How to Prevent Network from Compromised Endpoints using Cisco ISE: ANC?
Hello friends! We have already introduced many blogs on Cisco Identity Service Engine (ISE), in which we already covered multiple topics. If you have not checked those ones, then we recommend you check those blogs. The list of Cisco ISE blogs is mentioned below, you can go through it as per your learning plan.
- A Brief Introduction of Cisco ISE
- Cisco ISE: Device Administration and Network Access
- Cisco ISE- The Access policy platform for an Enterprise
- Cisco ISE: Ver2.7 Licenses Vs Ver3.0 Licenses
- Guest Access with Cisco ISE
- How to Configure Profiling and Posturing in Cisco ISE
Now, let’s come to the main topic, for which you are here. CISCO ISE has a very interesting feature which is called Adaptive Network Control (ANC).
As I told you that ANC (Adaptive Network Control) is a feature of the Cisco Identity Service Engine that can be used to monitor and control the endpoints. “Endpoints must be authenticated by Cisco ISE”.
Now, the main question is – How can we use ANC (Adaptive Network Control)?
You can quarantine an endpoint by restricting the access using dACL (downloadable Access Control List) or you can administratively shutdown the Switch Interface remotely via ISE (Identity Service Engine) itself.
As we know that, CISCO ISE can perform multiple tasks automatically by just creating the policies as per the requirements. With respect to this ability, many people are confused that ANC also works like this, but it is not. The administrator must trigger the ANC policy manually.
Cisco ISE Configuration
- Adaptive Network Control –
- Login to Cisco ISE (GUI)
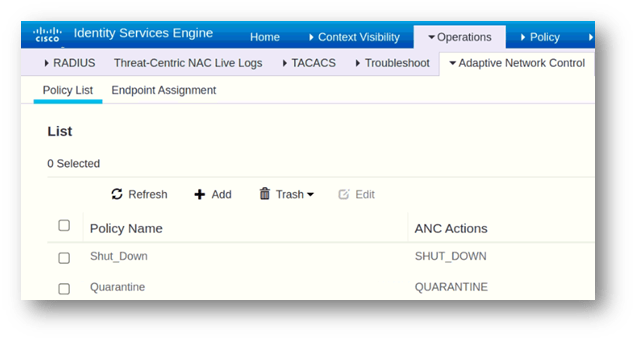
- Navigate to Operations > Adaptive Network Control > Policy List
- Click Add – You can add the Policy as per the below table

Click Save
Authorization Profile
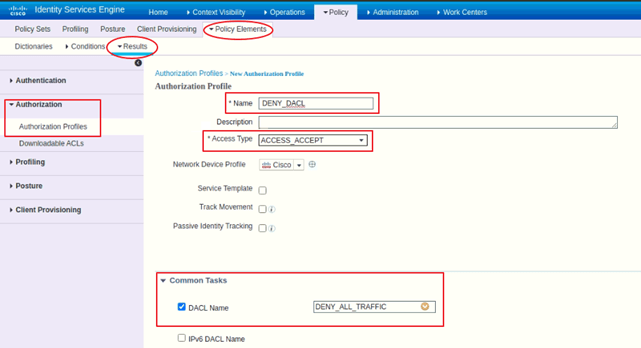
- Navigate to Policy > Policy Elements
- Results > Authorization > Authorization Profiles
- Click Add
- Give any Name e.g., DENY_DACL
- In Common Tasks, Check ‘DACL NAME’ box and from the drop-down, select the default DACL DENY_ALL_TRAFFIC
- Click Submit
Authorization Policy
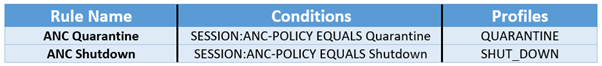
- Navigate to Policy > Policy Sets
- Click on the existing Policy to modify the same
- Under the Authorization Policy tab, you will find Global Exceptions
- Create a new rule in Global Exception. Example: Please check the below-mentioned table
Verification and Testing
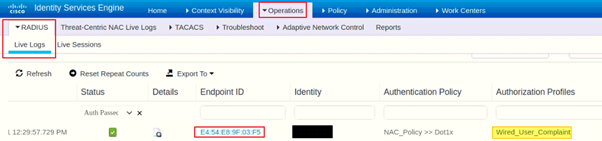
- Login to a computer as a user, authenticate yourself by entering your credentials
- Login to ISE (GUI), navigate to ISE RADIUS live logs to confirm the authentication of the user
- Login to the CLI of the switch
- Run the command “show authentication session interface <interface name> details” without quotes.
