A Brief Introduction of Cisco ISE
Our goal as Network Security Engineer is to be able to secure network access of endpoints connected over networks. E.g., Windows Desktop users connected to the office network switch. We have wired or/and wireless users in offices trying to connect to an office network or remote users connecting to an office network over an SSL VPN, and we want to make sure that only authenticated user/device gets access to the network, any user/device fails authentication must not get access to the network/resources.
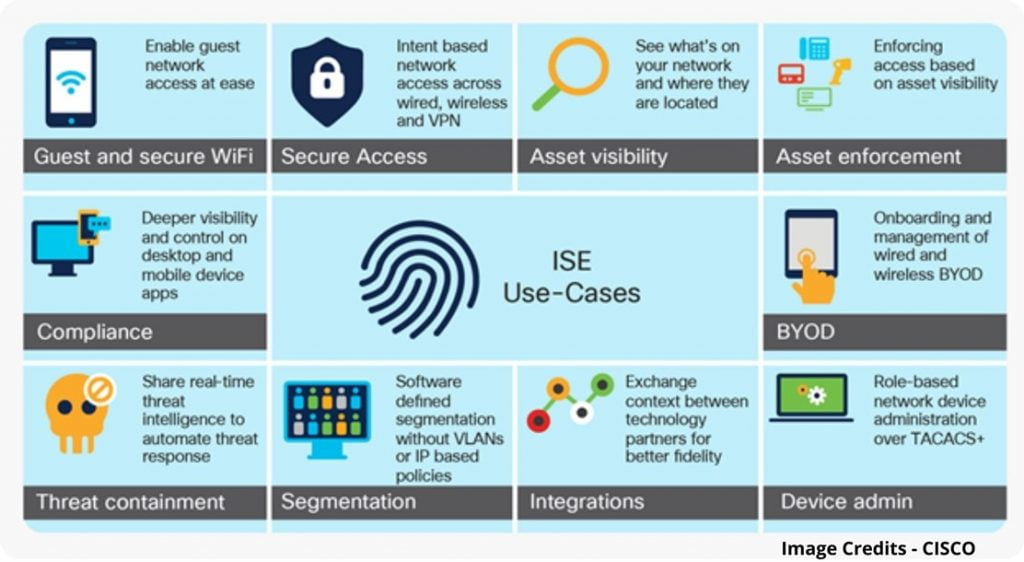
Also, we need to ensure that the authenticated user should only get access to the authorized network/resources. Once the user/device gets access, the accounting should be in place which logs when the user/device gets authenticated and authorized, etc. To achieve all these requirements in 1 solution we have an AAA server that provides the Authentication, Authorization, and Accounting services. Cisco offers a product called Cisco Identity Services Engine (ISE) which provides AAA services and more advanced features.
Authentication Types and its Policy
Cisco ISE provides edge authentication services for a network in a variety of ways.
1. IEEE 802.1x authentication
2. MAC Authentication Bypass
3. Web Authentication
4. Posture Assessment Device Profiling
5. External Mobile Device Management (MDM) Integration
6. Authentication via API
To perform the above functions, Cisco ISE integrates with Network Access Device (Switch, Wireless Controller, VPN Concentrator) using the RADIUS protocol. Cisco ISE provides standard RADIUS compliant features, also it provides an additional proprietary feature. AAA is not just configured on NAD but also the Cisco ISE which goes through devices/endpoints connecting network.
When Cisco ISE receives a RADIUS authentication request, first it goes to the Authentication Policy this is where Cisco ISE determines the identity of the user or device. This process could involve 802.1x authentication, MAB, or Web Authentication.
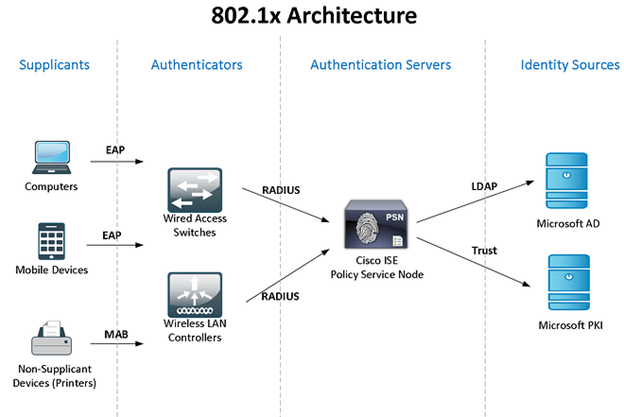
For Authentication, if the password is presented in the RADIUS auth request message, the password can be validated against the local ISE directory or AD or LDAP database. If a certificate is used for authentication, it can be validated against the Certification Authority Certificate Chain and its expiry status. If the MAC address is used for authentication, it can be validated against the MAC addresses in the MAC Database of ISE. If the Password, Certificate, MAC is invalid then ISE will send a RADIUS-access-reject message to the NAD.
The purpose of Authentication is only to determine the identity of the user/device whether it is valid or not. But the question is what to do with the valid/authenticated user or what level of access to be provided to the authenticated user is the role of Authorization Service/Policy in Cisco ISE.
As per the Authorization Policy, the User/Device can get access in the following ways.
1. Free/Full Access to the network resources
2. No Network Access
3. Access to the Network and Resources with some limitation
Free/Full Access – This is mostly applicable to IT admins who require access to everything.
No Network Access – When we know who the user or device is, but we do not want them to have any access. In that case, the User/device will succeed in authentication but fail in the authorization.
Limited Access – The typical example of Limited access could be Marketing Users should only access marketing servers or maybe Finance Users should only access Finance Servers.
Are you Planning to Deploy Cisco ISE for Secure Network Access in your Environment?
If you are planning for a Green-field Deployment, Tech Refresh, Migration from your legacy AAA Solution to Cisco ISE Solution or for implementing advanced features in your already deployed Cisco ISE Solution. You can always reach out to us, the team at Zindagi Technologies consists of experts in the field of Network Security, VPN Solutions, Data Centre technologies, Enterprise & Service Provider Networks, Virtualization, Private Cloud, Public Cloud, Data Center Networks (LAN and SAN), Collaboration, Wireless, Surveillance, Openstack, ACI, storage and security technologies with over a 20 years of combined industry experience in planning, designing, implementing and optimizing complex Network Security and VPN deployments. We will be glad to help you. Call us on +919773973971.
Author
Harpreet Singh Batra
Consulting Engineer- Data Center and Network Security
