What is CISCO ISE and its PERSONAS?
WHAT IS CISCO ISE?
The Cisco Identity Services Engine (ISE) or CISCO ISE is a security policy management platform that is a critical component of Cisco’s zero trust architecture. Its job in the network is to allow the network to act as a network security enforcement point.
Cisco ISE assists in the paradigm shift of network security enforcement being enforced by the network rather than a single device. This is accomplished through the Remote Authentication Dial-in User Service (RADIUS), which handles the network’s authentication, authorization, and accounting (AAA).
Cisco ISE serves as a centralized network security policy platform and RADIUS server, allowing all network devices to use the AAA function. The network access device (NAD) transmits all essential authentication parameters to Cisco ISE whenever a user or an endpoint attempts to access the network. Using RADIUS attribute/value pairs, Cisco ISE responds to the NAD with the resulting security policy to be implemented to the user/endpoint (AV pairs).
Cisco ISE’s precise policy building blocks ensure that you may adopt the optimum network security policy for each user or group on a per-user or per-group basis.
A network administrator can provide differentiated network access to all users by tightly connecting the user’s authorization with the authentication.
- If you are a basic user, your network access will most likely differ from that of a network administrator.
- If you connect to the network using a wireless connection, your level of access may be different than if you connect via a wired connection.
- If you are accessing the network from a remote branch site, it can be different from if you are accessing it from the campus network.
Cisco ISE further has several more advanced features
Profiling: –Endpoints can be dynamically identified using this feature, which is natively incorporated in Cisco ISE. When an endpoint tries to connect to the network, ISE may profile it, recognizing, tracking, and taking inventory of the endpoints that are trying to connect to the network depending on a predetermined security policy.
Posturing: –Posturing is more in-depth than profiling and takes a different technique. Profiling relies on network-level communications to determine information about the endpoint, whereas posturing makes use of data stored on the endpoint. Posturing ensures that the endpoint is following security policies that have been deployed to the endpoint, such as antivirus software, antispyware software, and other security policies, by using a network access control (NAC) agent that resides on the endpoint directly.
Guest-level access: – A trusted employee can create temporary guest credentials for guests, contractors, or other temporary users using the guest portals offered in ISE. These visitor credentials are then given to the guest user to log in to the network, either manually or via email.
Because Cisco ISE provides highly differentiated access to corporate, employee, and guest endpoints while enforcing profiling, posturing, and MDM-influenced authorization policies, network managers must be able to keep track of the level of access allowed to users/endpoints.
This is also a built-in function of Cisco ISE.
Cisco ISE provides a logging event for each authentication, authorization, profiling, or posturing activity. Network administrators can filter, send to syslog servers, and otherwise search these logging events to learn more about a user’s network authentication and authorization.
A network administrator can spread a single security policy to the far reaches of the network and ensure that the security policy deployed to each user/endpoint is as secure as feasible by combining the industry-trusted RADIUS protocol with the granular, context-based policy offered with ISE.
PERSONAS
Given the variety of functions that Cisco ISE may play in an enterprise setting, a distributed architecture is required to fulfill those roles at scale; these responsibilities are referred to as personas.
Cisco ISE is designed for scalability. It splits the functions it serves into several personas to enable scalability.
An ISE node is a single (virtual or physical) appliance that is configured to execute one or more of the four personas available in an ISE deployment.
In the event of a standalone or two-node deployment, a single ISE node can be configured with only one persona, several personas, or even all personas.
The following are the four personas:
1. Administration (PAN)
2. Monitoring (MNT)
3. Policy Services (PSN)
4. pxGrid
Policy Administration Node (PAN)
The Administration persona is the first, and probably most significant, persona. This Cisco ISE feature is essential since it allows a network administrator to design and manage the network security policy.
This Cisco ISE Administration persona feature is most important because it allows a network administrator to configure and optimize network security policies.
A network administrator must use the administrative persona’s graphical user interface (GUI) to change the security policy on Cisco ISE, whether it be authentication, authorization, profiling, posturing, or any other policy.
- It is Cisco ISE’s central control center
- All ISE policies are set up in the PAN and then synchronized to all other ISE nodes and personas.
