7 Easy steps to Configure site-to-site IPsec VPN using IKEV1 on Cisco ASA
What is IPsec?
IPsec VPN (internet protocol security) is a protocol or method to encrypt the traffic between two branches or sites. It is used to secure the traffic over an untrusted network, and we can understand by its name that it provides security of INSIDE network IPs.
It provides Confidentiality, Integrity, and Authentication over the network.
What is VPN?
It stands for Virtual Private Network. it is used to connect two private networks of different locations or sites over in a public network. It implements by IPsec for connecting two sites.
What is IKE (IKEV1 and IKEV2)?
It stands for Internet Key Exchange. IKE is a protocol that is used to set up the keys for negotiating the IPsec VPN. IPsec uses IKE for creating a virtual tunnel between two sites
IKE has 2 versions. We will use IKEV1 for IPSEC VPN.
The Process to Configure site-to-site IPsec VPN
We have two branches (Branch 1 and Branch 2) and we have to protect traffic over the ISP of branches.
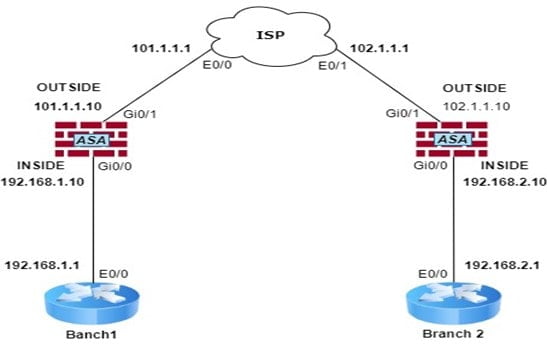
Configuration on Branch1 ASA (firewall):-
Step 1:- Create Crypto Ikev1 Policy
- In this step, we will configure the HAGLE information.
- Hash, authentication, group, encryption must be the same on both sides.
ASA1(config)# crypto ikev1 policy 10
ASA1(config-ikev1-policy)# hash sha
ASA1(config-ikev1-policy)# authentication pre-share
ASA1(config-ikev1-policy)# group 2
ASA1(config-ikev1-policy)# lifetime 86400
ASA1(config-ikev1-policy)# encryption 3des
Step 2:- Create A Tunnel-Group To Specify A Pre-Shared Key For Peer.
- The pre-shared key should be the same on both sides
- To create a tunnel group, there are two steps :
- Create tunnel-group
ASA1(config)# tunnel-group 102.1.1.10 type IPsec-l2l
- Specify pre-shared key in tunnel-group
ASA1(config)# tunnel-group 102.1.1.10 IPsec-attributes
ASA1(config-tunnel-ipsec)# ikev1 pre-shared-key cisco
Step 3:- Create IPsec Transform-Set
ASA1(config)# crypto ipsec ikev1 transform-set TSET esp-3des esp-sha-hmac
Step 4:- Define Interesting Traffic ACCESS-LIST
- Traffic which we want to secure via VPN that is Interesting traffic (192.168.1.1 and 192.168.2.1)
ASA1(config)# access-list VPN-ACL permit Ip host 192.168.1.1 host 192.168.2.1
Step 5:- Create A Crypto Map
- It is used to create a particular list of VPN ACCESS-LIST, TRANSFORM-SET, and PEER IP.
ASA1(config)# crypto map CMAP 10 set peer 102.1.1.10
ASA1(config)# crypto map CMAP 10 set ikev1 transform-set TSET
ASA1(config)# crypto map CMAP 10 match address VPN-ACL
Step 6:- Enable IKEV1 And Apply Crypto Map On The Interface
ASA1(config)# crypto map CMAP interface outside
ASA1(config)# crypto ikev1 enable outside
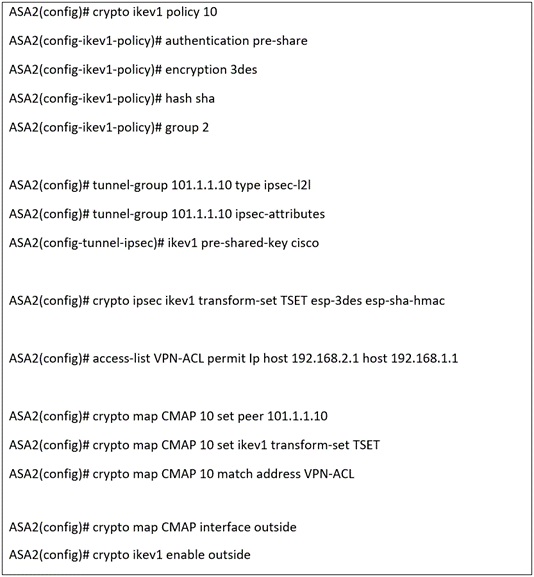
Step 7:- Apply Same Steps For Branch 2 ASA Device
- Ip addresses will not same. Make sure to use the correct IP addresses for Branch2 ASA.
The complete configuration of Branch2 ASA is here.
Zindagi Technologies has proven of an expert in the field of configuring Remote VPN, Site to Site VPN, Plain GRE, or MPLS VPN, VPN deployments. If you want to use VPN on your sites and to provide remote services to your users then you can avail of this service from us. Not just this, but there are many more services like data center services, cloud solutions, managed IT services, IT Consultant, Network infrastructure, cryptography, AI, IT security, and cyber security. We are the top IT consulting company in Delhi and you can contact us. We have our doors open to receive any solution requirements. You can reach out to us at +919773973971.
Author
Vijay Kumar
Associate Consultant

jatin hirdyani
January 28, 2022u r so nicely going to ur work congrats 💓
Cisco-Lord123
June 29, 2023Nice Guide! Direct to the point! keep up the good work!
Tobias Ndlovu
July 16, 2023You are the best🙏 thank you so much
Sandeep Balayan
August 8, 2023NONAT or UNAT is not configured here . IPSEC tunnel traffic should not be Natted so we need to specify this issue .