Best Practices of Cisco NIPS Day 1 Configuration Guide (Part-2)
Hello friends, this is the 2nd part of the Cisco NIPS Day 1 Configuration Guide, if you have not gone through my first part of this blog then you must check that first.
In the end, I will share some OEM-related links as well for you, so you can overcome your all doubts and will get something good out of these blogs.
We are using hardened operating system Cisco Sourcefire NIPS-8350 physical device in this blog as an example:
In the below diagram, you will see 2 Network IPS 8350 for redundancy, ASR routers for WAN connectivity, Firewall, and switches.
Quick Links
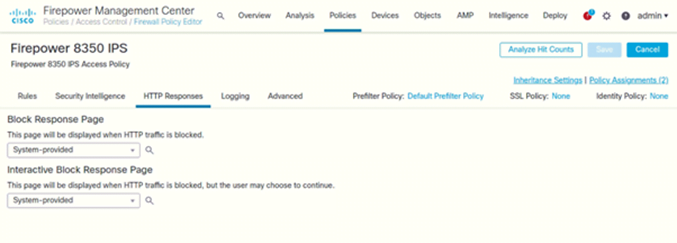
Configure HTTP Responses
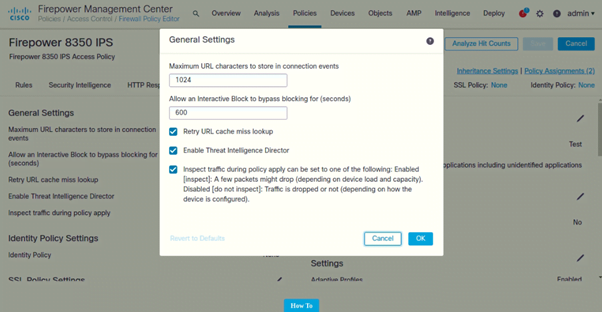
General Settings
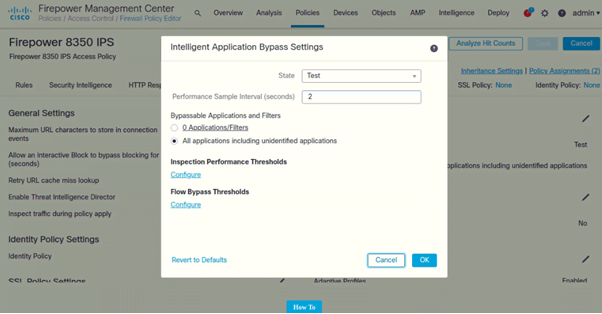
Intelligent Application Bypass Settings
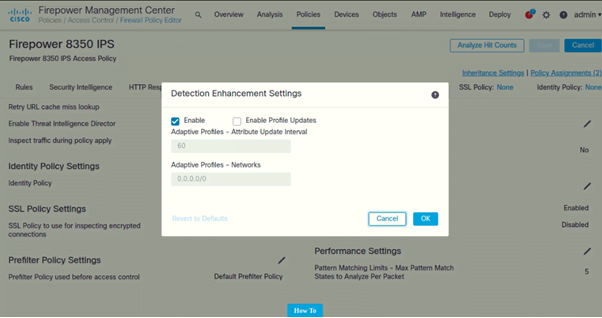
Detection Enhancement Settings
Pre-filter Policy Settings
Balanced Security and Connectivity Policy Settings
Detection Enhancement Settings
Performance
Network Analysis Settings
Latency Based Performance Settings
Configure HTTP Responses – CISCO
When the system blocks web requests, you can set the HTTP response page to display in access control, either using access control rules or by using the default action defined in the access control policy.
