Explaining RADIUS and its Attributes.
The Remote Authentication Dial In User Service (RADIUS) is a network access control protocol that handles authentication, authorization, and accounting.
RADIUS is used to transport RADIUS-encapsulated EAP packets between the NAS and an authentication server in RADIUS/EAP.
It uses UDP Port numbers 1812 & 1813 UDP
1812: – On 1812 Port Number authentication and authorization both happen at the same time.
1813: – On 1813 Port Number Accounting happen only.
RADIUS Massages
- Access Request: – This carries user identity.
- Access Reject: – When authentication or authorization fails, this occurs.
- Access Accept: – This occurs when both authentication and authorization have been completed successfully.
- Access Challenge: – For that identity give me a password.
Some Background information about RADIUS
The User Datagram Protocol is used to communicate between a network access server (NAS) and a RADIUS server (UDP). The RADIUS protocol is generally regarded as a connectionless service. The RADIUS-enabled devices, not the communication protocol, handle issues like server availability, retransmission, and timeouts.
RADIUS is a server/client protocol. RADIUS clients are mainly NAS devices, and RADIUS servers are usually daemon processes running on UNIX or Windows NT machines. (Examples include Cisco ISE, Aruba Airpass, Fortinet FortiNAC, and others.) The client sends user information to authorized RADIUS servers and responds to the response. RADIUS servers accept user connection requests, authenticate the user, and then return the configuration information that the client needs to provide service to the user.
Authentication and Authorization
The RADIUS server can authenticate a user using a variety of methods. It can support PPP, PAP or CHAP, UNIX login, and other authentication protocols when given the username and password by the user.
When the RADIUS server receives an Access-Request from the NAS, it looks for the username in a database. If the username does not exist in the database, the RADIUS server either loads a default profile or sends an Access-Reject message right away. This Access-Reject message can be accompanied by a text message that explains why the request was denied.
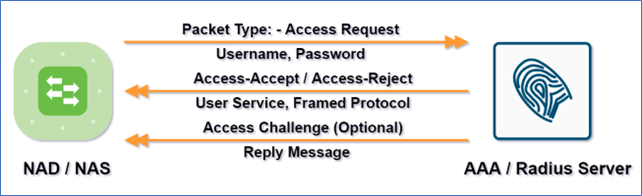
Authentication and authorization are combined in RADIUS. If the username and password are correct, the RADIUS server responds with an Access-Accept response that includes a list of attribute-value pairs that specify the session parameters. Service type, protocol type, IP address to assign the user, access list to apply, or a static route to install in the NAS routing table are all common parameters. What will be installed on the NAS is determined by the RADIUS server’s configuration information.
The RADIUS authentication and authorization sequence are depicted in the diagram above.
Accounting
RADIUS accounting capabilities allow data to be sent at the start and termination of sessions, showing how much time, packets, bytes, and other resources were consumed during the session.
A shared secret is used to authenticate transactions between the client and the RADIUS server, and it is never transferred over the network. Furthermore, user credentials are provided encrypted between the client and the RADIUS server to eliminate the potential of a user’s password being discovered by someone snooping on an insecure network.
RADIUS AVP (Attribute Value Pairs)
AVP (attribute value pairs) are what the ISE Server uses to create contextual data. There are 190 properties that you may find by searching on Google, but we’ll focus on the most important AVP attributes that you need to master.
| IETF Number | IETF Attribute |
| 1 | Username |
| 2 | User-Password |
| 4 | NAS-IP-Address |
| 6 | Service-Type |
| 26 | Vendor-Specific |
| 30 | Called-Station-Id |
| 31 | Calling-Station-Id |
| 61 | NAS-Port-Type |
| 79 | EAP-Message |
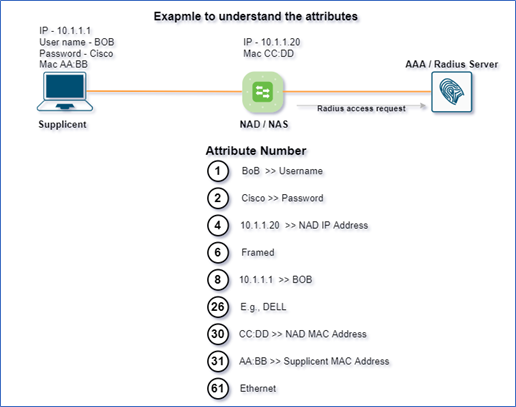
Attribute 1: – Username
User’s claimed identity.
Attribute 2: – User-Password
User’s Password (String)
Attribute 4: – NAS-IP-Address
This is something the supplicant does not tell the authenticator, but which the authenticator adds to make the information more specific.
Attribute 6: – Service-Type
The service type is divided into two:
- Framed: – If the service type field is filled with “framed” that means IT is coming with a username.
- Call check: – If it is coming with “Call Check” that means IT is a MAC address.
Note: –
- If the end-user comes with MAC Address, Attribute will go as NULL.
- Instead of a username, it will use the MAC address.
Attribute 26: – Vendor-Specific
It will carry the MAC address, using the MAC Organizationally Unique Identifier address it identifies the Vendor-Specific devices.
Attribute 30: – Called-Station-Id
It is the MAC address of NAD/NAS.
Attribute 31: – Calling-Station-Id
It is the MAC address of the Supplicant.
Attribute 61: – NAS-Port-Type
This tells the story of how a user is getting connected with the network in three ways
- Wired: – That means the endpoint is connected to the ethernet cable. (Physically connected).
- Wireless: – That means the endpoint is connected to wireless.
- Virtual: – That means the endpoint is connected to VPN.
Attribute 79: – EAP-Message
AVP 79 is the one that is going to incorporate the EAP messages into the RADIUS packet.
In our future blog, we’ll go over EAP and its flavors in further detail.
Zindagi Technologies is the top IT Consulting Services provider company in Delhi and provides a lot of services apart from IT consulting. Having hands-on experience in Cybersecurity, Cloud Management, Managed IT Services, IoT services, VAPT Assessment, Disaster Recovery, End-user computing, DevOps, and many more just to cater to your business needs.
If you want to deploy CISCO ISE or any other NAC solution or any other CISCO Product with its full functionality or maybe you want to implement advanced features, you can always contact the team at Zindagi Technologies, which consists of experts in the fields of Data Center, SD-Access, SD-WAN, Virtualization & Cloud Services, Collaboration, Wireless device Deployments, and many other technologies. Give us a call at +919773973971 and we’ll be happy to offer you, our services.
Author
Ravi Kumar Singh
Consultant – Network Security

RADIUS Protocol & Messages | Zindagi Technologies
November 17, 2022[…] What Are The Different Types Of RADIUS Messages? […]