Don’t Overlook Layer 2 Security – Consequential for Network (Part-2)

This is the second part of Layer 2 Security. We already posted Part 1, if you have not checked that then please check it out first as skipping the first part may lead you to leave the vulnerability in your network. We have already covered MAC attacks and VLAN Hopping attacks. The remaining Layer-2 attacks are:
- DHCP Attack
- GARP Attack
- Spoofing Attack
- MAC Spoofing
- IP Spoofing
In this blog, we will cover DHCP and GARP attacks and will see, how to mitigate them. We will continue Spoofing Attack in Part 3.
DHCP (Dynamic Host Configuration Protocol) Attack
DHCP Overview:
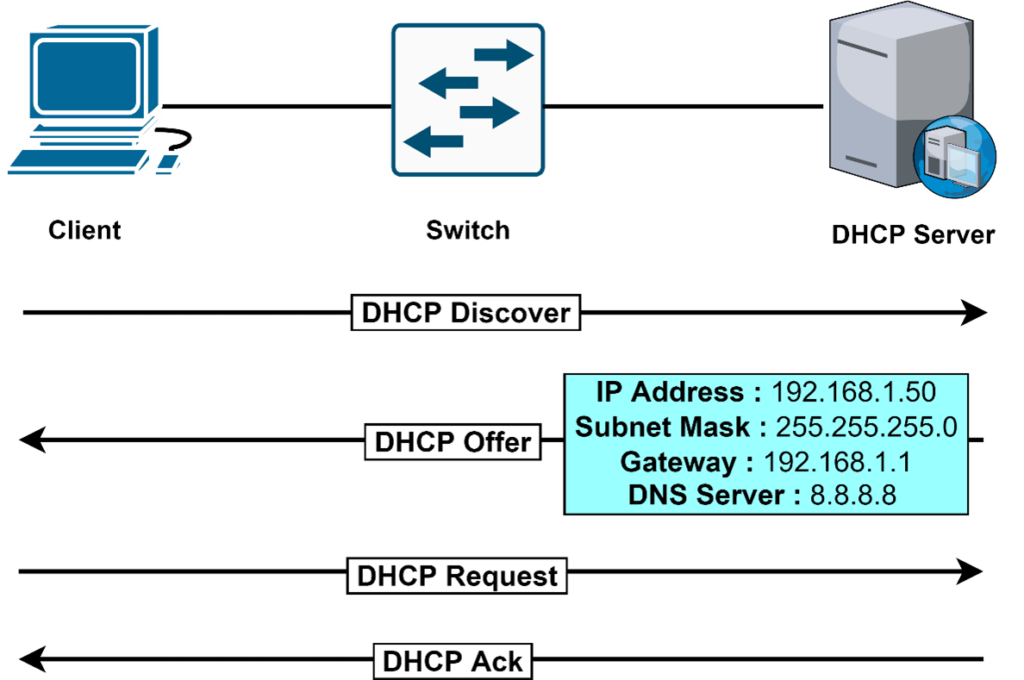
DHCP defined by RFC 2131
DHCP Attack Types:
- DHCP Starvation Attack
- Rogue DHCP Server Attack
