CISCO ISE -The Access Policy Platform for an Enterprise
CISCO ISE Introduction: CISCO Identity Services Engine is a prominent NAC and identity grounded solution from cisco which provides a solution to streamline security policy management, reduce operating costs, and dispenses a single network access policy plan all over the organization amalgamating multiple services.
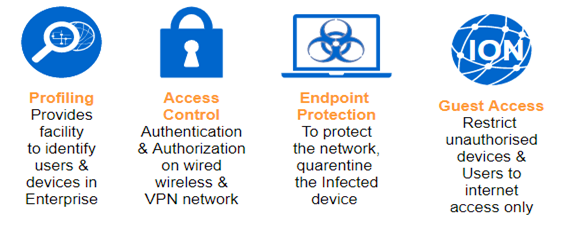
It is a type of policy platform that permits you to provide highly secure network access to users and devices, counting various authentication and accounting, web authentication, posture, profiling, device-onboarding, guest services, and VPN access into a single identity-based platform.
Today Network Is Not The Similar
In today’s scenario more devices, more users, more traffic, and more complexity. Going by the numbers, Network complexity makes it harder to see who (user) and what (device type) is on your network.

How To Use The Network With So Many Unknowns?
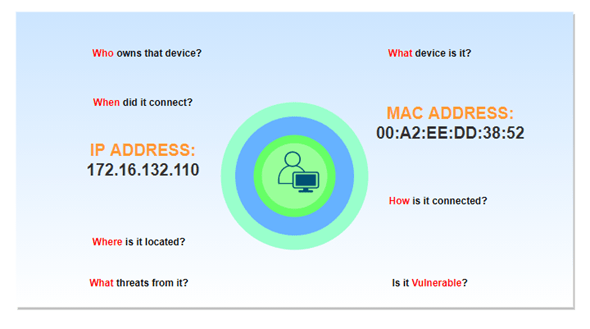
Without an NAC solution, there are many unknowns in the network. We do not have information about who & when accessed our network. We do not know if it is vulnerable or not. We do not have any update of his location, what device he is using to access the network, and connection type (wired, wireless, or VPN) to access the network.
Business Outcomes Of ISE In The Enterprise
Asset Visibility – Who is using, what device are they using when connecting to a network, and which operating systems are supported? By the information of devices/users are coming and going, it provides visibility over time.
ISE provides visibility with the help of profiling, AnyConnect. The profiling service in Cisco ISE identifies the devices that connect to your network. AnyConnect provides the Application visibility.
| Poor context-awareness without ISE | Rich context awareness with ISE | |
| IP ADDRESS: 172.16.121.10 | WHO | Chakransh (Employee) |
| UNKNOWN | WHAT | Apple iPhone XR/iOS/14.4.2 |
| UNKNOWN | WHEN | 11:00 AM IST |
| UNKNOWN | WHERE | Floor-3, Bakshi House, New Delhi |
| UNKNOWN | HOW | Wired |
| UNKNOWN | APPS | Firefox, AnyConnect |
| UNKNOWN | SPEC | Serial number, CPU, RAM |
Access to any device/user  | RESULT | Authorized network access |
Access Control – Control through the ISE for wired, wireless, and VPN users and devices by policy enforcement, ensures that only authentic and authorize users and devices can connect to the network. By the access control, we can achieve the below-mentioned points
- Secure access from any location regardless of connection type.
- Apply access and usage policies across the entire network.
- Monitor access, activity, and compliance of non-corporate assets.
Cisco ISE provides a “Posturing” feature. With the help of posture compliance, we can check that endpoint should have required files, patches. Antivirus and defenders should be enabled. If any other endpoint solution we have then it should be present on the client machine. Any client should not get network access without a compliance check. If any user is non-compliant then it should be remediated and after taking the necessary action it can get the network access.
Guest Access
Guest access is when we invite someone to use our network, who is not part of our domain/team. If any guest user tries to access the network, then he/she will be redirected to ISE. To log in apart from Provide Credentials, the user clicks Register for Guest Access.
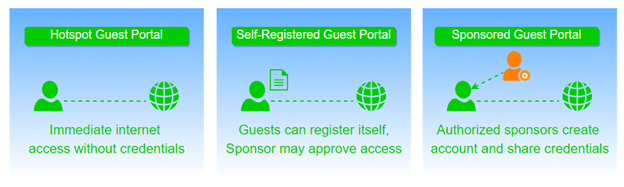
The user gets the page where he/she can create the account. We can limit the self-registration privilege to people by creating and sharing a secret registration code. After creating the account, the user can log in with newly created credentials (username and password).
With This, We Conclude
- Profiling: Identity of a device on the network & Quantify the risk.
- Authentication: User and end device attribution &Identification of endpoints on Wireless/Wired connections.
- Posture: Device security posture identification & Allows for better policy & security decisions.
- Enforcement: Ability to enforce policy decisions based on context. Untrusted devices have restricted access.
With this blog, you will be able to understand the features of CISCO ISE and tracking capabilities of any unknown resource. This will in turn help you in managing your network and you will be able to keep a close eye on the time and other related details of the users.
We hope that this blog post has answered some of your questions related to CISCO ISE. We at Zindagi Technologies have a team of capable engineers that will help you in the deployment of CISCO ISE. For more details, we are available for you, give us a call on +91 9773973971 or reach us at Zindagi Technologies.
Author
Chakransh Awasthi
Senior Network Security Consultant
