Digitization is happening all over the world and all you need is the right tools in this case the organization needs a Top IT Consulting Services company. There are many things that are important in digitization and only a professional can help the organization. The resources, expertise, and all the transformation tools that are required for […]
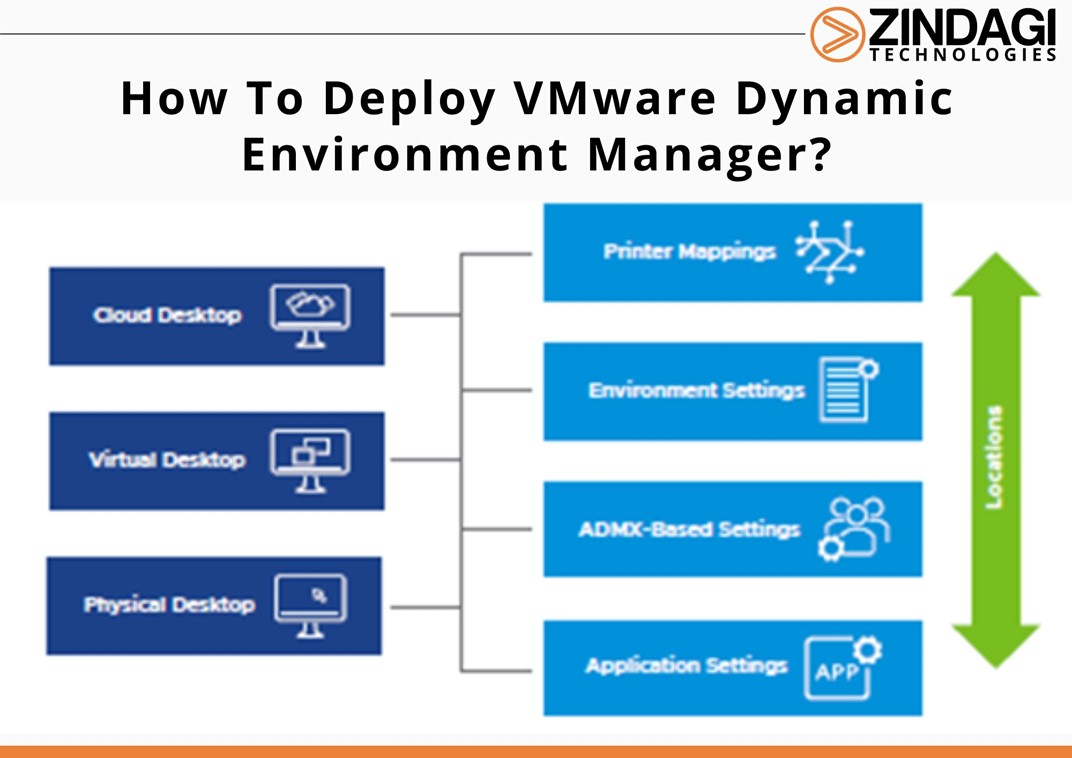
VMware Dynamic Environment Manager (DEM) is a user environment management tool that allows administrators to control and personalize the user experience in virtual desktop infrastructure (VDI) and Remote Desktop Services (RDS) environments. It provides a centralized management console that allows administrators to configure and manage user settings, policies, and application entitlements across multiple virtual and […]
Switching to the cloud or cloud migration is nothing new and if you are also planning to then you are one of the many who are following the steps. New trends in cloud computing technologies have been introduced by AWS and IaaS and companies like Netflix, Coca-Cola Adobe, Salesforce, and Samsung are slowly following the […]
Basic Overview of LDAP LDAP, or Lightweight Directory Access Protocol, is an authentication protocol that is commonly used for accessing and managing information in a directory service. A directory service is a centralized database that stores information about users, groups, and other network resources. LDAP provides a standardized way for applications to access this information […]
This blog is a continuation of the What is Wi-Fi Heatmap and Wireless Parameters Series. In Part 1, we discussed Heatmaps and basic Wireless Parameters. In the second part, we will continue with the first steps to a Wi-Fi network Design and considerations. Wi-Fi Design Wi-Fi design is the process of taking your business requirements […]
UCS CIMC Port Configuration Step 1: A keyboard and monitor to the USB and VGA ports on the appliance’s rear panel or A KVM cable to the KVM connector on the appliance’s front panel. Step 2: Make sure that the appliance power cord is plugged in and the power is on. Step 3: Press the […]
NetFlow is a protocol developed by Cisco, used to collect metadata on Ip (Internet Protocol) traffic flows passing through a network device. A NetFlow-enabled device generates metadata at the interface level and forwards flow data information to a flow collector, where the flow records are stored to enable network traffic analytics and management. A NetFlow-enabled […]
Time and money are the two most important values of any business and DevOps is the way to save time and money. Development and operations are the integration of all processes. The processes include quality assurance, verification, IT activities, testing and software development. These implementations are done so that overall efficiencies are improved. The demand […]
Information technology or IT is no more a department that lies in a corner and does not impact day-to-day affairs. When you run an organization then you are involved in almost every sector and usually, they carry risks. IT risk management is a part of managed services for small businesses which are delivered by an […]
There are still organizations that have not been under the cybersecurity radar and are most vulnerable to risks. Digital innovation has increased the network complexity creating new loopholes in the network making it easier for cybercriminals to seep in. Having a Comprehensive Cybersecurity Solution will help organizations to guard their important files and documents. The […]