DHCP Starvation Attack
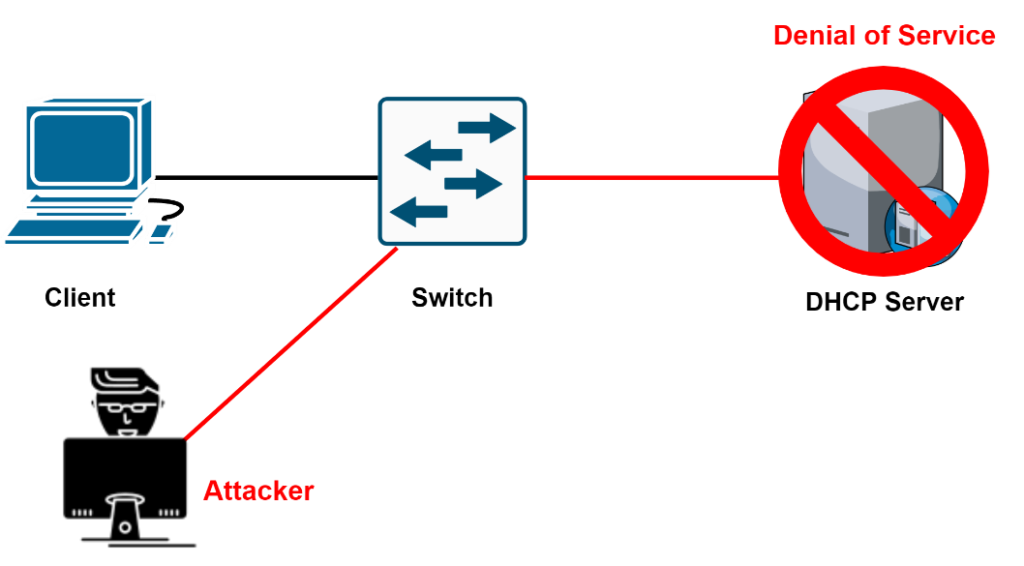
- The Attacker looks at the entire DHCP scope and tries to lease all the DHCP addresses available in the DHCP scope
- This is a Denial-of-Service DoS attack using DHCP leases
Countermeasures for DHCP Starvation Attack
- The Attacker uses a new MAC address to request a new DHCP lease
- Restrict the number of MAC addresses on a port with port security
- Else use option 82 of the DHCP
- A DHCP server can track which port has already got one IP address
Rogue DHCP Server Attack
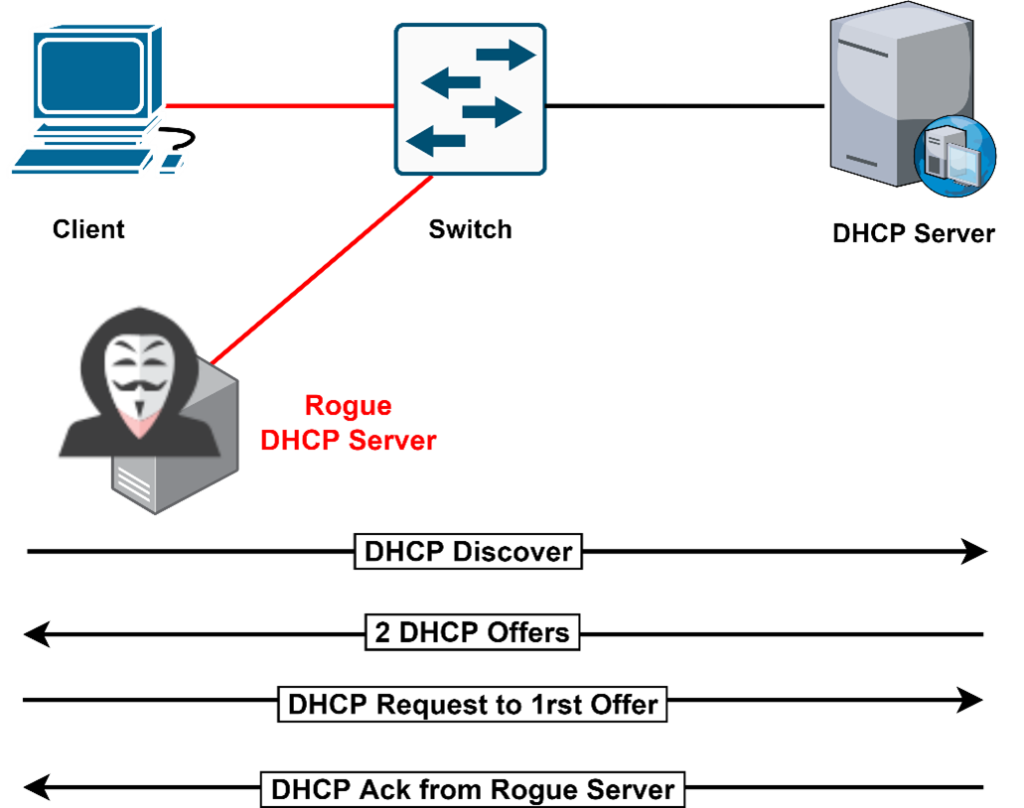
In the above diagram, the Attacker introduces himself as a DHCP server in the network. The Attacker Offers the Network IP configuration details to the Clients in the respect of DHCP Discover Messages.
