How Does GETVPN Secure (Multiprotocol Label Switching) MPLS
When we configure (Multiprotocol Label Switching) MPLS we ensure reachability only. In MPLS, traffic goes in plain text form, so if someone wants to eavesdrop and wants to collect sensitive data or confidential information, they can get that data, and to secure MPLS connectivity we must configure GETVPN (Group Encryption Transport VPN). In general, companies ask the service to provide MPLS service to communicate between different sites. So, in MPLS, the traffic goes in plain text and we must trust the service provider and send the traffic in the plain text although we can also configure GETVPN and secure the traffic. MPLS will provide reachability and GETVPN will provide security by encrypting the traffic.
What is GETVPN?
GETVPN is an IPsec-based VPN and we use GETVPN when MPLS is configured. In the case of GETVPN, the internal IP header and after encryption external IP header will be the same because MPLS private to private reachability is already there.
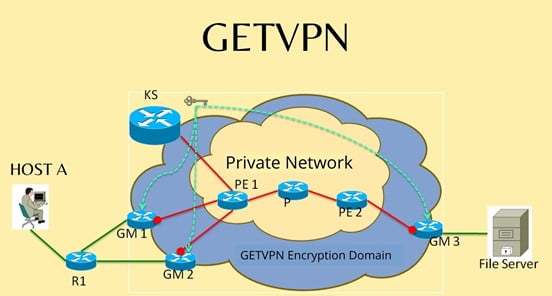
In GETVPN there will be KS and GM, KS will provide keys to GMs and all GM will communicate in the same group securely with the help of those keys.
What are KS and GM in GETVPN?
There will be a Key Server (KS) in all other devices that will be Group Members (GM). All GM will negotiate with KS and get the key according to their group and after that group, a member can communicate directly in the same group. In KS we can create multiple groups and can control the traffic so that only required people can communicate with each other.
Note: GETVPN is a policy-based VPN. We generally create one ACL entry in GMs and its reverse or mirror entry on KS, and it should match otherwise KS will not negotiate with GM. After matching the ACL KS will negotiate with encryption and hashing algorithm. Then KS will generate keys and distribute the keys among all the GMs and all GMs will receive the key and start communicating in the same group. After a certain time, the key will expire and again KS will refresh those keys (this process is call rekeying).
What is GDOI?
GETVPN uses GDOI (Group Domain of Interpretation) to exchange all traffic between KS and GMs. GDOI uses UDP port number 848. It is similar to ISAKMP in function. In the exchange process between KS and GMs, there will be 10 packets and all packets use port number 848 for both source and destination both.
GDOI packet exchange: In exchange, there will be 10 packets to negotiate and get the keys for actual data packet communication.
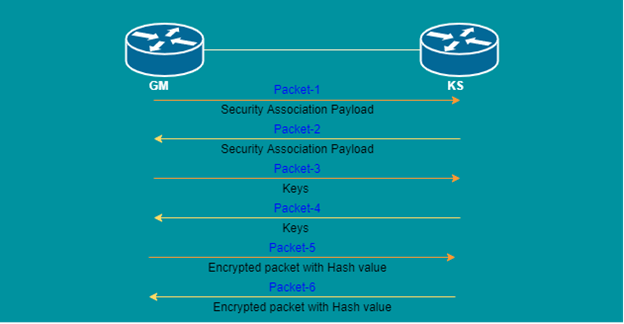
- GM will initiate the 1st packet and share the security association payload. In which there will be single or multiple sets of policies. This packet contains hashing algorithm (MDF5, SHA256, etc.), authentication method (RSA-sig, PKI), Diffie Helman group number, Lifetime Encryption Algorithm (AES, 3DES, etc.).
- Now 1st packet will be received by KS and KS will compare those sets of policies and then if it finds a matching set of policies, it will send the 2nd packet to GM with only the matched set of policies. Then both will negotiate with that set of policies and generate keys.
- Now GM will send keys in the 3rd packet.
- KS will share keys in the 4th packet.
- Now as both of them have keys, so GM will send the 5th packet in encrypted form with hash, and KS will decrypt the packet with the help of the key and check the integrity with the help of hash value.
- Then KS will send the 6th packet in encrypted form with hash and GM will decrypt the packet with the help of a key and check the integrity with a hash value.
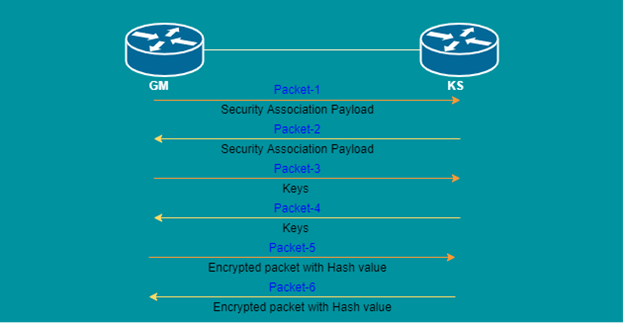
- GM will initiate with the 7th packet with identity number
- Then KS will share the 8th packet with two types of keys (to communicate with other GM in the same group and communicate with KS), algorithms, SPI, ACLs, etc.
- After that GM will check the algorithms and send the 9th packet as an acknowledgment.
- Then KS will send the 10th packet as an acknowledgment.
The complete process is called the Registration Process. KS will offer two types of keys, one is TEK (Traffic encryption Key) and the other is KEK (Key Encryption Key). TEK is used to secure GETVPN data plain traffic, when GM will communicate with GM then it will be used. KEK is used when GM will communicate with KS and vice versa. We hope this blog is useful to you in the terms of either learning or performing.
Zindagi Technologies are the most efficient in implementing, handling, and giving the right services to those who require them. We provide several services including Enterprise Networks, Cloud and Virtualization, Data Center Networks, Content Security, network security, and many more. If you are planning any of the above-mentioned services or any other, then you can contact us anytime or call us on +919773973971 as our experienced solutions architects will be giving you the right solution for your problem.
Author
Dipayan Sarkar
Network Security Consultant
