What Is Locator Identity Separation Protocol (LISP) In SD-Access?
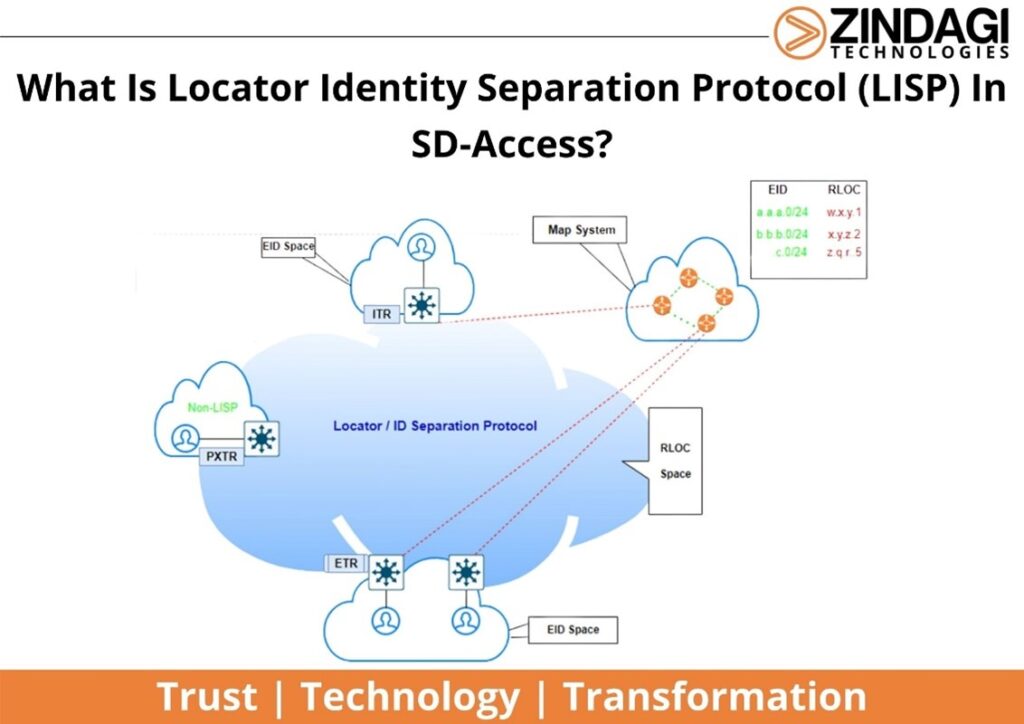
In this section, we will discuss the SD-Access control plane. You can also refer SD-WAN blog to learn about the workflow of SD-WAN. The SD-Access uses LISP or Locator Identity Separation Protocol as a control plane mechanism. LISP separates the location of a device from its identity by maintaining a database.
The following topics will be covered in this blog:
- LISP Mapping System
- LISP Approach
- LISP Terminologies.
- LISP Header
LISP Mapping System
The LISP mapping system uses MAP System (MS) & MAP Resolver (MR) as an analogy that we have in DNS.
– DNS resolves IP Addresses for queried Name
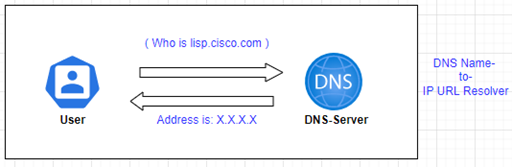
– LISP resolves Locations for queried Identities
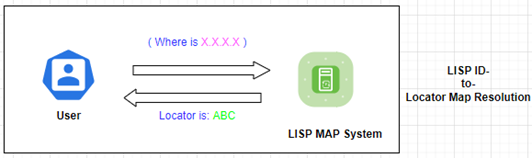
LISP Approach
Lisp namespaces
- EID (Endpoint identifier) is the IP address of a host.
- RLOC (Routing Locator) is the IP address of the LISP router of the host.
- EID-to-RLOC mapping is the distributed architecture that maps EIDs to RLOCs (routing locator)
The below diagram explains how LISP works:
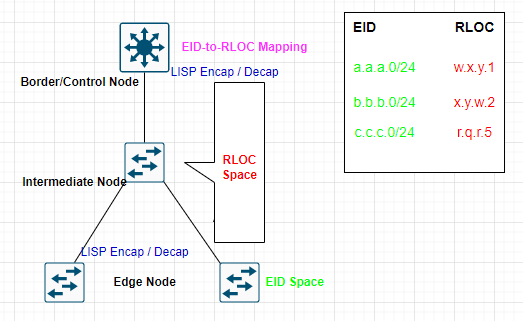
- The End client will be connected to the End Node.