In this scenario, the problems are:
- Wrong Default Gateway – Attacker is the Gateway
- Wrong DNS Server – Attacker is the DNS Server
- Wrong IP Address – Attacker does DOS with incorrect IP
Countermeasures for Rogue DHCP Server Attack
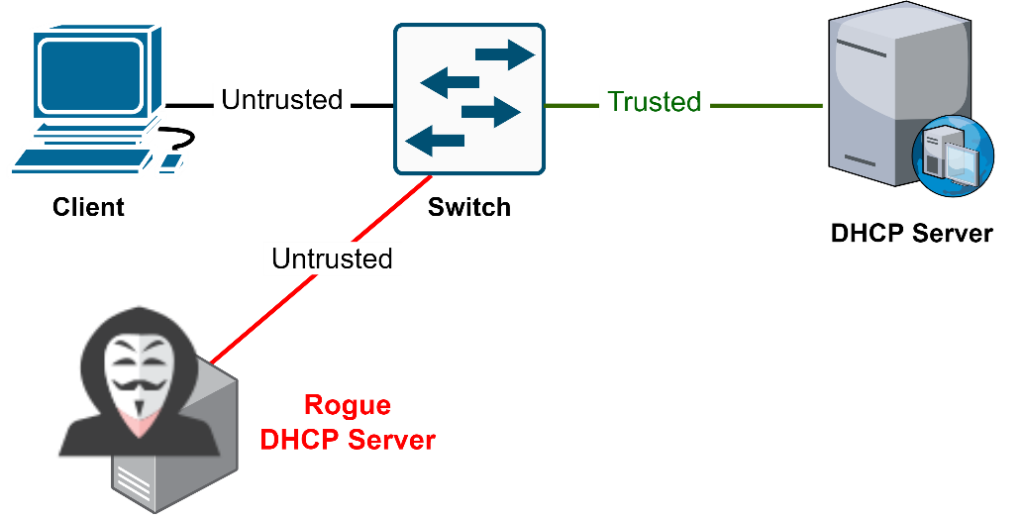
In the above diagram, there is a Trusted port to which the DHCP server is connected. The switch accepts DHCP responses on that port only. By default, all the Ports in the VLAN are Untrusted.
To Enable the DHCP snooping –
- Global command to enable the feature – “ip dhcp snooping”
- Interface command for Trusted Server – “ip dhcp snooping trust”
To Disable the DHCP snooping –
- Global command to disable the feature – “no ip dhcp snooping”
- Interface command to Untrust the Server – “ no ip dhcp snooping trust”
GARP Attack
ARP Function
Before Communication between 2 Clients, an ARP request is necessary to map the IP address to the MAC address.
All the computers on the subnet will receive and process the ARP request, If the client matches the IP address in the request, then it will send an ARP reply.
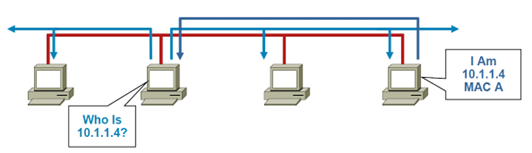
Gratuitous ARP (GARP)
A client is allowed to send an unsolicited ARP; this is called Gratuitous ARP (GARP). Other clients on the same subnet when receiving the GARP message, they store this information in their ARP tables.
Any Client can claim to be the owner of any IP/MAC address they like.
ARP attacks use this to redirect traffic.
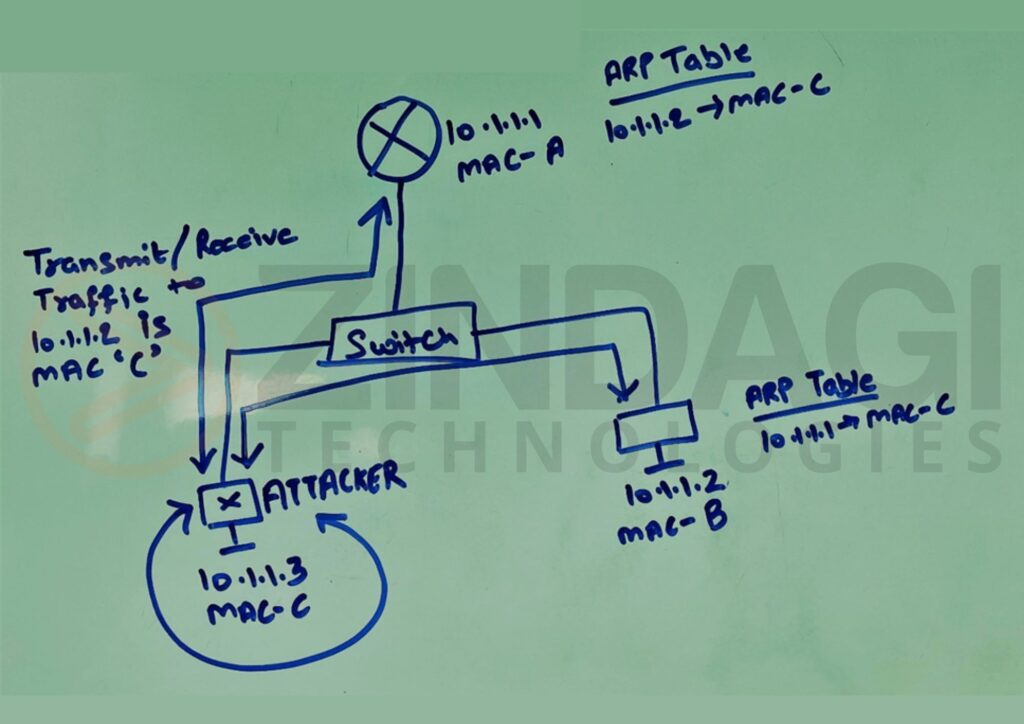
As you can see above the diagram, the Attacker has poisoned the ARP tables of the Router and the Client. Now, all the traffic flows through the Attacker.
