To and Through the Cisco ASA Firewall
Our goal as a Network Security Engineer is to be able to provide security of communication and restrict access from insecure networks. E.g. Internet. We use Firewall very commonly to restrict unwanted communication between various private networks and public networks. E.g. If we are hosting a Web Server in our environment, we expect only http or https traffic for it, so we only allow port 80 and 443 access from the Internet to our Private network (specifically to that Web Server) on Firewall. Today we will be discussing the default behavior of a very well-known Cisco Firewall i.e. ASA for traffic To the Firewall and Through the Firewall.
Topology
In order to understand and discuss the scenarios for traffic To and Through the Cisco ASA Firewall, let’s refer to the below mention topology for better understanding.
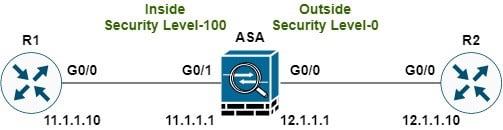
In the above topology, there are 2 routers connected to Cisco ASA Firewall with point-to-point connectivity. ASA is configured as a Routed Firewall with Inside and Outside Zone. We know that by default Cisco ASA uses 100 security levels for the Inside interface and 0 security levels for any other interface with a name other than Inside.
To the ASA Firewall
Task-1
What if I ping from R1 to ASA Firewall Inside interface (11.1.1.1)? Will it ping?
Answer- Yes, it will ping as it is a point-point link.
Task-2
What if I ping from R2 to ASA Firewall Outside interface (12.1.1.1)? Will it ping?
Answer- Yes, it will ping as it is a point-point link.
Task-3
Now, Let’s suppose we have configured telnet on Cisco ASA Firewall so that R1 and R2 can telnet the ASA Firewall. What if I telnet from R1 to ASA Firewall inside interface (11.1.1.1)? Will I be able to take telnet from R1?
Answer- Yes, as R1 is reachable to ASA Firewall Inside Interface and ASA is enabled for Telnet.
Task-4
What if I telnet from R2 to ASA Firewall Outside interface (12.1.1.1)? Will I be able to take telnet from R2?
Answer- Interestingly NO, Telnet is clear text traffic. By default, ASA only allows telnet to ASA firewall from security level 100. ASA does not allow telnet from any interface other than 100 security level.
Task-5
Now, Let’s suppose we have configured SSH on Cisco ASA Firewall so that R1 and R2 can SSH the ASA Firewall. What if I SSH from R1 to ASA Firewall inside interface (11.1.1.1)? Will I be able to take SSH from R1?
Answer- Yes, as R1 is reachable to ASA Firewall Inside Interface and ASA is enabled for SSH.
Task-6
What if I SSH from R2 to ASA Firewall Outside interface (12.1.1.1)? Will I be able to take SSH from R2?
Answer- Interestingly YES, Telnet didn’t work but SSH worked because SSH traffic is secure/encrypted. By default, ASA Firewall allows SSH traffic from any interface as long as ASA is configured correctly.
Through the ASA Firewall
Task-1
Now, Let’s suppose we have configured Telnet on R1 and R2 so that we can telnet R1 and R2 from one another. What if I telnet from R1 to R2 (12.1.1.10)? Will I be able to take Telnet from R1?
Answer- Yes, because the traffic from Higher Security Level to Lower Security Level is allowed in ASA Firewall by default. Also, ASA is a Stateful Firewall so the return traffic from R2 to R1 will also be allowed because of the active connection in the connection table.
Task-2
What if I telnet from R2 to R1 (11.1.1.10)? Will I be able to take Telnet from R2?
Answer- No, because the traffic is not allowed by default from Lower to Higher Security level in ASA Firewall. If we want traffic to be allowed from Lower to Higher Security levels, we need to configure an access list to explicitly allow traffic from Outside to Inside.
Note:- Even though if we do SSH the result will be the same as the above 2 tasks. When traffic is supposed to pass through Firewall, By default ASA doesn’t care whether it is encrypted traffic or plain text
Task-3
What if I ping from R1 to R2 (12.1.1.10)? Will I be able to ping R2 from R1?
Answer- Interestingly NO, No matter what, the traffic is from Higher to Lower Security Level, Ping does not work by default in ASA Firewall. The reason is that ICMP inspection is not enabled by default in ASA, it needs to be explicitly enabled then only ping works.
Task-4
Now, Let’s suppose we enable ICMP inspection in the ASA firewall. What if I ping from R2 to R1 (11.1.1.10)? Will I be able to ping R1 from R2?
Answer- No, even though we enable ICMP inspection in ASA Firewall, Lower to Higher security level is not allowed by default. Access-List is required on the Outside Interface of ASA to allow ICMP traffic.
Are you Planning to Deploy Cisco ASA Firewall for your Environment?
If you are planning for a Green-field Deployment, Tech Refresh, Migration from your legacy Firewall or any Firewall to Cisco ASA, or for implementing advanced features in your already deployed ASA Firewall. You can always reach out to us, the team at Zindagi Technologies consists of experts in the field of Network Security, Data Centre technologies, Enterprise & Service Provider Networks, Virtualization, Private Cloud, Public Cloud, Data Center Networks (LAN and SAN), Collaboration, Wireless, Surveillance, Openstack, ACI, storage and security technologies with over a 20 years of combined industry experience in planning, designing, implementing and optimizing complex Network Security and VPN deployments. We will be glad to help you. You can give us a call at +919773973971 or you can also drop us an email.
Author
Harpreet Singh Batra
Consulting Engineer- Data Center and Network Security
