What Are The Features Of Port Security And How Does It Works?
Basically, port security is used to protect our LAN interface from the attacker. The attacker may be anyone in the organization or outside.
- You can allow mac addresses manually
- You can change or allow the maximum number of the mac address.
- If you do not configure manually, in that condition switch will allow the first source mac address
That enters the interface.
- You can use a combination of manually configured mac addresses and as well as dynamically learned add is possible.
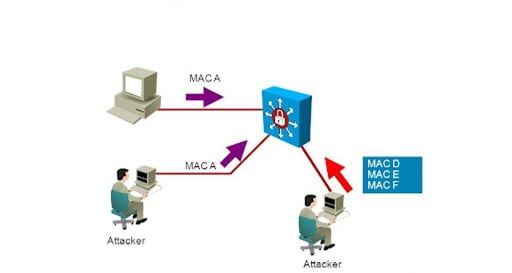
How Does Port Security Works?
First whenever you enable port security on an interface with the default configuration, that time
Only one mac address is allowed. If any other mac address learns on that interface, then the port goes to the err-disable state.
There are three types of Methods of port security
- Static Method
- Dynamic Method
- Sticky Method
- Static method– if we talk about the static method. we can add or remove the mac entry from the mac address-table by manually.
- Dynamic method – secondly, we will talk about the dynamic method as it can be learned One mac (1-1024) address defaults automatically.
- Stick method –it is the same as the dynamic method, but one difference is you can set the learning limit of the mac address. Another rule of it is first come first receive.
Violation Mode Of Port Security
- Shutdown
- Restrict
- Protect
- Shutdown Mode
Effectively shuts down the port by placing it into an err-disabled state.
Generates a log and SNMP message, whenever the interface is disabled.
The violation counter is set 1 when the interface is disabled or default 0.
- Restrict Mode
The switch will discard traffic from an unauthorized mac address.
That interface is not going to a disabled state.
The violation counter is incremented by 1 each and every unauthorized frame.
It is also generating log and SNMP messages each and an unauthorized frame.
- Protect Mode
It does not generate any time syslog or SNMP message for unauthorized traffic.
The interface is not disabled.
The switch discards traffic from an unauthorized Mac address
Configuration Steps
Step 1. enable port security
Switch(config)#interface fa0/1
Switch (config-if) #switchport mode access
Switch (config-if) #switchport port-security
Step 2. define the allowed no of the max mac address.
Switch (config-if) #switchport port-security maximum 1
Step 3. choose the static dynamic or sticky method
Switch (config-if) #switchport port-security mac-address sticky/H.H.H.H
Step 4. set the violation mode
Switch (config-if) #switchport port-security violation shutdown/Restrict/Protect
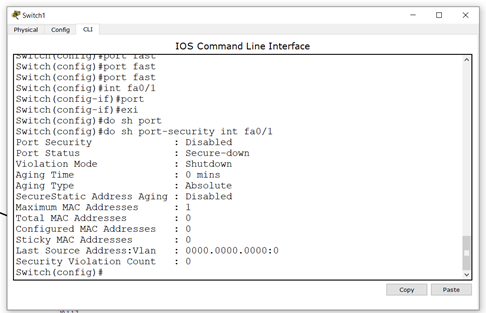
Some verification command
Switch#show port-security address
Switch#show port-security interface fa0/1
It is great! We learned about a very basic and important feature of the cisco catalyst switch.
Those are very simple steps.
We at Zindagi Technologies are experts in the data center, security network, designing and planning of architecture of the network, etc. we have very good experience in these fields.
You can keep in touch with us by the blog. If you have any questions or you want to share your view
Then you are free to ask. We have good experience in data centers, IT consulting, Managed it service.
Cyber security, cloud solutions, and many more. You can also give us a call at +919773973971 or [email protected] and visit our website.
Author
Anuj Kumar
Associate Consultant