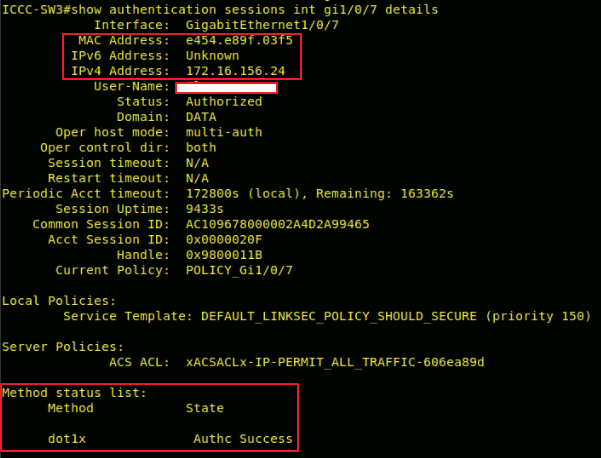
- Now, go to your ISE (Identity Service Engine) device > Login (if asks)
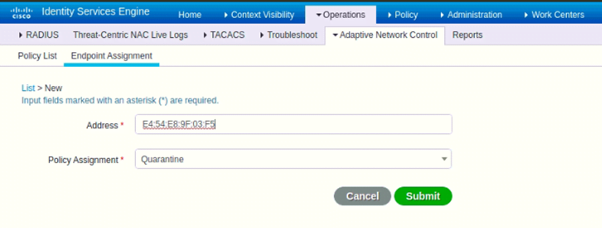
- Go to Operations > Adaptive Network Control > Endpoint Assignment
- Click Add
- Enter the MAC address of the workstation/endpoint, we already checked that from where we can get the MAC address. Please see above.
- In Policy Assignment – Select any policy as per your requirement
- Click Submit
Post assignment of the ANC policy, you will see multiple logs in the switch, the MAC address has been re-authorized and the DACL “DENY_ALL_TRAFFIC” has been applied.
As a revision, the default DACL has been called in the Authorization profile and that profile was configured in Authorization Policy – Global Exception.
Now, if you want to revoke the policy then it is also a very easy method. Follow the below steps: –
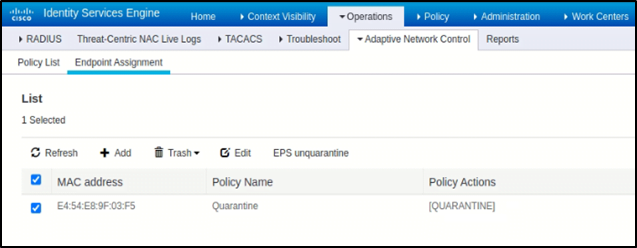
- Navigate to Operations > Adaptive Network Control > Endpoint Assignment
- Check the box of the MAC Address of the endpoint for which you want to remove the ANC policy.
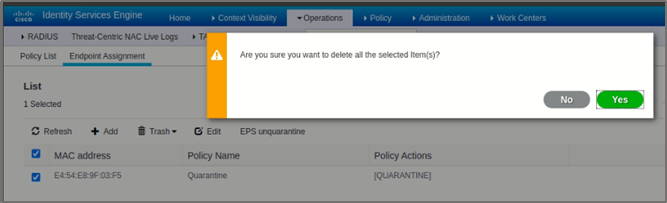
- Click Trash > Selected
- Click Yes
You can see the logs or messages in Switch (NAD), COA (Change of Authorization) was successful, and the workstation/Endpoint is successfully authenticated and authorized.
This can be also verified by checking Identity Service Engine (ISE) RADIUS live logs, you can find every detail related to the authentication and authorization.
RADIUS live logs also help in troubleshooting because it gives you whole packet exchange information.
It is great! We again learned about a very crucial feature of Cisco ISE in very simple steps. As discussed above, the ANC is a manual process and how can we create the “Quarantine” and “Shutdown” ANC policy for compromised and Non-Compliant Endpoints.
You can also go through other blogs and my blogs on Security components (WSA and FortiGate) blogs and Beginner and Advance Home Security.
We at Zindagi Technologies implements security, Network, Server devices, and much more, plans the architecture of the network, and provide full KT with all the documents. If you need any assistance, then you can directly contact us or call us at +91-9773973971.
Author
Jagjeet Singh
Senior Network Security Consultant
