Guest Access with Cisco ISE
Guest Access Overview
Getting concise information on the multiple modes of Guest Access on ISE can be a bit of a challenge as there is a lot of information out there. This blog will provide a concise and simple-to-understand summary of the different modes available, their nuances and help you choose which will be most suitable for your environment.
If any outside user wants to access the internet or the resources and services in your network by using your companies’ network, then you can provide them Guest Access portals by using it they can connect to your network. Most guests have authorized visitors or other temporary users who require access to your network.
Cisco ISE supports 3 kinds of guest access portals.
>Hotspot Guest Portals
>Sponsored Guest Portals
>Self-Registered Guest Portals
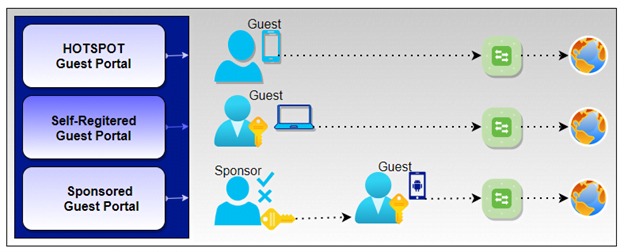
Network Access with Hotspot Guest Portals
A Hotspot Guest Portal provides network access to guests with the Acceptable Use Policy (AUP). In the Hotspot guest portal, guests do not require usernames and passwords. When guests connect to a network, they try to access any website on the browser then they will be redirected to the ISE Hotspot Guest Portal where they must accept an Acceptable Use Policy (AUP) to get the network access. When the guest accepts the AUP then the device MAC will be stored in the ISE database. With the Hotspot guest portal, you can provide internet access without authentication.
If any change happens in page settings, you will get those changes in the graphical flow in the Guest Flow diagram. Such as if you enable/disable the AUP page, it will appear in the flow and the guest will also experience the same in the guest portal.
Note: – Administrator has an option to enable an access code. In that case, guests required an access code to log in.
Network Access with Self-Registered Guest Portals
A self-Registered portal is a kind of credentialed guest portal. In this portal, guests need to have a username and password to access the network. Guests have the authority to create their own account with username and password in the self-registered portal. Which they use to log in to the guest portal and gain internet access through the campus network. In this portal, users can create their accounts with their email id or mobile number.
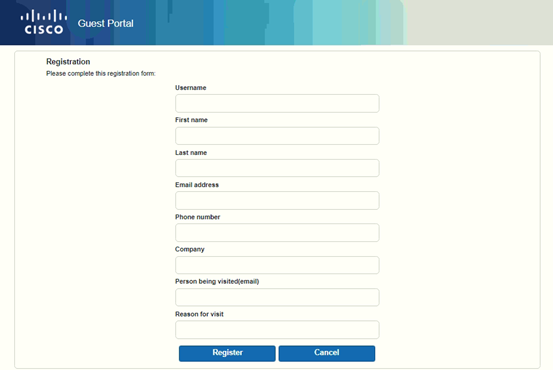
A self-Registered guest portal is used when you want that guest to do the self-registration without any employee approval by the sponsor.
Network Access with Sponsored Guest Portals
The sponsored guest portal is also a credentialed guest portal. The sponsored-Guest portal is used to enable designated sponsors to grant access to guests. In enterprises, you require more secure network access than railway stations and coffee shops. To maintain a company’s confidentiality and data integrity, network access security is very important. While providing network access to guests, the sponsor should adhere to your company guidelines. For the entire process, Cisco ISE stores and records to audit and report purposes. You can use that database for future monitoring of unauthorized access detection.
ISE admin can create a new Sponsored-Guest portal or can edit or duplicate an existing one. They can delete any Sponsored-Guest portal, including the default portal provided by Cisco ISE.
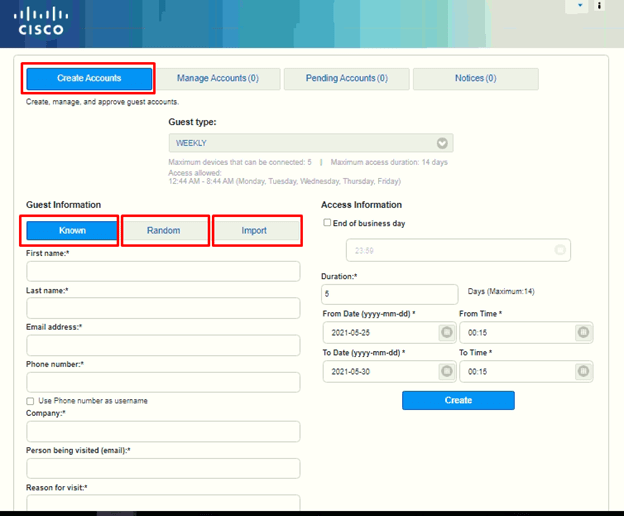
Sponsor Portal Create Accounts Page
You can use the Create Accounts page to create accounts for the following authorized visitors:
- You can create the known guest accounts for the users, whose personal information, such as last name, email address, or phone number, is available to you.
- If you do not have any personal information of the guests but want to generate the template for future usage then you can create the random guest accounts.
- Import Guest Accounts: – Guests can be imported if any external database present and can assign the time.
Now that we know the various kinds of Guest Access provided with Cisco ISE, you will be empowered to make an informed decision as to which Guest Access portal will be most suitable for your environment. Reading this overview will not only save your time in deciding right now but also in the future as selecting the correct deployment will require lesser reconfigurations and since your environment could be dynamic, it will benefit you to know which other modes of deployments are available in case your requirements change.
While this blog has been able to provide you with an overview of the different Guest Access modes available, there are finer details which one might have to consider during deployment for which you can refer to the Cisco ISE Guest Access Prescriptive Deployment Guide.
We at Zindagi Technologies have successfully deployed Cisco ISE at multiple locations including SMB’s and Enterprise level environments so if you need any consultation with regards to designing and implementation, please feel free to reach out to us at Zindagi Technologies or +91 9773973971.
Author
Chakransh Awasthi
Senior Network Security Consultant
