What is 802.1X & Packet flow?
The first thing to know about 802.1X is that it is not a specific object or protocol. Furthermore, 802.1X is part of a wider system of network access controls known as NAC solutions in the market. One example of a NAC system is Cisco ISE. (Cisco Identity Service Engine) 802.1X is a network-level authentication and authorization mechanism that is essential to any NAC solution.
A system of hardware/software components and protocols make up the 802.1X authentication framework. Endpoint users and/or endpoint devices are required to authenticate themselves before being provided (possibly) differing levels of access to a wired or wireless network connection in IP networks.
Before we go into the 802.1X Packet Flow, let’s have a look at essential components that must be understood before we can grasp 802.1X packet flow.
- Supplicant
- Authenticator
- Authentication Servers
Supplicant
A supplicant is a network device that collects end-user authentication credentials and passes them on to the authentication process. For example, a software application or an operating system-related process running on a laptop connected to a network port. A Supplicant can be connected to a network via wireless, wired, & VPN.
Authenticator
The Authenticator is a network access device that receives and relays authentication credentials from the Supplicant to the Authentication Server for verification.
Authentication Server
The Authentication Server is a network server that checks the credentials received by the supplicant against the information contained in its database and decides whether to grant or deny the supplicant network access. Any AAA server can be used as the authentication server.
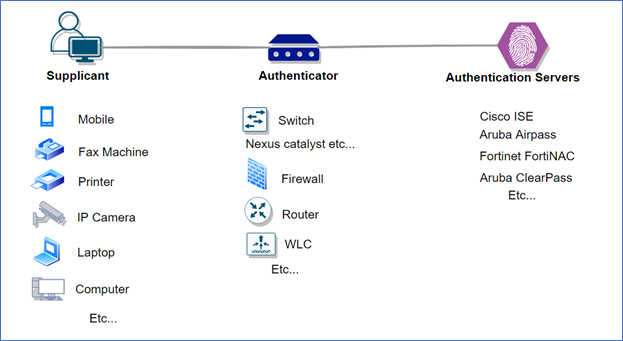
Note: We can have multiple hops between Authenticator (NAD) and the Supplicant.
Also, there can be multiple hops between Authenticator (NAD) and Authentication Servers (AAA Server).
Before starting 802.1X we need to understand EAP (Extensible Authentication Protocol)
- 802.1X (EAPoL) is a delivery mechanism and it does not provide the actual authentication mechanism.
- When utilizing 802.1X, you need to choose an EAP type:
Such as transport layer security (EAP-TLS) or PEAP, which defines how the authentication takes place.
EAPs are broadly cartridge by two
- Tunnelled
Does not carry identity
It’s Protected
E.g., PEAP, EAP-FAST, EAP-TLS
- Non-Tunnelled
Carry the identity
Clear text
E.g., CHAP, MS-CHAPv1, MS-CHAPv2
Let’s start with the 802.1X packet flow now that we’ve covered all three important components: Supplicant Authenticator & Authentication Servers.
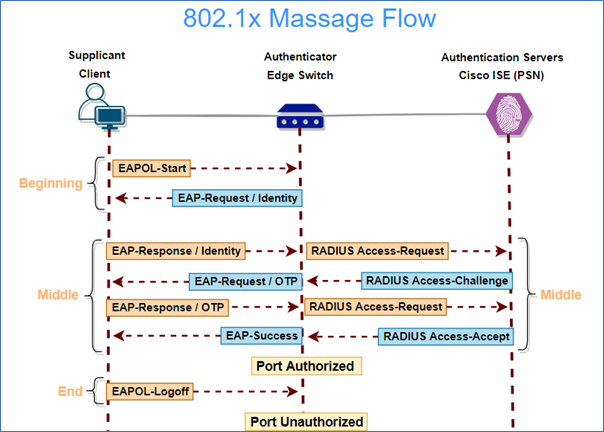
Between the Authenticator (NAD) and the Authentication Server, the RADIUS protocol is used (AAA) Cisco ISE is a AAA server in the diagram above.
Supplicants are pieces of software that run on endpoints. The user/device authentication credential must be provided to the authentication server by the supplicant. The Authenticator receives this credential from the supplicant via the Extensible Authentication Protocol (EAP). EAP is a link-local protocol, which means it can only be sent between two devices that are connected directly, such as an endpoint and a switch or an endpoint and a wireless AP/controller.
As a result, the authenticator’s duty is to use RADIUS encapsulation to proxy this EAP data from the supplicant to the authentication server, which is a routable protocol capable of being communicated to any reachable destination on an IP network. The responsibility of the Authentication Server is to validate/authenticate the credential received in the RADIUS communication and return an authorized response to the authenticator.
The credential given to the authentication server can represent either the device or the user that is requesting network access, or both. Identity Sources are identity stores/directories that an authentication server (such as Cisco ISE) can utilize to verify the supplicant’s authentication credentials.
In our future blog, we’ll go over 802.1X EAP and RADIUS in further detail. We’ll also learn about RADIUS AVP (Attribute value pairs) and more.
Zindagi Technologies is the top IT Consulting Services provider company in Delhi and provides a lot of services apart from IT consulting. Having hands-on experience in Cybersecurity, Managed IT Services, VAPT Assessment, End-user computing, DevOps, and many more just to cater to your business perspective. If you want to deploy CISCO ISE or any other NAC solution or any other CISCO Product with its full functionality or maybe you want to implement advanced features, you can always contact the team at Zindagi Technologies, which consists of experts in the fields of Data Center, SD-Access, SD-WAN, Virtualization & Cloud Services, Collaboration, Wireless device Deployments, and many other technologies. Give us a call at +919773973971and we’ll be happy to offer you, our services.
Author
Ravi Kumar Singh
Consultant – Network Security

Implementing 802.1x on wired network | Zindagi Technologies
June 10, 2022[…] currently use an intermediate solution to secure their wired networks. This entails using a mix of 802.1x and MAC Authentication Bypass (MAB). The endpoints that connect to the access layer can be […]