- Login to FMC
- Go to Policies > Access Control
- Click on edit on IPS Device
- Click on HTTP Responses
Configure General Settings
- Click on Advanced
- Under General Settings (Click on Pencil icon to edit)
Following are the General Settings configured on both IPSs:
Configure Intelligent Application Bypass Settings
- Click on Advanced
- Under Intelligent Application Bypass Settings (Click on Pencil icon to edit)
Following are the settings configured on both IPSs:
Configure Detection Enhancement Settings
- Click on Advanced
- Under Detection Enhancement Settings (Click on Pencil icon to edit)
Following are the settings configured on both IPSs:
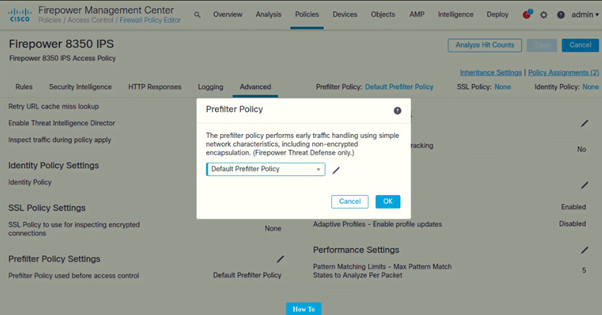
Configure Pre-filter Policy Settings
- Click on Advanced
- Under Pre-filter Policy Settings (Click on Pencil icon to edit)
Following are the settings configured on both IPSs:
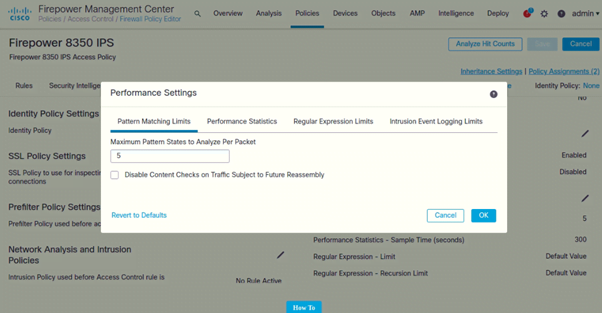
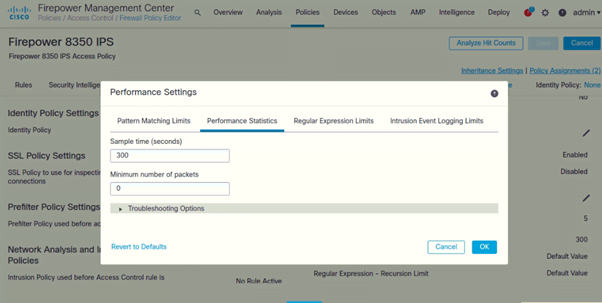
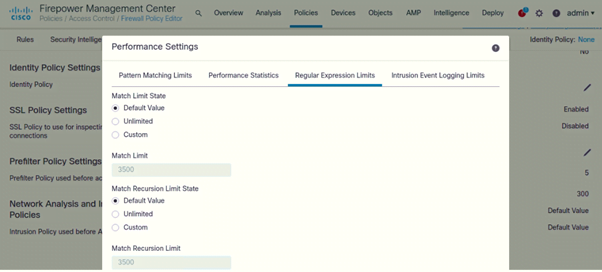
Configure Performance Settings
- Click on Advanced
- Under Performance Settings (Click on Pencil icon to edit)
Following are the settings configured on both IPSs:
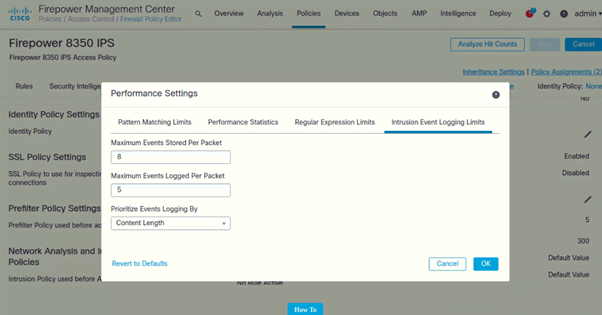
Configure Network Analysis and Intrusion Policies Settings
- Click on Advanced
- Under Network Analysis and Intrusion Policies Settings (Click on Pencil icon to edit)
Following are the settings configured on both IPSs:
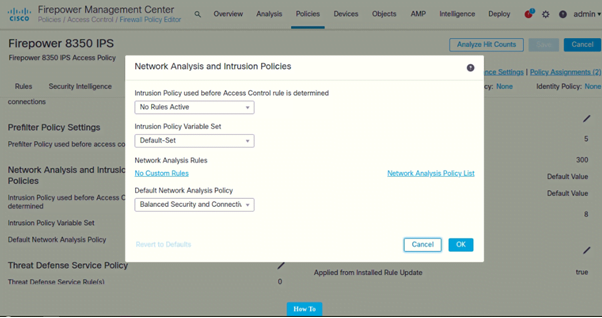
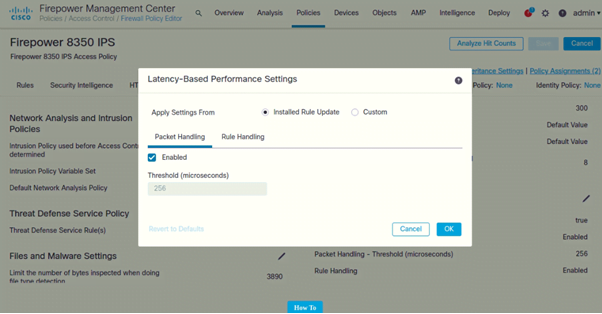
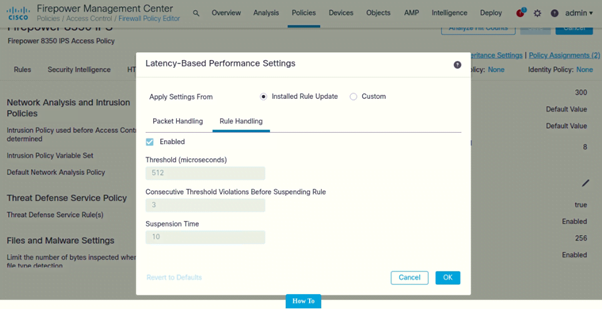
Configure Latency-Based Performance Settings
- Click on Advanced
- Under Latency-Based Performance Settings (Click on Pencil icon to edit)
Following are the settings configured on both IPSs:
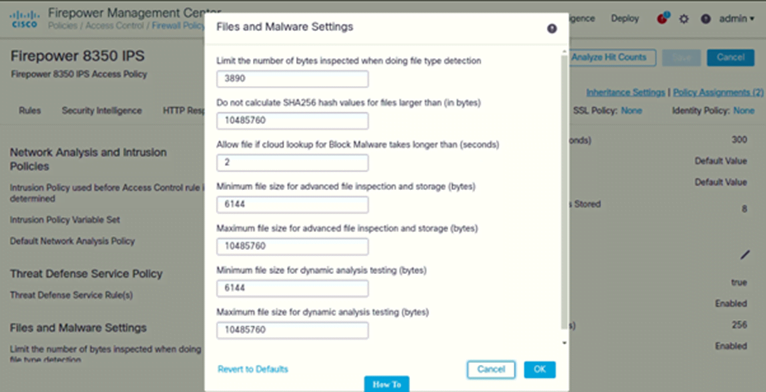
Configure File and Malware Settings
- Click on Advanced
- Under File and Malware Settings (Click on Pencil icon to edit)
Following are the settings configured on both IPSs:
