Don’t Overlook Layer 2 Security – Consequential for Network (Part-3)

This is the 3rd and last part of Layer 2 Security. We have already discussed MAC Attacks, VLAN Hopping attacks in Part 1 and DHCP Attacks, and GARP Attacks in Part 2.
If you really need to secure your Layer-2 of the network, then please follow all the parts, and apply Layer-2 Security in your organization/Data Center.
In this blog, we will cover Spoofing Attacks. It has 2 categories that are as follows:
- MAC Spoofing Attack – A network attacker can gain access to a network using MAC addresses. Additionally, it can be used to take over someone’s existing identity on the network.
- IP Spoofing Attack – In IP spoofing, IP packets are created with a modified source address to either disguise the sender’s identity or to impersonate another computer. It is a technique used by attackers to attack targets or infrastructure in the surrounding area with DoS/DDoS attacks.
Countermeasures to Spoofing Attacks – IP Source Guard
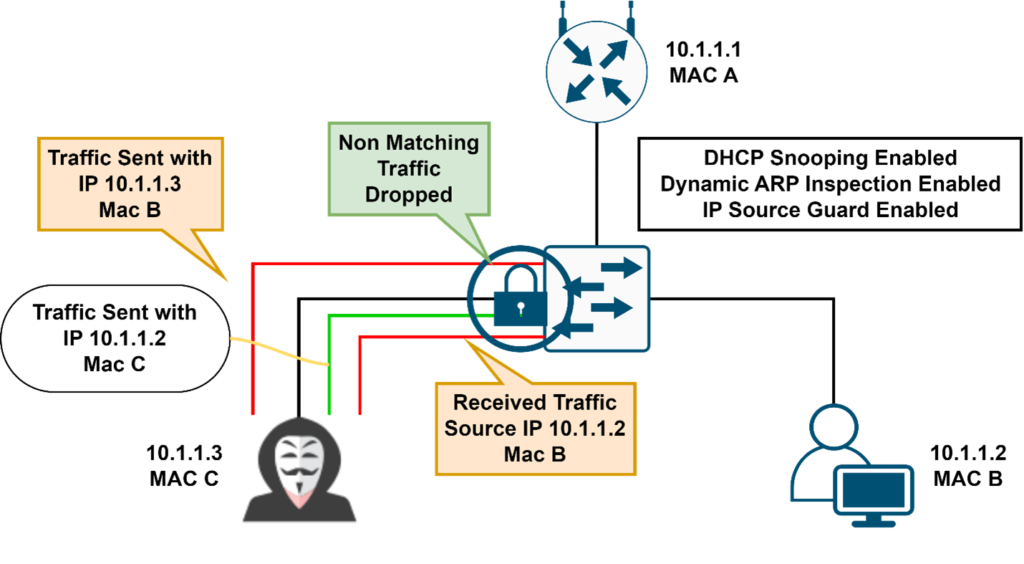
- It uses the DHCP snooping binding table information
- IP source guard Operates just like dynamic ARP inspection but looks at every packet, not just the ARP packet. It checks the MAC address and IP address from the interface in the binding table, if it does not match then it blocks the traffic.
IP Source Guard
IP Source Guard is a per-interface traffic filter that permits IP traffic only when the IP address and MAC address of each packet matches one of two sources of IP and MAC address bindings:
- Entries in the Dynamic Host Configuration Protocol (DHCP) snooping binding table
- Static IP source entries that you configure
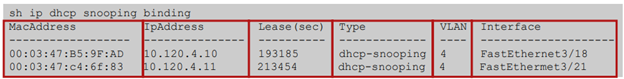
The device drops IP packets when the IP address and MAC address of the packet do not have a binding table entry or a static IP source entry. For example, assume that the show ip dhcp snooping binding command displays the following binding table entry:

If the device receives an IP packet with an IP address of 10.5.5.2, IP Source Guard forwards the packet only if the MAC address of the packet is 00:02:B3:3F:3B:99
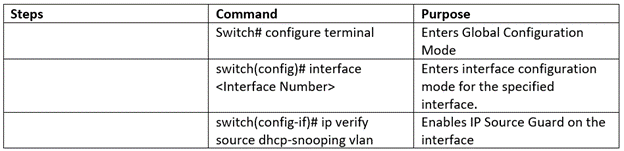
Configuration of IP Source Guard
Note* – DHCP and DHCP Snooping is the prerequisite for the IPSG (IP Source Guard). First, you must configure both the features (DHCP and DHCP Snooping) to use the IPSG feature. No additional license is required for this feature.
Enable IP Source Guard on a Layer 2 Interface
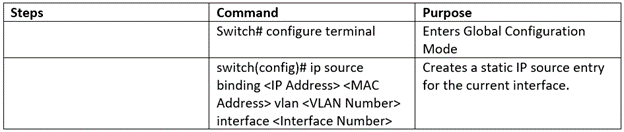
Add Static IP Source Entry
Summarize
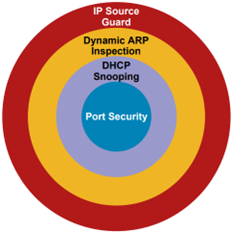
- Port Security prevents from CAM attacks and DHCP Starvation attacks
- DHCP Snooping prevents from Rogue DHCP Server attacks
- Dynamic ARP Inspection prevents current ARP attacks.
- IP source guard prevents IP/MAC spoofing
We have successfully completed the major parts of Layer-2 Security. I hope all the queries are resolved now. You can also check out our other security blogs. We hope all the queries related to these attacks are resolved. Stay Tuned for more such blogs. Let’s get in touch and transform your IT needs accordingly, you can contact us or you can call us on +91 9773973971 and we will get back to you soon.
Author
Jagjeet Singh
Senior Consultant-Network Security