- The platform’s licensing functionality is also included in the PAN.
- The built-in certificate authority uses a PAN as the root.
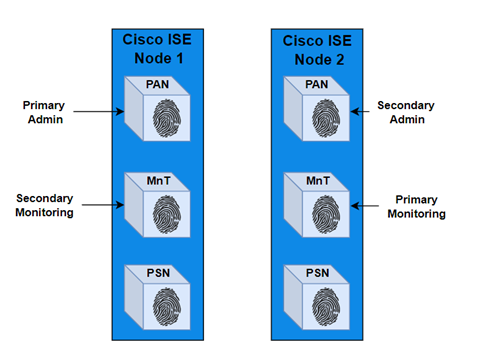
- The Administration persona can have a maximum of two nodes: a primary PAN and a secondary PAN for redundancy.
Monitoring and Troubleshooting Node (MnT)
This node’s function is precisely what it sounds like:
Monitoring: When an endpoint connects to a Policy Services node (PSN), events are generated to track the authentication and authorization process. These events are sent to the MnT node, which aggregates and processes them into a readable format.
Troubleshooting: The authentication or authorization procedure might be successful or unsuccessful as each event is transmitted to the MnT node. The content of the logs on the MnT node is likewise incredibly detailed due to the detailed event tracking that occurs on the PSNs. If a user or endpoint is having trouble connecting to the network, a network administrator may utilize the MnT node to identify what is causing the problem because it monitors the user’s/authentication endpoints in real time.
- The Monitoring persona serves as the ISE cube’s centralized logging server.
- In an ISE cube, there can only be two MnT nodes: a primary MnT node and a secondary MnT node for redundancy.
Policy Services Node (PSN)
The Policy Services persona performs a variety of tasks and is often referred to as “the workhorse.” The RADIUS server for the ISE cube is a node running the Policy Services persona, which handles authentication requests, performs identity lookups and policy checks, and issues the resultant authorization result.
The NAD delivers the RADIUS Access-Request and subsequent packets to the specified PSN when a user authenticates to the network (s). With the entire security policy pushed by the PAN, the PSN(s) may authenticate the user and give the required authorization policy in a self-contained manner.
PSN is also responsible for sending the NAD a Change of Authorization (CoA) notification. The dynamic authorization setting, which allows the PSN to force a reauthentication, must also be present on the NAD. The PSN creates the CoA and sends it to the NAD without the involvement of the PAN.
- The PSN is also responsible for hosting various online portals for guest access and sponsorship opportunities.
- The ISE PSN persona is responsible for endpoint profiling.
- SGT Exchange protocol service
- Device administration (TACACS+)
- Passive identity service
- In addition to being the issuing CA for the built-in ISE CA
- For scalability and distribution of PSN functions and load, each ISE cube can have up to 50 PSNs.
pxGrid Persona
The pxGrid persona is the final persona in an ISE cube. Cisco’s pxGrid publish and subscribe communication bus was built from the ground up to be a scalable, secure data-sharing solution.
In other words, it’s built to communicate a large amount of security data in a scalable and efficient manner.
If you’re considering a new Cisco ISE deployment, a migration from a traditional AAA solution to Cisco ISE, or adding additional functionality to an existing Cisco ISE solution. You can always contact us; the Zindagi Technologies team includes professionals in Network Security, VPN Solutions, Data Center technologies, Enterprise & Service Provider Networks, Virtualization, Private Cloud, Public Cloud, Data Center Networks, security, and a variety of other technologies. We will be happy to assist you. Please contact us at +91-9773973971.
Author
Ravi Kumar Singh
Consultant – Network Security

Cisco SD-Access | Set Up SD-Access Fabric | Zindagi Tech
September 19, 2022[…] to interface with the software, makes the SD-access services available to users. Three appliances, Identity Service Engine (ISE), Application Policy Infrastructure Controller Enterprise Module (APIC-EM), and Network Data […]
Understanding AAA and its need | Zindagi Technologies
November 10, 2022[…] Cisco ISE (Identity Service Engine) is said to be a next-generation network access control solution that enables a dynamic and automated approach to enforce policies. […]