How Can Host Intrusion Prevention System Protect Against Malicious Attacks?
Host Intrusion Prevention System solutions protect the computer against known and unknown malicious attacks. In case of attempted major changes by a hacker or malware, HIPS blocks the action and alerts the user so an appropriate decision about what to do can be made.
This helps to keep your system secure without having to rely on a specific threat to be added to a detection update. If a threat actor or virus tries to change the operating system, the host intrusion prevention system blocks the activity and notifies the potential victims so they can take proper action.
What is the difference between IDS and IPS?
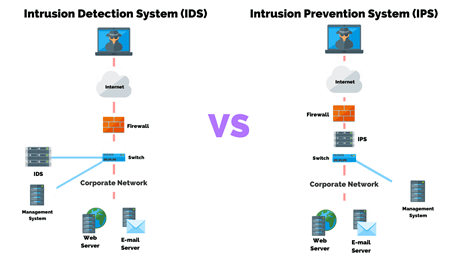
Similar to a firewall, IPS is deployed inline to the traffic flow. IPS is an active network component that examines every passing packet and takes the correct remedial action per its configuration and policy. In contrast, IDS is a passive component typically not deployed inline and instead monitors the traffic flow via span or tap technology to then raise notifications.
How Do HIPS Detect Threats?
The normal method of a HIPS is runtime detection. It intercepts actions when they occur, but some HIPS also offer pre-execution detection. This means that the nature of an executable is analyzed before it runs, to check for suspicious behavior. Risks associated with HIPS are false positives and wrong user decisions.
What are the key features of HIPS?
· Day-zero protection: Stop malicious exploitation of systems and applications; prevent the introduction and spread of malicious code
· Hardened systems: Lockdown OS, applications, and databases; prevent unauthorized executables from being introduced or run
· Integrated firewall: Blocks inbound and outbound TCP/UDP traffic; administrator can block traffic per port, per protocol, per IP address, or range
· Maintain compliance by enforcing security policies on clients and servers
· Buffer overflow protection
· Real-time File Integrity Monitoring detection on Windows, Linux.
What are the different policies of HIPS?
Out-of-the-box security policies offer the following features:
– Intrusion prevention
· Proactive security against day-zero attacks
· Protection against buffer overflow and memory-based attacks
· Out-of-the-box operating system hardening
· External device protection
· Administrative privilege de-escalation
– Intrusion detection
· Policy-based auditing and monitoring
· Log consolidation for easy search, archival, and retrieval
· Event analysis and response capabilities
· File and registry protection and monitoring
Some Disadvantages Of HIPS:
Now that we talked about the benefits, let’s take a quick look at the disadvantage of HIPS. A drawback would be that the response taken may leave the host ineffective or even affect the availability of a vital resource. Incorrect user decisions and false positives are also menaces linked to host intrusion prevention systems.
Host Intrusion Prevention Systems (HIPS) can be an extremely important component of stratified protection if combined with a minimum of one detection-based security solution. Users and organizations should definitely benefit from HIPS, but it is essential to have some knowledge of how to use it successfully. If you need any assistance in protecting your organization against malicious attacks and want to secure the data then give us a call on +919773973971 or drop us an email.
Author
Shivam Rana
Associate Consultant
