Deep Dive into Ethernet Header.
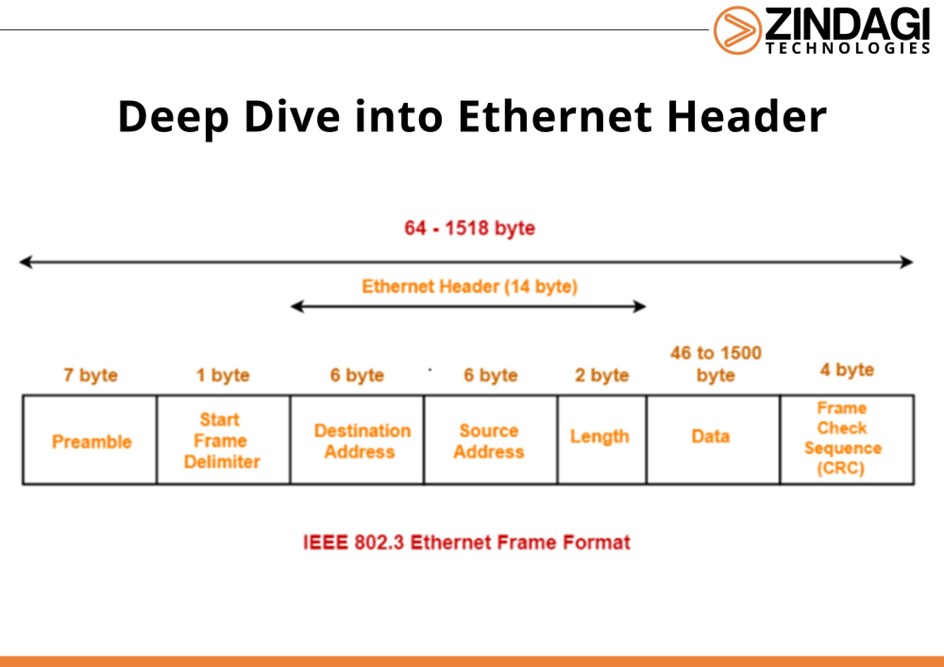
Ethernet is a part of wired computer networking technologies that are mostly used in LAN, MAN and WAN. It was industrially introduced in 1980 and firstly standardized in 1983 as IEEE 802.3.
Ethernet DIX Header
- This Header is owned by DIX (Digital, Intel and Xerox) (Ethernet DIX)
- This header is used at layer 2 for data encapsulation.
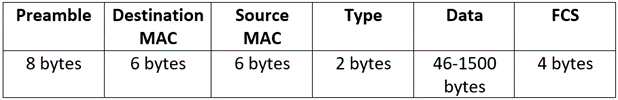
Preamble
This field is used to define a new frame that is received by the device and in which the first 7 bytes are in 10101010, 10101010, 10101010, 10101010, 10101010, 10101010, 10101010, and the last byte is 10101011, when the device sees the last two bits 11 the device will be able to recognize that the actual data starts.
Destination MAC
It is 48 bits destination host physical address/MAC address.
Source MAC
It is also 48 bits source host physical/MAC address.
Type
- This is used to define which data/protocol (not user data) is encapsulated in this layer 2 header
- Example- 0x800 – IPV4 header
- 0x806 – Arp header
- 0x86dd – IPV6 header
Data
This represents which kind of data is encapsulated in this header (IP, IPV6, ARP)
FCS
- Frame Check Sequence
- This field is used to check data integrity using CRC
- CRC- Cyclic Redundancy Check – It calculates over data and header and that value known as check sum, is put in the FCS field.
Note- This header (type field) is failed to tell layer 2 Protocols like CDP, STP, and VTP. That’s why this Header is not enough. So, IEEE come and modify this header and divide this header into 2 parts
- 802.3 MAC
- 802.2 LLC
802.3 MAC + 802.2 LLC
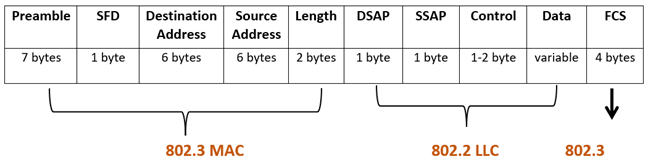
Preamble
This field is still the same but only has 7 bytes
SFD
- Signal Frame Delimeter.
- After that actual frame will start 10101011.
Destination MAC
Source MAC
Length
This field is used here to define the length of the ethernet header
DSAP
- Destination Service Access Point
- These field bits are reserved for something
- It defines the size of only some protocols
SSAP
- Source Service Access Point
- This defines which protocol is encapsulated in the upper layer
Control
Connection types, Connectionless on modern devices
Data
Data types in the upper layer
FCS
- Frame Check Sequence
- This field is used to check data integrity using CRC
- CRC- Cyclic Redundancy Check – It calculates over data and header and that value known as check sum, is put in the FCS field.
Zindagi Technology is an IT Consulting services Company in Delhi. Zindagi Technologies consultants have expertise in the field of designing, building, and maintaining large-scale Networks, Data Centers, Cyber security aspects and large IT infrastructure. We have profitable years of experience with public and private sector clients and have been giving very positive and profitable work in all aspects. If you think your company goals are lacking and need to be completed with the right resource then drop us a message at +91-9773973971, or get in touch with us via email. Follow us on LinkedIn and stay in touch with the latest technology blogs.
Author
Abhishek Kaushik
Associate Consultant
