Understanding Authentication, Authorization, Accounting (AAA), and its need.

Network security is an essential part of an IT infrastructure. So is remote access administration. It is usually enforced in the form of a centralized access mechanism. Such a framework takes care of three key components of network access – Authentication, Authorization, and Accounting, or AAA.
AAA is a security framework that controls user access to network resources, imposes policies, and audits their usage. AAA plays a significant role in managing and securing the network by inspecting the users and keeping track of their activities while they are connected.
- Authentication – The first step in a secure identification system is to make sure that the user accessing a system is credible. Authentication decides a user’s credibility based on the identity presented by comparing it to that of known users.
- Authorization – After authentication, Authorization determines what that specific user is allowed to do and access within the network. Users are categorized to know what type of privilege they have such as an Administrator or a Guest.
- Accounting – Accounting involves monitoring and keeping track of the session statistics and audits usage information that is being used after the user has been authenticated and authorized.
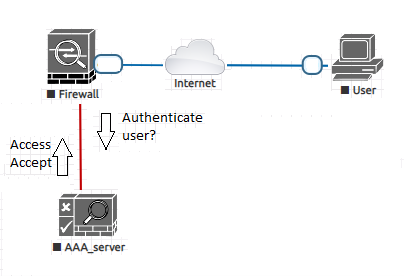
Why is AAA Important?
AAA is crucial because it limits the user’s access to a system and keeps track of their activity. AAA security enables us to dynamically configure the type of authentication and authorization wanted by creating policies for specific services and users. AAA ensures an increase in flexibility and control over access configuration.
There are two main roles that AAA plays in a network:
Network Access Control
Network access involves controlling- granting, or limiting access based on the credentials provided by a user. AAA verifies the identity of the user or a device by comparing the presented credentials against a database of known users. If the information matches, Access to the resources is granted based on their privilege.
The protocol used for network access control is RADIUS (Remote Authentication Dial-In User Service)
Device Administration
Device Administration involves implementing policies to determine who can log in to a device’s console or remote session to manage it, the level of privilege they have, and operations they can run by keeping track of their actions. The protocol used for Device administration is TACACS+ (Terminal access controller Access-Control System)
Solutions Available for AAA Security
Cisco ACS
The Cisco Access Control System (ACS) is an AAA (Authentication, Authorization, Accounting) solution that provides policy-based security and enables the management of all network devices to access centrally. ACS acts as an integration point for network access control and identity management. ACS has an easy-to-use GUI and provides a redundant and scalable solution.
Cisco ACS comes in three flavors:
- Hardware Appliance – A physical device comes with ACS software preinstalled.
- Software – A software package that can be installed on a windows server.
- Virtual machine installation
Cisco ISE
Cisco Identity Service Engine (ISE) is recognized as one of the leading integrated and open platforms that provide in-depth visibility of all the users, devices and applications that are on the network.
Cisco ISE (Identity Service Engine) is said to be a next-generation network access control solution that enables a dynamic and automated approach to enforce policies.
Some of the key features of Cisco ISE – Deeper visibility, Secure access control and Asset enforcement, Device administration for managing the network devices, BYOD (Bring your own device), and Guest and visitor management.
Cisco ISE is available in two flavors:
- Hardware Appliance – Cisco SNS 3500 and 3600 series
- Virtual machine – Cisco ISE 1. x to 3. x
This article explains the fundamentals of the AAA framework, the importance it holds and Cisco’s solution to achieve access control for your network. Check out more about Cisco ISE and stay tuned for our upcoming blogs with much more to highlight.
We, here at Zindagi Technologies Pvt. Ltd., understand our customers’ needs and challenges to help achieve the best possible outcome. We are a top-managed IT service provider with the ability in Security solutions and our services have positively affected many organizations. Get in touch with us at +91 9773973971 and do follow us on LinkedIn.
Author
Divyank Taneja
Associate Consultant-Network Security

TACACS+ Vs. RADIUS, which is better | Zindagi Technologies
December 13, 2022[…] we discussed the AAA framework and products available to provide AAA service. We know that protocols are essential to achieve communication […]