How Active-Active Failover works on CISCO ASA
What is meant by a Fail-Over? How does it works on Cisco ASA?
The meaning of the word “Fail-Over” is a procedure by which a system automatically transfers control to a duplicate system when it detects a fault or failure. In this blog, we will learn how Active-Active Failover works on Cisco ASA.
So, when an ASA {Adaptive Security Appliance} due to any reason FAIL, our Deployed System detects this Fault and then transfers the control to the backup ASA.
In simple terms, Failover is a procedure when an ASA fails another backup ASA handles the system.
Why do we need to configure the Fail-Over?
High-Availability: Using Failover we can ensure that if Primary / Active. ASA fails after that too System Continuously works by transferring the Control to Backup / Standby ASA.
Device Redundancy: One Firewall actively working while Backup Firewall sits passively and periodically checks the Active Firewall and if you don’t want that your device sits passively, or you can deploy Active / Active Fail-Over.
Active / Active Fail-Over – Cisco ASA
- It is a modified approach to failover that uses equipment more efficiently as both devices forward the data traffic.
- Using this we segment the Network /System that we want to secure into two halves and each half is handled by one ASA while providing redundancy to the other half.
- Active/Active Failover is defined by having two pieces of equipment inactive status for one portion of the network and in standby for the other portion.
In short,
- In this both ASA are in ACTIVE State.
- LOAD-BALANCING.
- It is supported by Multiple Mode only. For more details on Contexts, Single and Multiple modes refer to the Article à types of Contexts
- Configuration is always done in PRIMARY Unit.
For overall Failover Configuration refer to this USER GUIDE provided by CISCO ADMIN Guide
Pre-requisites of Active/Active Fail-Over:
- Both Units must be IDENTICAL i.e.,
- Same Model,
- Same RAM,
- Same Software Version,
- The same number of Interfaces
- Same Firewall Context.
- ASA must be in Multiple Modes.
Failover Group
- It is a Logical Group of one or more Security Contexts.
- One Group is Active in Primary ASA and the other Group is Active in Secondary ASA.
- Failover occurs at a Group Level and it supports both Stateless and Stateful Failover.
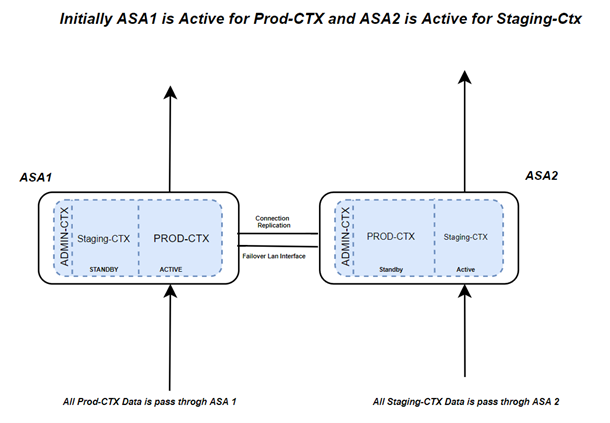
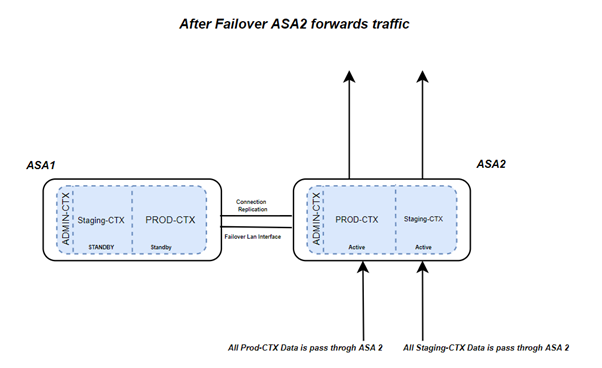
Failover Monitoring
To monitor the ASA which is in Failover, CISCO provides Monitoring at Device as well as Interface level
- Unit Health Monitoring
- Interface Health Monitoring
Unit Health Monitoring
- Devices will Monitor connectivity from the Failover interface by sending Periodic Hello Message.
- Each LAN Interface sends Hello Message after 1 sec
- If the device stops receiving Hello Message then it does not Trigger a Failover.
Interface Health Monitoring
- Monitoring device from DATA Interface.
- By default, ASA sends Periodic Hello Message after every 5 Seconds from its DATA Interface.
Test Performs under IHM
- Link UP/DOWN Test: A test of interface status. If it indicates that the interface is OPTIONAL then ASA performs further tests.
- Network Activity Test: Unit counts all received packets for up to 5 Seconds. If any packets are received at any time during this interval the interface is considered operational and testing stops. If no traffic is received ASA further performs the TEST.
- ARP Test:
- A reading of the UNIT ARP CACHE for the 2 most recently acquired entries.
- The unit sends ARP Requests to those ARP Entries.
- After each request, the UNIT Counts all received traffic for up to 5 seconds. If traffic is received the interface is considered operational.
- If no traffic is received then ASA performs further testing
- Ping Test:
- It consists of sending out a Broadcast PING Request.
- The unit then counts all received packets FOR UPTO 5 SECONDS
If all these tests fail for an Interface, but the SAME INTERFACE on the other UNIT continues to pass all the tests, then Interface is considered to be failed.
Are you looking to get High-Availability to your Network Infrastructure?
If you are thinking to provide High-Availability to your Deployed Network or want to deploy CISCO ASA or any other CISCO Product with its full functionality or maybe you want to implement advance features, you can always get in touch with the team at Zindagi Technologies consists of experts in the field Data Centre, cloud solutions, Virtualization & Cloud Services, Collaboration, Wireless device Deployments, Network Infrastructure, IT security, Managed IT and many more technologies. We will be glad to provide you with our Services, give us a call at +919773973971.
Author
Shivam Choudhary
Associate Consultant