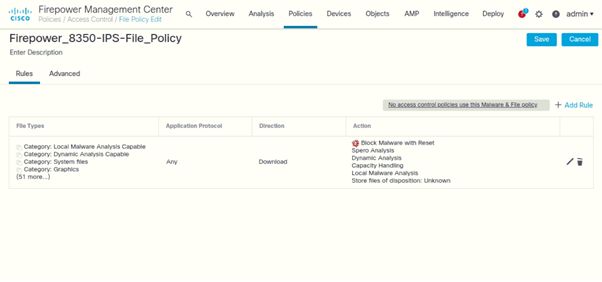
Configure Syslog Settings
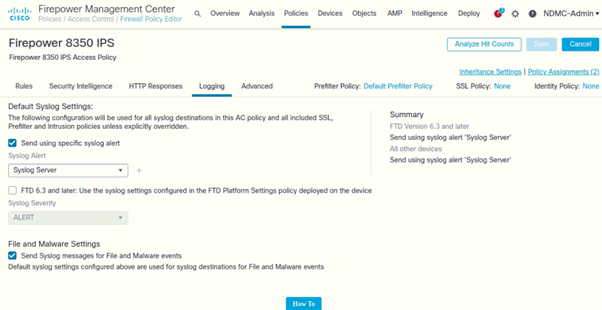
- Login to FMC
- Go to Policies > Access Control
- Click on edit on IPS Device
- Click on Logging
Following are the Syslog Settings configured on both IPSs. Since Logging is enabled per Access Policy, for the Logging details, please refer to the FW_APT_IPS Access Rules.xlsx document.
Configure Balanced Security and Connectivity Policy Settings
- Login to FMC
- Go to Policies > Intrusion
- Click on edit on IPS Device
- In left pane > Expand Policy Layers
- Click on Balanced Security and Connectivity
Following are the settings configured on both IPSs:
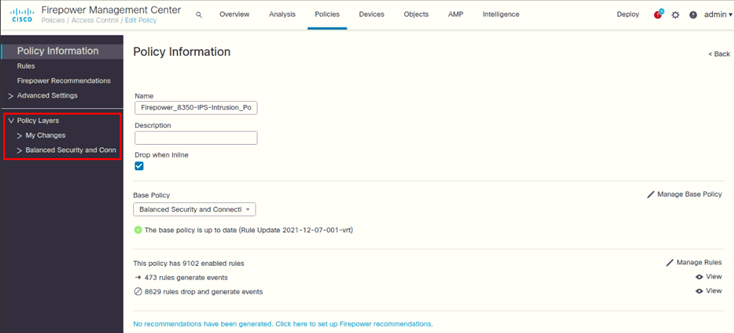
Expand Balanced Security
Click on Rules to configure it
OEM Document Links
Following are the links to the basic troubleshooting guides from the OEM:
Cisco Firepower 8000 Series Getting Started Guide:
Firepower Management Center Configuration Guide:
Initial Configuration Steps of FireSIGHT Systems:
Datasheet and all related documents:
https://www.cisco.com/c/en/us/support/security/firepower-appliance-8350/model.html#Configuration
We have completed the basic config of the Cisco NIPS, but you can do your own research and explore the device as well. I do not recommend copying the exact configuration of this blog because we all know that the configuration is totally dependent on the requirements. You can use the information of blog-1 and 2 for your understanding and then fulfill the requirement of the NIPS configuration.
Keeping your organization safe and data security is the best thing you can do to save your business from getting caught in the net of hackers. Zindagi Technologies is the top IT Consulting company in India that will provide the best security options for your organization. To get in touch with us you can drop us a message on +91 97739 73971 or you can contact us via mail also.
Author
Jagjeet Singh
Senior Network Security Consultant
