The Emerging Need For Micro-Segmentation In Today’s Time.
The need for micro-segmentation has been emerging in the market ever since its introduction and it has been quite a buzz. But why do we care about micro-segmenting our network? Before coming to why we need it, we first need to know what micro-segmenting your data center means.
What is Micro-Segmentation?
Micro-segmentation is a technology that enables the security team to logically divide their network into distinct segments. The data center is broken down into several logical segments based on the workload level and then services are delivered to each segment accordingly.
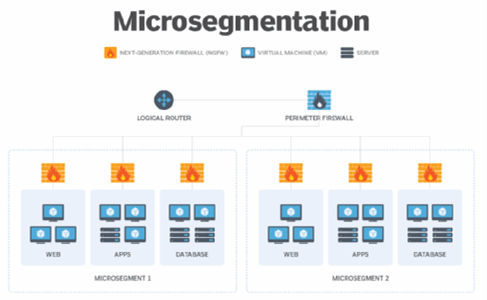
Micro-segmentation provides flexibility to the enterprises by allowing the security experts to apply flexible policies with the help of network virtualization, preventing them from the cost of deploying multiple physical firewalls which an enterprise might have to bear.
In a traditional architecture where let us say we have three VMs for an application, namely, App VM, DB VM, and Web VM. You may have these virtual machines running in a different subnet and whenever these virtual machines would want to talk to each other, then the traffic would go out to the switch and then our physical firewall would determine if these virtual machines could communicate of specific ports and it would allow the traffic accordingly. If these virtual machines were in the same subnet, then the perimeter firewall would not even come into the picture.
In an architecture where we use micro-segmentation, we disperse out our firewall rules and apply them at the virtual machine level which means that all the east-west traffic will only be allowed/blocked at the virtual machine itself. This is achieved by installing a distributed firewall at the virtual machine level.
It provides the flexibility of creating firewall rules based on Security Groups, IP Sets, Clusters, Data Center, Distributed Port Group, vNIC, Virtual Machine, etc. the security architects can create the most granular rules with these options and deliver pre-defined services on specific ports or they can manually create their own services template and apply it at the group level on virtual machines. Since the firewall policies are applied at the vNIC level, the policies stay intact and tied to the Network Interface Card of the virtual machine even after vMotion from one host to another.
There are several OEMs providing a micro-segmentation solution, VMware NSX has proven to be one of the best solutions leading the Gartner Magic Quadrant.
What is a Distributed Firewall?
A Distributed Firewall (DFW) resides inside the kernel of an ESXi host or a cluster of ESXi hosts which are configured for NSX. DFW runs as a VIB package at the kernel level of ESXi hosts. Since it is a kernel-embedded firewall, it provides visibility over the virtual workloads and allows us to enforce policies at the vNIC of the virtual machine.
Micro-segmentation solutions work on zero-trust security by creating micro-segments at the virtual machine network interface card (vNIC) level, enabling every virtual machine to have its own firewall.
NSX Manager monitors and enforces policies on the virtual machines at the vNIC level. It provides a single pane of glass to view policies configured at every DFW instance.
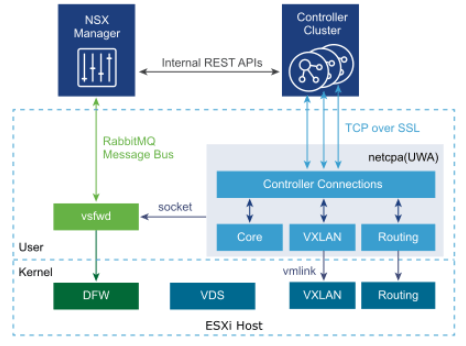
The diagram above illustrates the user and kernel space in VMware NSX. The NSX Manager and NSX components residing in ESXi hosts communicate with each other through a RabbitMQ broker process. It uses Advanced Messaging Queuing Protocol (AMQP) to communicate with each other over a secured channel using SSL. vShield Firewall Daemon (VSFWD) is a process that runs on the ESXi hosts and is responsible for maintaining the SSL connection with the broker.
To sum it up, Micro-Segmentation has evolved over the last few years and can clearly be seen as one of the mainstream technologies in helping you prepare and plan your data center to be more resilient towards attacks.
If you are planning to build an irrepressible and robust data center and you are looking for Planning, Designing, Implementation, and PoC services, Zindagi Technologies has a team of security architects who have expertise in Micro-Segmentation solutions. For more information reach us at [email protected] or give us a call at +919773973971.
Author
Sumit Yadav
Data Center Consulting Engineer