Countermeasures to ARP Attacks
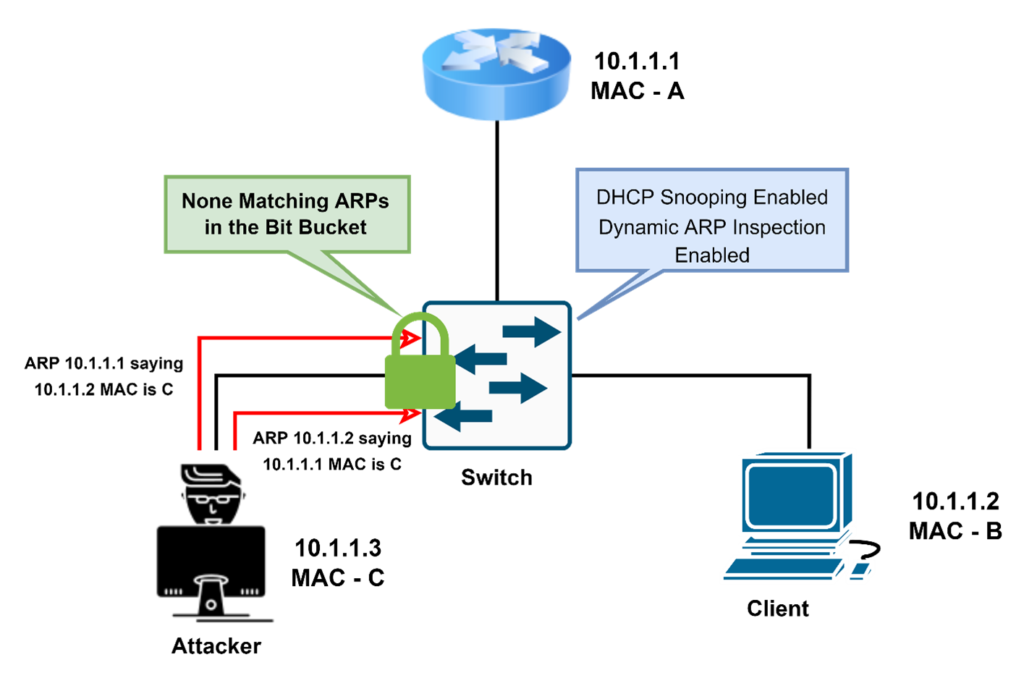
In the above diagram, Network Administrator uses DHCP Snooping with Dynamic ARP Inspection. Now, Switch matches all the ARP packets with IP/MAC binding table entries. If the entries do not match, then it will drop the packets.
To Summarize:
- Port Security prevents CAM attacks and DHCP Starvation attacks
- DHCP Snooping prevents Rogue DHCP Server attacks
- Dynamic ARP Inspection prevents current ARP attacks.
As you can see, Layer-2 security is a very crucial part of the network, and we should use these features to prevent such attacks. We will continue Spoofing Attacks in Part 3. You can also check out our other security blogs. We hope all the queries related to these attacks are resolved. Stay Tuned, Contact US or you can call us on +91 9773973971.
Author
Jagjeet Singh
Senior Network Security Consultant

Don’t Overlook Layer 2 Security Pt 3 | Zindagi Technologies
November 9, 2022[…] This is the 3rd and last part of Layer 2 Security. We have already discussed MAC Attacks, VLAN Hopping attacks in Part 1 and DHCP Attacks, and GARP Attacks in Part 2. […]