- The end devices will be inside the End Point Identity (EID) Space.
- In between SD-Access Fabric, we have a collapsed Border & Control Node.
- In between the Edge node and Border node, we have an RLOC space that represents the location.
- In the mapping system (Control node), we will have EID to RLOC mapping. The main purpose of this mapping is that if the source user doesn’t know the destination, then you can do the query to the mapping system and this MAP server will send the response to the destination.
- The whole mechanism works as At the moment the End Points will get connected to the Edge device, they will send that entry to MAP Server so that Mapping Server knows that Endpoint to the Location shown in the above diagram.
Terminologies
Let us understand the terminologies used inside the LISP.
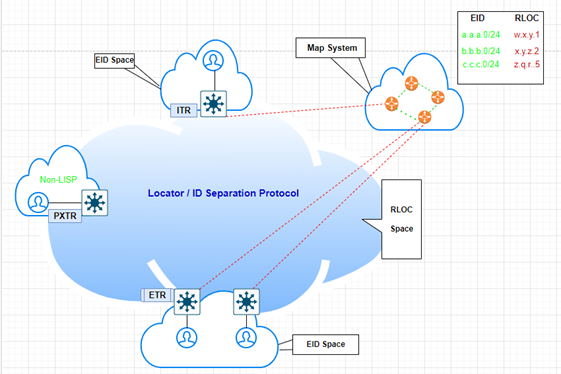
- EID: End-point Identity
- RLOC: Router Location
- ITR: Ingress Tunnel Router
- ETR: Egress Tunnel Router
- XTR: It represents both Ingress & Egress Tunnel Router.
- PXTR: Proxy Tunnel Router
- MS: Map System
- MR: Map Resolver
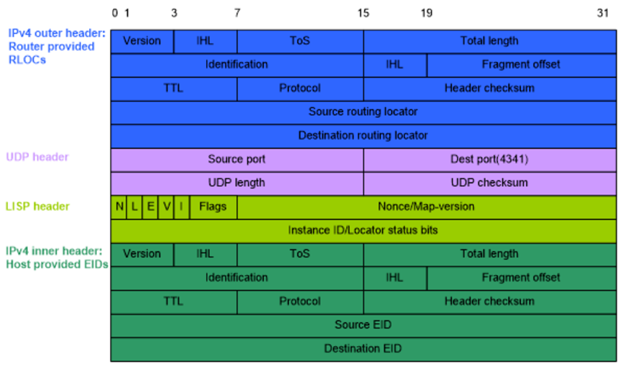
Header Format
The LISP contains five different bits:
- N (Nonce present bit)
- L (Locator status bit)
- E (Echo Nonce request bit)
- V (Map version bit)
- I (Instance ID bit)
Fig: LISP IPv4 Header Format
This article explains how the LISP control plane mechanism does work in SD-Access. We hope that while going through this article, you will be able to understand the basic workflow behind LISP in SDA fabric and how Endpoint Identity (EID) gets mapped to Routing Locator (RLOC).
In continuation of this blog, we will discuss how VXLAN works in the next blog for SD-Access where we will discuss the VXLAN protocol and its terminologies along with VXLAN Header.
Zindagi Technologies is a top IT consulting company in Delhi and has been serving the IT needs of organizations in the public and private sectors. We have successfully implemented many Data centres along with cybersecurity issues that are faced by many organizations. If you want to go through the list of clients then you can visit Zindagi’s website or contact us at +91-9773973971.
Author
Sani Singh
Consultant – Enterprise Networking

IS-IS domain used in ISP Domains | Zindagi Technologies
November 15, 2022[…] going to discuss the IS-IS protocol which is widely used in large ISP domains. You can also refer to the LISP understanding that is used in SD-Access as a control plane. The IS-IS protocol stands for “Intermediate System to Intermediate […]
Basic concepts of SD-Access | Zindagi Technologies
December 19, 2022[…] this blog, we are going to discuss SD-Access Wireless. You can also refer to the LISP understanding that is used in SD-Access as a control plane. The SD-Access Wireless […]