TACACS+ Vs. RADIUS. Which is better?

Earlier, we discussed the AAA framework and products available to provide AAA service. We know that protocols are essential to achieve communication between devices. So, today we are going to shed light on the protocols used between the device and the AAA server and how exactly they work. Several protocols can be used by the AAA server, but the two most used protocols are RADIUS and TACACS+
RADIUS stands for “Remote Authentication Dial-In User Service” and TACACS stands for “Terminal Access Controller Access-Control System.”
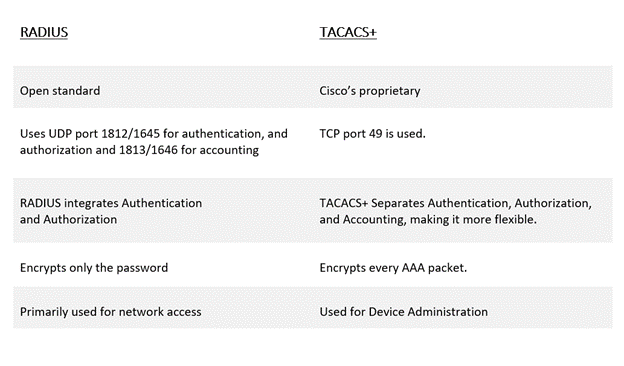
RADIUS
RADIUS is a client-server networking protocol that provides centralized authentication, authorization, and accounting for users wanting to gain access to the network. To authenticate an endpoint, RADIUS uses a client, NAS (Network Access Server), and a server.
The first step is that the user sends a request to the NAS (Network Access Server), which takes the responsibility for forwarding the users’ requests to the RADIUS (AAA) server and vice versa. A program called Supplicant carries the user’s credentials to the NAS.
The NAS sends an ACCESS-REQUEST message to the RADIUS server containing the user data. The server compares it against the information held in its database and responds with either:
ACCESS-CHALLENGE: requesting more information (typically a secondary password, PIN, or token) before authenticating the user.
ACCESS-ACCEPT: In case the user credentials are legit and found in the database, allowing the user to access the network resources with configured authorization policies.
ACCESS-REJECT: In case the user credentials are not found in the database, reject the user’s request to enter the network.
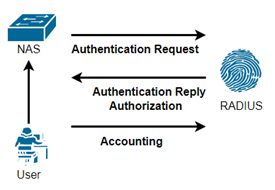
TACACS+
TACACS+ is a security protocol that provides centralized authentication of users who are attempting to gain access to NAS or NAD (network access server or network access device). TACACS+ provides separate authentication, authorization, and accounting services. TACACS+ VSAs (Vendor-Specific Attributes) can be used to manage administrator authorization.
These VSAs enable quickly changing the roles, access domains, and user groups of administrators directly through the directory. It allows the network administrator to define what commands a user can run. One of the critical functionalities of TACACS+ is its ability to separate authentication, authorization, and accounting into separate and independent functions. Therefore, TACACS+ is so commonly used for device administration.
Key Differences between RADIUS and TACACS+
Which is better?
Both RADIUS and TACACS+ are AAA solutions that enforce network security. RADIUS and TACACS+, in general, perform similar functions depending on the type of network devices. Equally, both protocols can handle AAA duties. Usually, they are both used for distinct purposes:
Device Administration and Network Access policies are quite different. With Device Admin, policies are created that dictate privilege levels, and command sets (which command this user is permitted to run on the device). Network access, VLANs, Security Group Tags, Access-Control-lists, etc. are assigned to the connected users. The network access policy cares about attributes of the endpoint, such as its profile and posture assessments.
RADIUS does not allow users to control which commands can be executed on a device and which cannot. Because it combines Authentication and Authorization, RADIUS is not as useful for device management. TCACAS+, on the other hand, allows for command authorization control on a user or group basis because it separates authorization from accounting.
We Conclude
Choosing between the two depends on the use case and vendor interoperability. If the primary requirement is device administration and you are tied to Cisco Solution, TACACS+ is good to go. If there is vendor interoperability and the priority is network access management, RADIUS might be a better option. TACACS+ and RADIUS can also be deployed together to provide both services in parallel.
Now we know the protocols used for the AAA security solution, their use cases, and the considerations to keep in mind while choosing which one to pick for what purpose.
Zindagi Technologies is a leading IT consulting and cybersecurity company which is serving as a commercial enterprise across the globe. We bring multiple solutions for your IT infrastructure problems and solutions that will complete your business goals. We have been working with the public and private sectors and have been delivering positive results too. You can give us a call or message at 9773973971 or you can contact us via email and we will surely get back to you.
Curious to learn more? Check out Zindagi Insights. Follow us on LinkedIn to get updates about new blogs and some quiz sessions to challenge your learning.
Author
Divyank Taneja
Associate Consultant

deep hazra
August 15, 2023Thank You Message For Sharing The Information
https://advanceslinux.com/restore-database/