EAP Flavors – A Detailed Explanation.
EAP stands for Extensible Authentication Protocol. We will learn about EAP flavors as they come in a variety and in this blog we will learn about the three most used options.
The EAP is divided into two sections. The first is tunnelled, and the second is non-tunnelled.
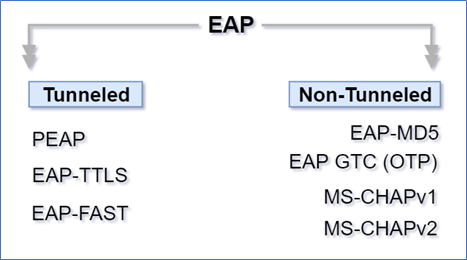
PEAP (Protected Extensible Authentication Protocol)
- The client encrypts data using the server certificate.
- Security works much like a website using SSL/TLS.
- Does not necessitate the use of a client certificate.
EAP-TTLS (Extensible Authentication Protocol – Tunneled Transport Layer Security)
- For mutual authentication, both server and client certificates are required.
- For example, the network recognizes bob for accounting, and bob recognizes that he is genuinely connecting to the present network rather than the spoof SSID.
- It is seen to be the safest option.
EAP-FAST (Secured Tunneling for Flexible Authentication)
- Does not require client certificates.
- Use PAC files to create the secure tunnel.
- It is possible to utilize it for both machine and user authentication at the same time.
- Require the AnyConnect supplicant on the workstation.
PEAP (Protected Extensible Authentication Protocol)
PEAP is Microsoft property, and Microsoft has made it available to the rest of the world. It is the default protocol on Microsoft machines, and it protects data using TLS. “TLS protects the EAP,” hence why it is called Protected EAP.
TLS protects the EAP through certificate exchange; however, client certificates are not required in that certificate exchange.
It follows the Inner method: – GTC (OTP), Ms-Chap).
It follows the outer method: – TLS.
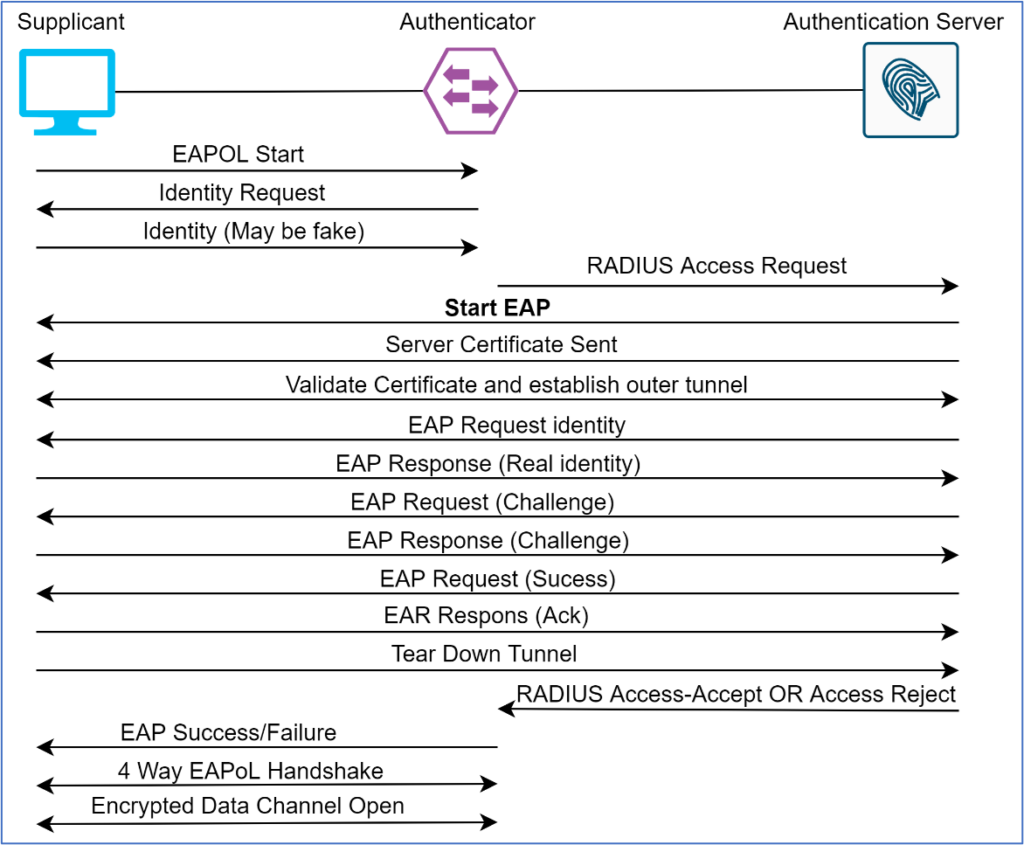
Note: –
- Depending on the tunnelled protocol you are utilizing, what outer method you will use.
