How does IPsec work with IKEv2 and establish a secure tunnel between two sites?
As a Network Security Engineer, this is our responsibility to secure your organization’s data over the internet. Our goal is to give you detailed information about How your data would be protected over the internet and Which protocols and Frameworks will be used to protect your data. We already discussed IKev1 working with IPsec. In this blog, we will learn about the IPSEC Site to Site VPN with IKEv2 and how it works.
What is IPsec Site to Site VPN?
IPsec is a protocol suite, or we can say a Framework that is used to provide a secure tunnel between two sites along with confidentiality, Integrity, and Authenticity. For E.g. There are two sites that are in different regions and their LAN users want to communicate with each other. As we know Private IPs are not routable on the internet. That’s where IPsec helps us to communicate to two different sites’ private networks over the internet with confidentiality, integrity, and authentication.
What is IKE (Internet Key Exchange)?
The IKE (Internet Key Exchange) is a standard that is used by the ISAKAMP protocol for negotiating the parameters. It works with IPsec that is used to set up encrypted, authenticated communication tunnels between two IPsec peer devices.
There are two versions of IKE: –
IKEv2 Phases
Like IKEv1, IKEv2 also has a two-phase negotiation process to create a secure tunnel. The first phase of IKEv2 is IKE_SA_INIT and the second phase of IKEv2 is IKE_AUTH.
Phase 1 Messages
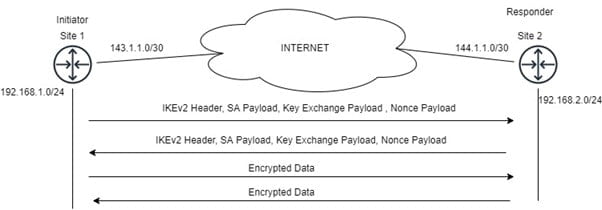
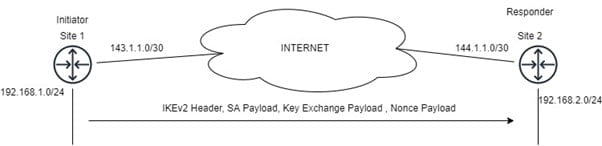
- IKE_SA_INIT_Request: – The first message is sent from Initiator to a responder. This message is used to negotiate the encryption and hashing algorithm in Security Association Payload and Public Parameter of Diffie Hellman in Key Exchange Payload and Nonce Payload.
- IKE_SA_INIT_Response: – The second message is sent from the responder to an initiator. In this message, the responder sends an agreed cipher suite and its own Diffie Hellman Parameter and Nonce Parameter.
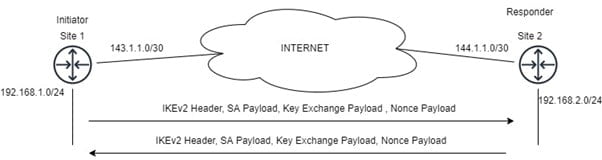
After Message 2 Phase 1 tunnel negotiation is completed and both IPsec peers generate a SKEYSEED which is used to derive the keys in IKE_SA.
Phase 2 Messages
The 3rd message of IKEv2 phase 2 (IKE_AUTH_Request) and the 4th message of IKEv2 (IKE_AUTH_Response) are encrypted and authenticated over the Phase 1 tunnel created by the previous message 1 and 2. In those messages, Phase 2 negotiation is done and both IPsec peers authenticate each other. In Phase 2 negotiation both devices negotiate which IPsec protocol (ESP or AH) is used to encrypt the Data Plane Traffic.

After Phase 2 secure tunnel is created which is used to forward data plane traffic in encrypted format over the internet. We hope this blog is useful to you to understand how ikev2 works with IPsec site-to-site VPN.
If you are planning implementation or migration from your plane GRE VPN and implement IPsec Solution in your organization. You can always reach out to us. We are providing Implementing Security Solutions, Data Center networks (LAN and SAN), Collaboration, Wireless Solutions, Virtualization, Private Clouds, Public Cloud Solutions. We have a certified technical team for implementing, migrating, and designing networks. To contact us, you can give us a call at +91 9773973971.
Author
Shivang Trivedi
Associate Consultant

ApurbDutta
February 1, 2022Well done Mr. Shivang Trivedi.
Deepanshu
February 1, 2022Informative 👌
Deepanshu
February 1, 2022Informative
Hilary Badder
October 5, 2022Spot on with this write-up, I actually believe this amazing site needs far more attention. I’ll probably be returning to read through more, thanks for the information!