people also keep the passwords of e-commerce sites and email ids the same to ease access. This is the biggest mistake you are doing. Keep a list of passwords and enter the passwords as many times as you are asked without saving them in the cache. The hackers are very clever and compromise the credential stores to steal your passwords. Now imagine if you have kept the same password for amazon as your google then the hacker can have the access to not only your personal details but your card details too.
MITM (Man In The Middle)
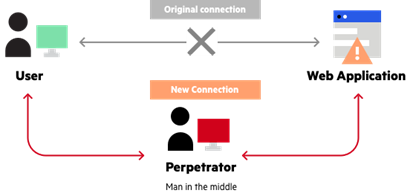
Hackers find many ways to come in between you and the source just to steal your data and your personal information. This is called the man in the middle. They place themselves in the middle of the user and the connecting application by intercepting the network traffic. The next step is to extract the password exchanged between both. Not just the password is leaked but the personal information like your name, date of birth, Aadhar number, or PAN card number might leak too. This is something different than network sniffing but in this, the attacker can tamper with the communications like a middle-man.
Everyone says stay safe but it is important to make your credentials safe too. Using passwordless authentication is just a superior way of securing passwords but more secure options will be given by Zindagi Technologies.
Zindagi Technologies is an IT consulting company with experienced techs and will provide complete security to your organization at the utmost level. Not everyone gives this type of best security than Zindagi. Switch to Zindagi Technologies if you feel that your IT provider is not doing justice to its role. If you feel like you are wasting your money on your current IT provider, then it’s time to give a chance to Zindagi Technologies and see the difference.
Author
Shweta
Senior Content Writer