- My outer method is TLS if my tunnelled protocol is PEAP.
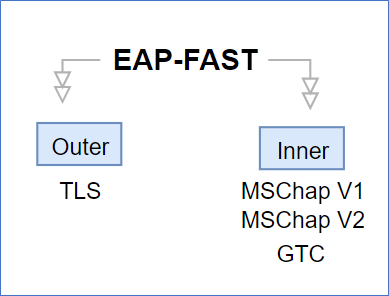
EAP-FAST (Flexible Authentication via Secure Tunneling)
EAP-FAST is a Cisco property, and Cisco has made it available to the rest of the world, just like PEAP EAP-FAST also uses an outer header or Outer method TLS.
Just like PEAP it also does not require a client certificate
But EAP-FAST Creates a PAC file that pushes toward clients.
It uses PAC (Protocol Access Credentials) (Best for ramming users)
What is PAC?
Consider PAC is a cookie / A secure Cookie, that is stored locally on the host machine as s proof of successful authentication.
When a client roams or is disconnected from the network temporarily, this PAC is used for quick session resumption.
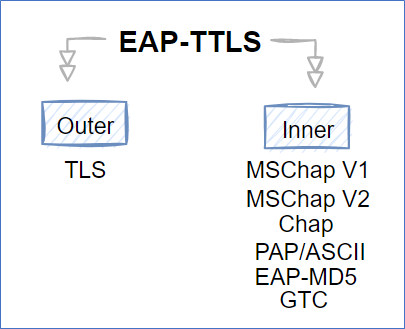
EAP TTLS (Extensible Authentication Protocol Tunnelled Transport Layer Security)
EAP TTLS is Funk Software (Juniper Networks) proprietary, and Juniper has made it available to the rest of the world.
The only difference between this and others (EAP-FAST, PEAP) is it requires/ demands the client certificate also.
TEAP (Tunnel-based Extensible Authentication Protocol)
TEAP is a tunnel-based Extensible Authentication Protocol method that creates a secure tunnel and then performs other EAP methods within that tunnel’s protection.
After the initial EAP Identity request/response exchange, TEAP authentication takes place in two stages.
TEAP employs the TLS handshake in the first phase to perform an authorized key exchange and construct a protected tunnel. The second phase begins after the tunnel is formed, with the peer and server engaging in further dialogue to build the appropriate authentications and authorization policies.
Note: –
- The TEAP Protocol is supported by Cisco ISE 2.7 and above.
- Microsoft included support for TEAP in Windows 10 version 2004 (released in MAY 2020).
- To know more about TEAP Please refer to the RFC 7170
Zindagi Technologies is a leading IT Consulting Services provider in Delhi that implements security, Enterprise network, cloud security, data center, hybrid cloud, Campus networks, server devices, and much more, as well as develops network architecture and provides DevOps services in public and private sectors. If you require any support, please contact us directly or phone us at +91-9773973971.
Author
Ravi Kumar Singh
Consultant – Network Security
