14 Ways To Know If You Are Following Best Cyber Security Practices Or Not? (Part -1)
It is an unspoken rule that if you are running an organization then you have to take care of cybersecurity. This is the foremost smart step towards the security of your hard work and following the best cybersecurity practices is a must. Seeing the situation now that the world is going through; most of the big organizations are facing cyber-attacks and they have increased in the past couple of years.
Being an SMB if you think you are safe from cyberattacks then you are on the wrong side. According to the statistics if you are a small business then you come under 43% of the aimed cyberattacks on SMBs.
Here are 14 cybersecurity best practices that are much needed by your business to keep an eye on breaches and attacks in the future. Being one of the best cyber security Service providers in Delhi, we take care of all the components of cybersecurity. We will be discussing 7 in this blog and the next 7 in the next blog.
Best Cyber Security Practices
Having A Strong Password Policy
As a cyber security Services company in Delhi, we strongly recommend that you have a password policy. Now if we say that does all your employees have passwords, you will say, “Of course, what kind of a question is this, we have very elaborated passwords that are difficult to guess”. Generally, people keep passwords that they can easily remember, like first name, parent’s name combined with the date of birth, or a pet’s name. Instead of letting people have their own passwords, it is important to implement password generation applications and to ensure that all password policies’ best practices are being followed.
Using The Right Security Software

An employee got a mail saying that they have won a lottery, or their number has won a prize, and seeing this, they click the link. In actuality, the link contains a virus that is now embedded in the system to keep an eye on all the sensitive information that is being accessed on that computer. Even if you close the doors and windows of your house to keep the thieves at bay, the mosquitos will still be able to get in through the hinges and cracks. This is how exactly the malware enters your system.
Getting The Patch Management Process To Work
What do you understand by patching? When a cloth gets torn then our mother used to patch it up by using a piece of cloth a try to make it usable. In a similar way, patch management means fixing software and vulnerabilities that will ensure a smooth-running process. In short patch management is very time-consuming and if they are not fixed on time then the system might break. Having proper patch management will help in keeping a log of all the previous patches and will form a routine that no patch is missed, keep in mind that we are able to do it for you.
A Run Of Nightly Backups

So as the implementation of our new site was still in process, one of the CSS files got permanently deleted and there was no way to recall it. Luckily, we have been following a nightly backup routine and our site data was restored as the last time it was. Being a managed cybersecurity services provider company in Delhi, this is one of the routine tasks. Not every organization is capable of taking backup of their data and they need a managed cyber security provider to fulfill this service. We can automate the backup process for you.
Multifactor Authentication Service
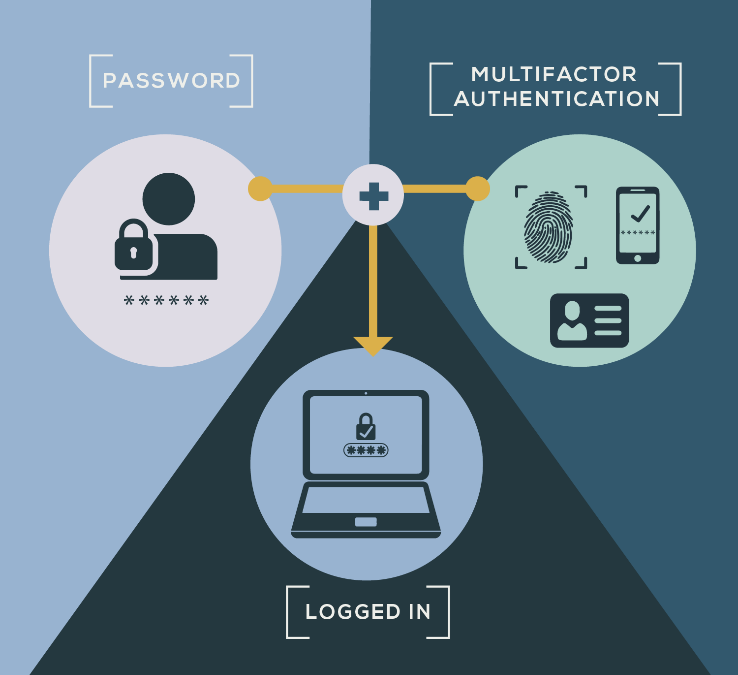
The two-factor authentication is something that we have all have seen in our emails and the processes we use. This means that the authentication process has two steps clearing which, the access would be granted. But in multilevel authentication, the user will have multiple levels of security options like a password, pin, OTP sent on the mail or phone number, or a biometric identifier like the retina, fingerprint, or voice verification. This will help in providing more security for your organization.
Phishing Awareness Program

“YOU HAVE WON A CAR ON YOUR XXXXXXX.XXX CARD” these words are enough to have your attention and the obnoxious amount of money displayed in the email will give birth to greed. This is just an example of luring the user into a phishing scam, there could be fake SMS, WhatsApp messages, travel emails, and many more things. Training your employees is one of the many things you can do. Educate them on how not to fall into the trap.
Get In Touch With The Top Cybersecurity Services Provider In Delhi and follow Best Cyber Security Practices.
Having the best cyber security team on board, we have the best cybersecurity consulting services in Delhi. We focus on the needs of customers and provide them with exactly what they need. You should get in touch with us through email or by dropping us a message at +91-9773973971 if you want to full-proof the cybersecurity aspect of your organization.
Author
Shweta
Senior Executive, S&M.

14 Best Cybersecurity Practices | Zindagi Technologies
June 8, 2022[…] In our previous blog, we were explaining the 14 ways your small business is following cybersecurity best practices. We have already discussed 7 and in this blog, we will be discussing the remaining 7 practices. […]