How To Understand ‘Tcpdump’ Command; The Better Way.
Knowing tcpdump is an essential skill that will come in handy for any System Administrator, Network Engineer, and security professional.
Tcpdump is an immensely powerful command-line interface packet sniffer. It must be launched as root or with superuser rights because of its use of the promiscuous mode or to be sure to have sufficient privileges on a network device or a socket.
Installing Tcpdump Command
By default, Tcpdump is installed when we install an operating system. To check if the Tcpdump command is available on your system.
~] #tcpdump –version
Output –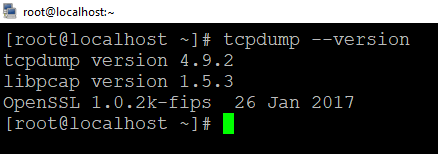
If case tcpdump command is not present in your system, you can easily install tcpdump using this package manager of your distributor.
Install Tcpdump on Ubuntu and Debian
$ sudo apt update && sudo apt install tcpdump
Install Tcpdump on CentOS
$ sudo yum install tcpdump
Garnel Syntax Of This Command
tcpdump [ option ] [ expression ]
Here,
option = control the behavior of the command.
expression = define which packets will be captured.
Break Down Options and Expressions
First, we should know about tcpdump command and what is it used for and then break down the tcpdump command Line.
~] #tcpdump -i ens33 -nn -s0 -v port 443Here,
i = Select interface on which the capture is to take place, this will often be an ethernet card or wireless adapter but could also be a VLAN or something more unusual. It is not always required it is only on a network adapter.
-nn = A single (n) will not resolve hostnames. A double (nn) will not resolve hostnames or ports. This is handy for not only viewing the IP / port numbers but also when capturing a large amount of data, as the name resolution will down the capture.
-s0 = Snap length, is the size of the packet to capture. -s0 will set the size to unlimited- use this if you want to capture all the traffic. Needed if you want to pull binaries/files from network traffic.
-v = Verbose, using (-v) or (-vv) increases the number of details show in the output, often showing more protocol-specific information.
Port 80 = This is a command port filter to capture only traffic on port 80, which is of course usually https.
Check, All The Interfaces In The Machine.
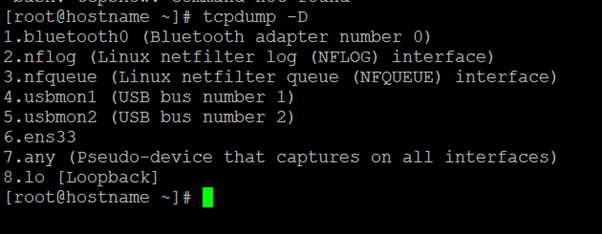
In this example above, you can see all the interfaces available in my machine. The special interface any allows capturing to any active interface.
Understanding The Output Format
Tcpdump is capable of capturing and decoding many different protocols, such as TCP, UDP, ICMP, and many more. While we cannot cover all of them here, to help you get started, let’s explore the TCP packet.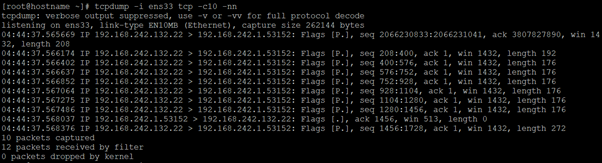
The fields may vary depending on the type of packet being sent, but this is the general format.
Explain All Fields Individually
First field – 04:44:37,566174 represents the timestamp of the received packets as per the local clock.
Second field – IP represents the network layer protocol – In this case IPv4,
For the IPv6 packet, the value is IP6.
Third Field – 192.168.242.132.22 is the source IP address and port. This is followed by the destination IP address and port, represent by 192.168.242.1.53152. After the source and destination, you can find the TCP flags [P.]. Typical values for this field include:
| Value | Flag Type | Description |
| S | SYN | Connection Start |
| F | FIN | Connection Finish |
| P | PUSH | Data Push |
| R | RESET | Connection Reset |
| . | ACK | Acknowledgment |
Fourth Field – Fourth field is the sequence number of the data contained in the packet, seq 208:400.
Fifth Field – This field is followed by Ack number ack 1, it is 1 since this is the side sending data.
Six Field – It is window size win 1432 which represents the number of the bytes available in the receiving buffer.
And finally, we have packet length, length 192 which represents the length, in bytes, of the payload data.
In this blog, we understand how tcpdump command works and how we capture all traffic in Linux. For more options you can have a look at the tcpdump man page.
Hope this blog post has been helpful to you and precious time by foretelling the issue one could face to understanding this command. In case if you are still having trouble with this or need any further suggestions or support, please feel free to connect
Zindagi Technologies holds a combined experience of more than 2 decades and has been vigilant and expert in Data Center Services, Network Design Implementation, Security Services, and much more. Call us on +919773973971 for more details.
Author
Deepak Kumar
Linux and Server Administrator
