Cisco FTD Management Options, Use Cases, & Best Practices
Our goal as a Network Security Engineer is to be able to provide security of communication and restrict access from insecure networks. E.g. Internet. We use Firewall very commonly to restrict unwanted communication between various private networks and public networks. Cisco offers an NGFW Solution called Cisco Firepower Threat Defense. In this blog, we will discuss the management options of Cisco FTD, Use Cases, and Best practices.
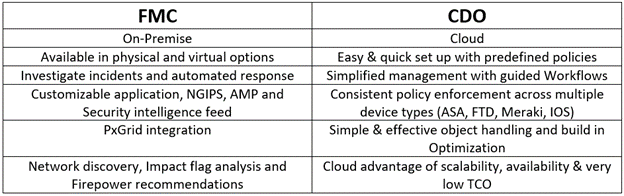
Management Options for Cisco FTD
Firepower Device Manager
- Manages a single Firepower Threat Defense
- Default device manager
- Included in all Firepower Threat Defense software
- Can co-exist with cloud based management platform, Cisco Defense Orchestrator (CDO)
Firepower Management Center (FMC)
- Helps Administrators to enforce consistent access policies in all FTDs
- Rapidly troubleshooting security events
- Generate summarized report across the deployment
- Centralized on premise management across multiple Firepower platforms
- Reduces complexity of manual policy configuration through inheritance and template use
Cisco Defense Orchestrator
- Consistently manage policies across your Cisco security products. CDO is a cloud-based application that cuts through complexity to save time and keep your organization protected against the latest threats
- Supports ASA, FTD, WSA, Meraki, IOS, AWS
- Faster device deployments
- Cross platform object and policy management
Choosing an Appropriate Firewall Manager
Common Use Cases for NGFW
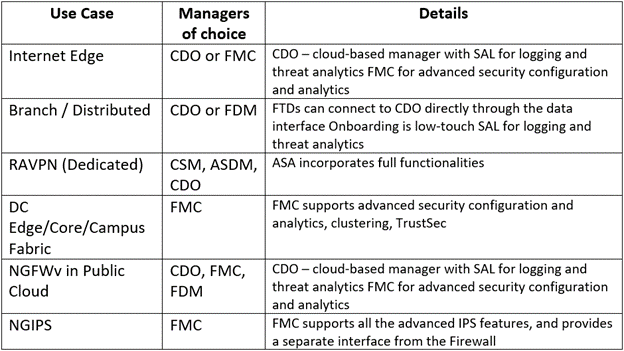
- NGIPS
- Internet Edge
- Branch
- RA VPN
- Data Center
- Cloud/Virtual
Best Practices for Logging
- Enable connection logging on a per access-control-rule basis
- Don’t enable logging for access rules with trust action
- Don’t enable logging for rules with block action in passive mode
- Log either at the beginning or end of the connection (not both)
- Log events to an external location
Best Practices for Enterprise Branch
- Leverage Site-Site VPN to create a backup for WAN or MPLS failure
- For S2S VPN use IKEv2 – better performance, conserved bandwidth
- Prevent overlapping networks across the branches
- Think about sysopt permit-vpn
- Apply strong encryption (license dependent)
Best Practices for RAVPN
- Build a resilient solution to provide seamless access
- Preferred deployment mode is Routed
- Use multiple connection profiles based on the authentication type
- Leverage Group policies for user-specific attributes
- Use NextGen security controls and create specific access rules
- Make use of split tunnel with other security controls like Umbrella
Best Practices for NGIPS
- Build a resilient solution leveraging fail-open, fail-close capabilities
- Leverage Inline mode for critical network segments
- Leverage Passive mode for non-critical network segments
- Be specific in configuring Variable Set and Network Discovery Policy
- Leverage Firepower Recommendations and Impact Flag Analysis
- Do selective TLS Decrypt & forward Logs to SIEM for long term storage
Best Practices for Internet Edge
- Build Device, Link & Interface Level Redundancy
- Preferred deployment mode should be Routed
- Modify the default policies with your network specific values
- Use RBAC for clear segregation of duties and access
- Use rule grouping for separation of Trusted & Untrusted rules
- Do selective TLS Decrypt & disable logging when not needed
Best Practices for Data Center
- Build Device, Link & Interface Level Redundancy
- Prefer Routed mode for Edge and Transparent for Core
- Use Segmentation: TrustSec, ACI & Multi Instance
- Be aware of clustering positioning, sizing, and supported features
- Implement selective logging and use APIs for automation
- Use Hardware Flow Offload & do selective TLS decrypt
Best Practices for Cloud & Virtual
- Build a scalable design with Native/3rd Party LLB
- Connect your virtual appliances to FMC either on cloud or local on-prem
- Leverage various available tools to identify cloud APP’s and put controls
- Use RBAC for access separation and granular policies to avoid policy risk
- Leverage logs and uses Firepower Recommendations
Recommended Manager and OS per Use Case
Are you planning to deploy Cisco FTD Firewall for your environment?
Do you want a Green-field Deployment, Tech Refresh, Migration from your legacy Firewall or any Firewall to Cisco FTD or for implementing advanced features in your already deployed FTD Firewall for your personal or private network or your organization? You can always reach out to us, the team at Zindagi Technologies consists of experts in the field of Network Security, Data Centre technologies, Enterprise & Service Provider Networks, Virtualization, Private Cloud, Public Cloud, Data Center Networks (LAN and SAN), Collaboration, Wireless, Surveillance, Openstack, ACI, storage and security technologies with over a 20 years of combined industry experience in planning, designing, implementing and optimizing complex Network Security and VPN deployments. You can drop us an email or you can give us a call at +91-9773973971
Author
Harpreet Singh Batra
Consulting Engineer- Data Center and Network Security

Cisco Firepower 4100 Chassis Configuration | Zindagi Technologies
December 26, 2022[…] (NGFW) is the first threat-focused NGFW in the industry. We can create logical devices like FTD, and ASA on Cisco Firepower. From the network to the endpoint, it provides full, unified policy […]
Upgrade FXOS | FCM | Zindagi Technologies
April 17, 2023[…] for the ASA (Adaptive Security Appliance) on the supervisor. We can create logical devices like FTD, ASA on Cisco […]